Lecture
To ensure the confidentiality of information transmitted over the network, it is necessary to ensure its encryption on the sender's side and decryption on the recipient's side using one of the algorithms discussed in Chapter 2. There are several encryption tools that encrypt information at different levels of the OSI model. The easiest way is to encrypt information at the application level. In this case, only the directly transmitted information is encrypted; in this case, no service information from the network packet headers is encoded. An example of a program that performs this kind of encryption is PGP (Pretty Good Privacy). One of the main advantages of this program is that there are versions of PGP for almost all software platforms: DOS, Windows, Unix, Macintosh. PGP is a cryptosystem that allows you to encrypt data (the contents of files, the clipboard) in an asymmetric scheme, as well as generate digital signature for transmitted messages. PGP uses the following algorithms: RSA, SHA, DES, CAST, IDEA, DSS. Encoded information is saved as a file that can be transferred via any network method (email, FTP). For convenience, PGP can be integrated with email programs such as OutlookExpress, TheBat, Eudora. Another advantage of PGP is that there are freeware versions of this program, which can be found at http://www.pgpru.com
The use of PGP and the like can be inconvenient due to the need for the user to take steps to encrypt messages. In order to make the encryption procedure transparent to the user, there are various network protocols that implement secure connection technologies. Consider one of these protocols - the SSL (Secure Socket Layer) protocol. SSL is designed by Netscape for its Netscape Navigator browser to ensure the confidentiality of the exchange between the two client and server application processes. It also provides server authentication and, optionally, client authentication. SSL works at the representative OSI model level over TCP.
The advantage of SSL is that it is independent of the application protocol. Application protocols such as HTTP, FTP, TELNET, and others can work on top of the SSL protocol completely transparently. SSL can negotiate an encryption algorithm and session key, as well as authenticate the server before the application accepts or transmits the first data byte. All protocol application data is transmitted encrypted with a guarantee of confidentiality. SSL provides a secure channel that has three main properties:
The SSL protocol uses the following cryptographic algorithms: DES, DSA, MD5, RC2, RC4. All modern browsers support SSL protocol. If the user enters the URL address starting with the abbreviation HTTPS, the HTTPS protocol starts to work, which is a standard HTTP protocol protected by SSL. In this case, the connection is made to the port number 443, which is usually used by default for HTTPS. After that, the browser and the server exchange packets, conducting mutual authentication according to their certificates, exchange session encryption keys, and begin exchanging information in an encrypted form (Fig. 5.1).
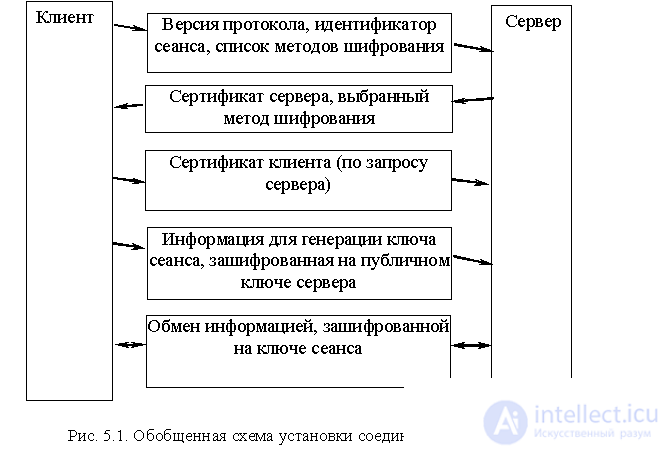
An alternative to using the SSL protocol can be the use of the Transport Layer Security (TLS) protocol, which has almost the same functionality.
To protect information at a lower — network — level, the OSI model uses Virtual Private Network (VPN) technology. VPN involves the use of cryptographic protection methods to ensure the confidentiality and integrity of information at the network level using a number of modern network layer protocols (IPSec, PPTP, L2TP, L2P) when transmitting information over public networks. Encryption is transparent to users by software or firmware. In this case, the data of all network packets, starting from the transport layer, are encrypted and placed in encoded form in the data region of the network layer packet. This forms a “tunnel” hidden from outsiders, through which information can be transmitted in a public access network between nodes of an imaginary, virtual network. Compared to the SSL protocol, VPN provides the ability to hide information such as port numbers used by an attacker, and when using the tunneling mechanism, use the IP addresses used in the local network, which makes it difficult to scan the network and find weaknesses in it.
There are three main VPN connection methods:
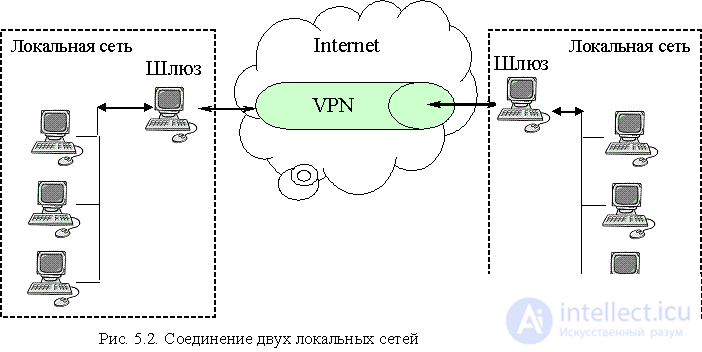
Consider one of the protocols through which the VPN technology is implemented. The IP Security Standard is a suite of protocols related to encryption, authentication, and security during transport of IP packets, which should be part of the IPv6 standard being developed. It includes 3 main protocols - Authentication Header (AH), Secure Content Hiding (ESP), and Internet Key Exchange (IKE). AH provides packet originator authentication and packet header integrity using hashing mechanisms. The ESP protocol provides verification of the integrity of a packet's datagram and encryption of information in it. It can operate in two modes: transport and tunnel. In transport mode, the ESP protocol protects packets (and data and headers) of higher-level protocols, the IP packet header is not protected. In tunnel mode, ESP provides communication between two LAN gateways, protecting the information in the IP packet header. In this mode, the IP packet is fully encoded and placed in the data region of the packet transmitted between the two gateways. At the receiving gateway, this packet is unpacked and sent to the addressee.
The IKE protocol is responsible for the connection setup procedure, when the parties agree on the cryptographic algorithms used, exchange session encryption keys. Protocols of the IPSec standard use such cryptographic algorithms as DES, TripleDES, AES, SHA, MD5.
In order to use VPN in practice, you can use hardware gateways (for example, CSP VPN Gate) through which communication with the external network takes place and which themselves implement all the VPN functions. For an end user, a simpler and cheaper solution may be to use a software implementation; for example, you can use the built-in IPSec support in Windows 2000 / XP
Comments
To leave a comment
Information security, Cryptography and cryptanalysis, Steganography and Stegoanalysis
Terms: Information security, Cryptography and cryptanalysis, Steganography and Stegoanalysis