Lecture
The SSL (Secure Sockets Layer Protocol, Secure Sockets Protocol) cryptographic protocol was developed by Netscape in 1996. It can be placed in a multi-layered protocol model between a protocol that provides a reliable connection (for example, TCP) and an application layer (for example, HTTP). It provides a secure channel between clients and server, providing the possibility of mutual authentication, using digital signatures to ensure integrity and encryption for confidentiality. This protocol is integrated into most browsers and web servers and uses an asymmetric public-key cryptosystem developed by RSA.
The protocol allows the choice of using various algorithms for encryption, hashing, and digital signature. This allows you to choose an algorithm based on legal, export or other restrictions, as well as allows the protocol to take advantage of new algorithms. The choice is consistent between the client and the server at the session setup stage.
There are several versions of the SSL protocol.
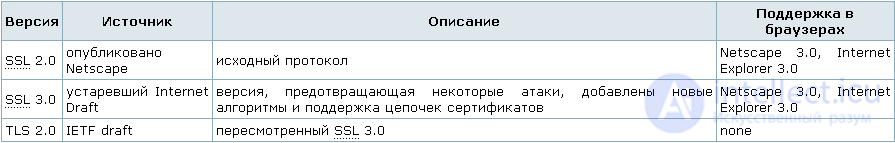
The Internet Engineering Task Force (IETF), the Internet Engineering Task Force, is working on a TLS (Transaction Layer Security) protocol for transport layer security.
SSL provides secure communication by combining the following two elements:
Authentication
A digital certificate is tied to a specific Internet domain, and the certification authority carries out checks that confirm the authenticity of the organization, and then creates and signs a digital certificate for that organization. Such a certificate should be installed only on the domain of the web server, the share of which it has been authenticated, which gives the Internet users the necessary guarantees.
Encryption
Encryption is the process of transforming information into a form that is unreadable for everyone except for a specific recipient. It is based on the necessary for e-commerce guarantees of confidentiality of information transfer and the impossibility of its falsification.
Detailed description of the certificate
To see the details of the SSL certificate of the website, double-click on the closed lock that appears at the bottom of the page in the status bar.
This is a digital certificate for IE 6.0 browser:
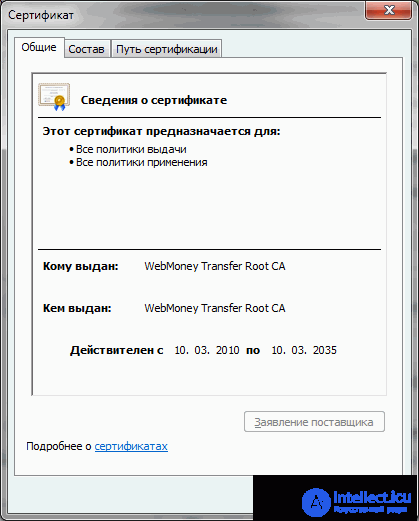
The SSL certificate of the web server allows visitors to your site to see the following information (detailed information about the certificate is presented on the “Composition” tab):
* Internet domain for which this certificate is issued. This information allows you to verify that the given SSL certificate for the web server was issued specifically for your host and domain (http://www.mydomain.com/).
* Certificate holder. This information is an additional guarantee, since the visitor can see the name of the person with whom he does business.
* The city where the company owning the certificate is registered. This information once again convinces the visitor that he is dealing with a real organization.
* Validity of the certificate. This information is especially important because it shows the user that your digital certificate is valid.
Web browser security warnings.
Your web browser has built-in security. If you are trying to access a website that has problems with a certificate, this security system may issue, for example, such a warning.
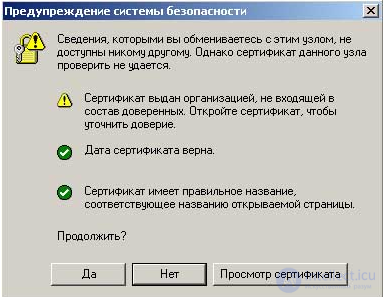
In this example, the warning states that the site you are logged on actually uses a secure protocol, but no third party can guarantee that you are working on the web server of the company you want to deal with and that your information will not be received by someone else.
