Lecture
In March 2014, Google removed the ability to use Gmail over an unencrypted connection. This year, the company increased the security level by adding special icons that signal that the email provider of the correspondent does not support HTTPS.
The company from Mountain View does a lot (although not the fact that it is sufficient) to protect the information of its users from a third party. Nevertheless, the question of the security of user data from the company itself remains open.
Before the Snowden revelations, the article says, there was no evidence that a third party really existed. Some people may have been slightly worried about the ability of cloud services to view users' personal data, but few believed that this data was actually viewed. Now it has become clear to almost everyone that, at a minimum, the government is not averse to looking into your personal files.
This understanding was the impetus for a change in public consciousness. From doubts about the validity of end-to-end encryption, many have concluded that it is absolutely necessary.
End-to-end means that the keys necessary for encrypting and decrypting transmitted messages are stored exclusively in the correspondence participants. In other words, email and all attached files can pass through a dozen third-party servers, and still have a completely unreadable view, until they reach the specified recipient. And only the latter will be able to decrypt and read the message.
Full end-to-end encryption can be achieved using programs such as PGP. With PGP, users can generate public / private key pairs and use them for end-to-end connections. This method, however, requires quite wide technical awareness from users. It should not be forgotten that the encrypted PGP message by default contains information about the recipient's key id, thereby greatly reducing the level of anonymity.
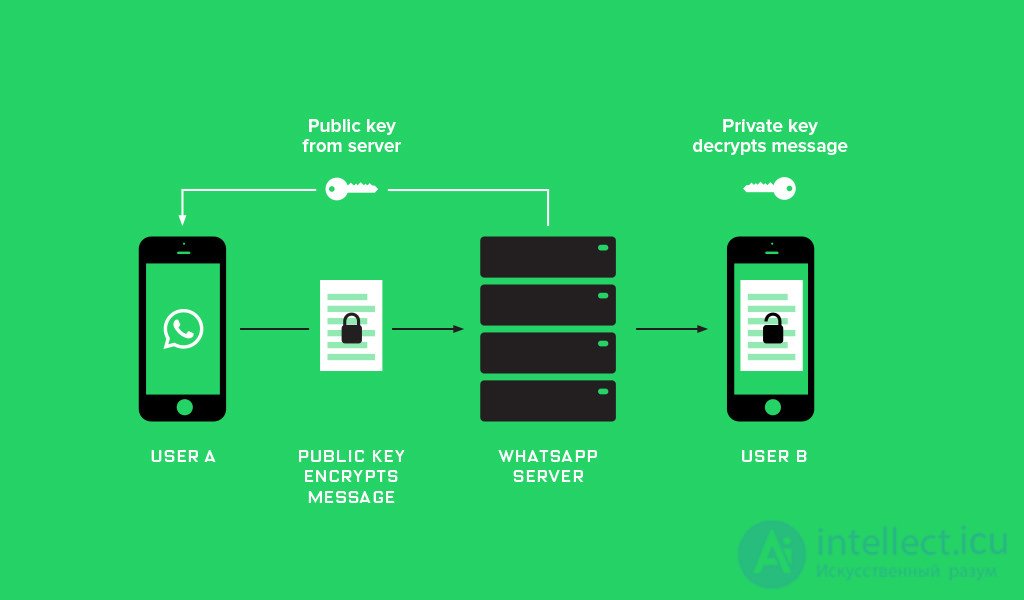
The system of data encryption of users WhatsApp (public key encryption). In order to send a message to user B, user A requests from the messenger server a public key for user B. Then user A uses this public key to encrypt the message. User B then uses a private key, available only on his device, to decrypt the received message.
Considering the situation from the point of view of companies, one should take into account the price they have to pay for using end-to-end encryption. This price is the impossibility of collecting data about its users. Microsoft is actively fighting the government of the United States for the right to notify its users about cases when security services have access to personal data. But such access would not be possible if Microsoft introduced end-to-end encryption for its services.
On the other hand, end-to-end encryption can be an extremely important requirement in the increasingly popular Internet of Things. In a world where every traffic light and every car is connected to the Internet, and smart phones know everything about their owners, authentication and encryption are vital.
The latest news from the camp of instant messengers allows you to optimistically look at the prospects for the widespread introduction of end-to-end encryption. WhatsApp has recently added this feature to its messenger. Viber and Google seem to be moving in the same direction. All this indicates that large companies have accepted the new conditions of the game.
And perhaps very soon, users will no longer hope that the services do not view their personal data. Services will simply not be able to view this data.
End-to-end is a system in which, encrypted information is transmitted from device to device directly, without intermediaries. The rules of the private key do not allow to decrypt the information to anyone except its recipient. Thus, the encryption and decryption of messages occur without the participation of the server. At the moment, the reliability of E2E cryptography is beyond doubt. However, every person who wants to use the services of this encryption should get acquainted with some of its shortcomings.
What happens to the encrypted data when the addressee’s device has notified the server about its receipt? In this case, the system can be programmed for two obvious actions:
Despite the fact that the second option may seem more reliable, these actions are equivalent. Anyway, the “hieroglyphs” stored in the server database cannot be decrypted (at least for now). That is why, paying attention to this information, the average user should be interested not in privacy, but in convenience.
Since all received messages, along with the keys for their decryption, are stored in the device’s memory, its loss or theft will lead to parting with all correspondence, which cannot be recovered. Thus, an ordinary user can permanently part with memorable dialogues or “top-secret” love poems.
Another conversation begins when it comes to large organizations implementing E2E correspondence by means of internal servers. If a digital key system is introduced in such a company, which a small group of people have access to, the recovery of lost information is not a difficult question. Such a decision will certainly require additional investments, but the matter of secrecy is worth it.
Imagine a classic one-on-one E2E correspondence. In this case, the device "A" and the device "B" are involved in the transfer of the message. Device "A" encrypts the data so that only device "B" can read them. This conversion does not use a lot of traffic, and happens "instantly."
Now imagine a conversation in a group dialogue. Suppose there are twenty people participating in the discussion of a topic. The device sender will have to encrypt the message for each device participating in the dialogue. In this case, twenty times.
Add to this the possibility of registering two or more devices on one account (for example: phone and tablet). The number of necessary encryption will grow even stronger. And so - for each message.
Such an exchange greatly increases the transmitted traffic. This can lead to slowdowns and slowdowns (which modern users hate so much), and may cause performance problems.
What is an integral part of all existing conversations unnerving users the most? Of course spam!
But spam is only a small part of the most interesting E2E problem. Most ordinary users, put the fight against unwanted messages on the shoulders of the system they use.
This system, implemented in all social networks, is engaged in tracking and eliminating unwanted messages. In order to understand which mailing is spam, and which is advertising for subscribers, the system must analyze (process) all transmitted traffic. In this analysis, and more precisely in its absence, is the main problem of E2E.
No matter how perfect the word processing system is, it will not be able to analyze encrypted messages. The absence of the classical system of separating messages sent to the "bad" and "good", opens the way for professional spammers and immature jokers.
This problem is not significant for users who are well versed in privacy settings. But it will become a burden for everyone else.
Users: When choosing "secure" applications for the implementation of their correspondence, you must carefully review all related problems.
Developers: The disadvantages described above are not critical, if the main goal of switching to the “safe” messenger is secrecy. However, users accustomed to the convenience of social networks can protest. Remember, you still have to preload when setting up a search engine, and this is quite a difficult task, given that the search is conducted on encrypted data. Look for exits. That is why when translating your application to the E2E encryption system, consider the needs of the target audience.
Comments
To leave a comment
Information security, Cryptographic ciphers
Terms: Information security, Cryptographic ciphers