Lecture
Rijndael is an iterative block cipher with variable block lengths and various key lengths. Key length and block length can be independently of each other.
Options
block size, bits 128, 192, 256 (1)
key size, bits 128, 192, 256
number of rounds 10, 12, 14 (2)
The size of the key element, bit 128, 192, 256 (equal to the size of the block)
number of key elements 11, 13, 15 (1 more than the number of rounds)
Features
Since the algorithm can be formulated in terms of just two operations — bitwise modulo-2 and indexed memory retrieval — performed on bytes, it can be effectively implemented on any computer platforms from lower-end microcontrollers to superprocessors. For the same reasons, and also because the architecture of the algorithm allows for a high degree of parallelism, it can also be very effectively implemented in hardware. In the end, it was the above factors, coupled with the high robustness of the algorithm, that predetermined his victory in the competition for a new standard.
The direct and inverse transformations in the cipher have the same algorithmic structure and differ in the shift constants, key elements, substitution nodes and multiplication constants. With hardware implementation, they can be combined by 60%; with software, optimal performance can only be achieved with completely separate implementations of both functions.
The cipher variant with a block size of 128 bits was adopted as the standard.
The number of encryption rounds is determined depending on the block size and key according to the following table:
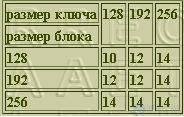
In other words, the maximum size is chosen from two sizes, and if it is 128 bits, then 10 rounds are used, if 192 bits, then 12, and if 256 - then 14 rounds of encryption.
Comments
To leave a comment
Information security, Cryptographic ciphers
Terms: Information security, Cryptographic ciphers