When visiting a website with a valid certificate, the user will be informed that this site has a digital certificate from a certification authority, such as thawte, and all data that the user provides to this site will be encrypted. By checking the certificate, the client can verify that the web site belongs to a real registered company, and that he is accessing the domain name that this company owns.
Protocol Overview
due to the multi-step connection setup procedure.
Session setup
Session setup begins with a handshake sequence between the client and the server. This sequence may depend on whether the server is configured to provide a certificate and whether it requires a certificate from the client. It is also possible that additional steps will be required to coordinate the parameters of the encryption algorithm. This document describes a typical scenario, and the remaining SSL features are not considered.
The handshake protocol is used by the client and server to:
1. Coordination of encryption parameters (Cipher Suite), which will be used during data transfer
2. Development and transfer of the session key between the client and the server
3. Optional authentication of the server by the client.
4. Optional client authentication by the server
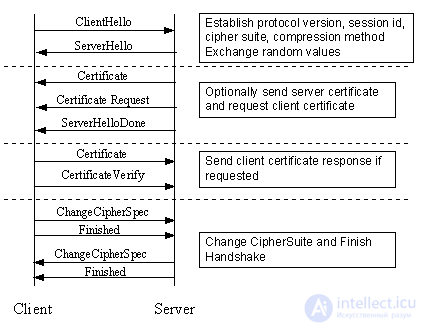
Fig. 1. Simplified Handshake Procedure
Coordination of a set of encryption parameters allows the client and server to choose such parameters that they both support. The SSL 3.0 specification defines 31 parameter sets. A set of encryption parameters consists of:
1. Key exchange methods
2. Symmetric encryption algorithm for data transmission
3. Hash functions for creating MAC (Message Authentication Code - message authenticity code)
The key exchange method determines how the client and server agree a common key for a symmetric encryption algorithm. The key exchange method is how the shared secret symmetric cryptography in SSL 2.0 for key exchange is used RSA. In SSL 3.0, you can choose between RSA, when using certificates, and the Diffie-Hellman key exchange method for exchanging keys without certificates and without previous communication between the client and the [Kaufman] server.
Choosing a key exchange method involves deciding whether or not to use digital signatures in key exchange, and which digital signature method to use. Signing with a private key protects a man in the middle (man-in-the-middle-attack) from attacks during the exchange of information used to generate a shared key.
SSL uses symmetric encryption algorithms to encrypt data during a session. There are 9 options, including the rejection of encryption:
1.No encryption
2. Stream encryption
RC4 with 40 bit key
RC4 with 128 bit key
Algorithms used in CBC mode
RC2 with 40 bit key
DES40, DES, 3DES_EDE.
Idea
Fortezza
CBC mode (Cipher Block Chaining), the previous encrypted block is used to encrypt the current block. DES - Data Encryption Standard, has many options (including DES40 and 3DES_EDE). Idea (one of the most robust algorithms) and RC2 are the property of RSA
The choice of the hash function determines how the hash of the data block will be generated. SSL supports:
No hashing
MD5, 128-bit hash
Secure Hash Algorithm (SHA), hash 160 bits
SHA was developed for use with DSS (Digital Signature Standard - Digital Signature Standard).
The handshake protocol provides many possibilities, but the most common sequence involves the exchange of certificates and key exchange using the Deffi-Hellman method. In other cases, the handshake order is different, as described in the SSL specification. The handshake sequence uses three protocols, SSL Handshake Protocol (SSL) to open a session between the client and the server, SSL Change Cipher Spec protocol to negotiate a set of crypto algorithms and their parameters, and the SSL Alert Protocol for the exchange error messages between the client and the server. These protocols are encapsulated in the SSL protocol (SSL Record Protocol) as application layer data. The encapsulated protocol is transmitted as data by the underlying protocol, which does not analyze this data. The encapsulated protocol does not know anything about the lower protocols.
Encapsulation of the control protocol into the recording protocol means that the re-negotiation of the session parameters will be performed over a secure channel. If there is no active session, then the zero set of encryption parameters is used, that is, prior to the session setup, no messages will be encrypted and their integrity will not be checked.
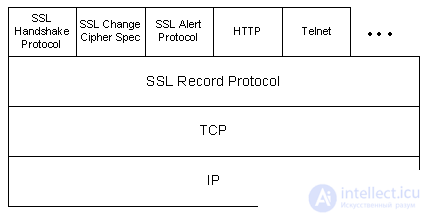
Fig. 2. SSL protocol stack
Data transfer
The SSL write protocol is used to transfer application-level data and SSL protocol control data, possibly breaking the data into smaller pieces or combining several messages from the upper layer in one block. Data compression is possible, then message authenticity codes (MAC) are calculated and the data is encrypted before transferring them using the underlying reliable transport protocol.
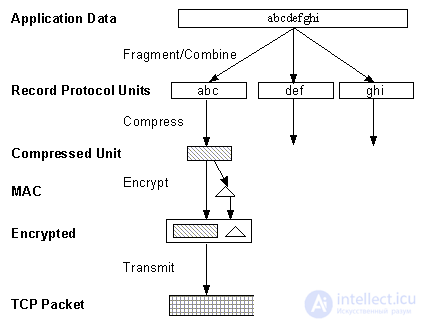
Fig. 3. SSL write protocol
SSL uses message hash functions and sequence numbers to compute message authentication codes (MAC, Message Authentication Code), which are encrypted to prevent replay attacks. Record protocol blocks, compressed blocks and encrypted blocks contain the identifier of the original protocol, the length of the message and the data.
Use SSL
One of the common uses for SSL is the protection of data transmitted over HTTP between a client and a web server. The secure URL begins with “https”, instead of “http”, and a different port is used (443 by default) / The browser stores client certificates and private keys, and shows a secure connection indicator when it is used.
Significance of SSL Authentication
"Spoofing" (compound imitation):
The relatively cheap services of web-designers and the ease with which existing pages can be copied, allow you to create illegal web-sites that look “officially” and look like an organization. In reality, it is a trap to illegally obtain confidential data.
Unauthorized actions:
A competitor or offended user can change your web site so that it gives false information or refuses to serve potential customers.
Unauthorized disclosure of information:
When transactions are carried out in clear text, a hacker can intercept them in order to obtain information that is important to your customers.
Data falsification:
The contents of the transaction can be intercepted and maliciously or accidentally changed during the transfer process. User names, credit card numbers and financial information transmitted in clear text are too vulnerable to outside interference.
SSL implementation
Although it is possible to write an SSL implementation from scratch to the specification, it is much easier to take one of the ready-made packages. Additionally, due to patents, some cryptographic libraries must be licensed, at least in the United States. The SSL libraries contain functions for encryption, computing hash functions, and tools for working with certificates. Each package must also contain a licensed module for working with public keys in the United States, since there is a patent for the use of public key cryptography.
RSARef The RSA sample implementation, unsupported library source code, can be used in free and non-commercial applications. Consensus Development Corp. sold licenses for commercial use, but now it is not so.
BSAFE 3.0 Commercial implementation of RSARef.
These packages for working with public keys include a complete set of asymmetric algorithms (including RSA and the Deffi-Hellman key exchange method), symmetric algorithms, and hash functions. They can be used in SSL implementations. The most famous libraries for working with SSL:
SSLPlus Commercial package with source package from Consensus Development Corp., improved SSLRef 3.0. To use you need BSAFE 3.0 (from RSA).
SSLava Implementation of SSL 3.0 in Java from Phaos Technology.
OpenSSL OpenSSL-0.9.4 (OpenSSL-0.9.4.tar.gz) is a free, non-commercial implementation of SSL 2.0 and SSL 3.0 and TLS 2.0. Includes the implementation of asymmetric algorithms that can be used outside the United States. In the States, due to patent restrictions, you must use RSARef or BSAFE3.0. SSLeay provides an inexpensive way to use SSL.
Comments
To leave a comment
Information security, Cryptographic ciphers
Terms: Information security, Cryptographic ciphers