Lecture
Creator: Ron Rivest
Created: 1994
Published: 1994 year
Key size: 0-2040 bits (128 by default)
Block size: 32, 64, or 128 bits (64 by default for 32-bit platforms)
Rounds: 1-255 (12 by default)
Type: Feistel Network
RC5 ( Ron's Code 5 or Rivest's Cipher 5 ) is a block cipher developed by Ron Rivest of RSA Security Inc. with a variable number of rounds, block length and key length. This extends the scope and simplifies the transition to a stronger version of the algorithm.
There are several different versions of the algorithm in which the transformations in the “half-rounds” of the classic RC5 are slightly modified. The classical algorithm uses three primitive operations and their inversions:
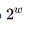
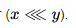
The main innovation is the use of a shift operation on a variable number of bits that were not used in earlier encryption algorithms. These operations are equally quickly performed on most processors, but at the same time significantly complicate the differential and linear cryptanalysis of the algorithm.
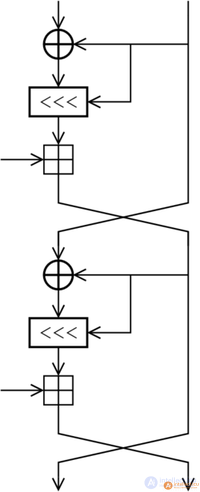
RC5 encryption consists of two steps. Key extension procedure and encryption directly. For decryption, the key expansion procedure is performed first, and then the operations opposite to the encryption procedure are performed. All addition and subtraction operations are performed modulo 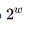
Because Since the RC5 algorithm has variable parameters, for the specification of the algorithm with specific parameters the designation RC5-W / R / b is accepted, where
Before directly encrypting or decrypting the data, the key extension procedure is performed. The key generation procedure consists of four stages:
Constant Generation
For a given parameter W, two pseudo-random variables are generated using two mathematical constants: e (exponent) and f (Golden Ratio).
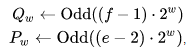
where Odd () is rounding to the nearest odd integer.
For w = 16.32.64, we obtain the following constants:

Key breaking into words
At this stage, the key is copied 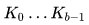 into an array of words
into an array of words 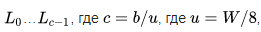 that is, the number of bytes in a word.
that is, the number of bytes in a word.
If a 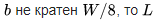 padded with zero bits to the nearest larger size c, a multiple of
padded with zero bits to the nearest larger size c, a multiple of 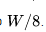
If b = c = 0, then we set the value 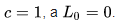
Building an extended key table
At this stage, the extension key table is built 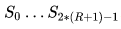 which is performed as follows:
which is performed as follows:
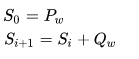
Stirring
The following actions are performed cyclically N times:
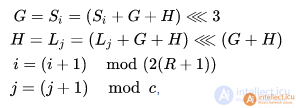
moreover, G, H, i, j are temporary variables whose initial values are 0.
The number of iterations of cycle N is the maximum of two values 3 * c and 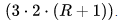
Before the first round, the operations of applying the extended key to the encrypted data are performed:
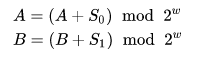
In each round, the following actions are performed:
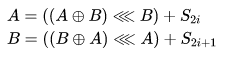
To decrypt data, reverse operations are used, i.e. for i = R, R-1, ..., 1 the following rounds are performed:
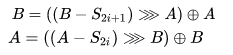
After completing all rounds, the original message is from the expression:
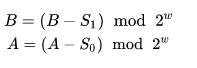
The RC5 algorithm has the following properties: [1]
RSA spent a lot of time analyzing its work with a 64-bit block. So, from 1995 to 1998, they published a number of reports in which they analyzed in detail the cryptographic strength of the RC5 algorithm. An evaluation for linear cryptanalysis shows that the algorithm is safe after 6 rounds. Differential cryptanalysis requires 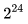 selected plaintexts for an algorithm with 5 rounds,
selected plaintexts for an algorithm with 5 rounds, 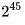 for 10 rounds,
for 10 rounds, 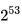 for 12 rounds and
for 12 rounds and 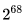 for 15 rounds. And since there is only
for 15 rounds. And since there is only 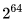 possible different plaintexts, then differential cryptanalysis is impossible for the algorithm in 15 or more rounds. So it is recommended to use 18-20 rounds, or at least not less than 15 instead of the 12 rounds that Rivest himself recommended.
possible different plaintexts, then differential cryptanalysis is impossible for the algorithm in 15 or more rounds. So it is recommended to use 18-20 rounds, or at least not less than 15 instead of the 12 rounds that Rivest himself recommended.
To stimulate learning and use of the RC5 cipher RSA Security Inc. On January 28, 1997, she proposed hacking a series of messages encrypted with the RC5 algorithm with different parameters, [2] giving a prize of $ 10,000 for hacking each message. The cipher with the weakest parameters RC5-32 / 12/5 was cracked for several hours. Nevertheless, the last hacking of the RC5-32 / 12/8 cipher required 5 years of calculations within the framework of the RC5-64 distributed computing project (here 64 = b · 8, the key length in bits) under the supervision of distributed.net. RC5-32 / 12 / b is still inaccessible for b from 9 to 16. distributed.net launched the RC5-72 project for hacking RC5-32 / 12/9 , in which as of October 2013 it was possible to sort out about 3 % keys. [3]
In May 2007, RSA Security Inc. announced the termination of support for the competition and the payment of cash rewards. In order not to stop the RC-72 project, distributed.net decided to sponsor a prize of $ 4,000 from its own funds. [4]
On platforms where the cyclic shift operation by a variable number of bits is performed for a different number of processor cycles, an attack during execution time on the RC5 algorithm is possible. Two options for such an attack were formulated by cryptanalysts Howard Haze and Helena Handschuh . They found that the key can be calculated after performing about 220 encryption operations with high-precision measurements of the execution time and then from 228 to 240 test encryption operations. The easiest way to deal with such attacks is to force shifts for a constant number of measures (for example, during the execution of the slowest shift).
Because one of the properties of RC5 is its simplicity in implementation and analysis, it is logical that many cryptologists [ who? ] wanted to improve the classic algorithm. The general structure of the algorithm remained unchanged, only the actions performed on each block in the process of direct encryption changed. So a few different variants of this algorithm appeared:
In this algorithm, modulo round key addition 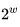 replaced by XOR operation:
replaced by XOR operation:
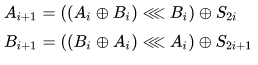
This algorithm turned out to be vulnerable to differential and linear cryptanalysis. Biryukov and Kushilevits managed to find an attack using differential cryptanalysis for the RC5XOR-32/12/16 algorithm using 228 selected plaintexts.
In this algorithm, the addition of two processed “blocks” by the XOR operation is replaced by modulo addition 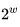 :
:
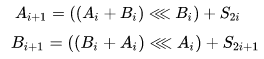
This algorithm turned out to be vulnerable to differential cryptanalysis.
In this algorithm, a cyclic shift is carried out by a fixed number of bits for a given round, and not by a variable.
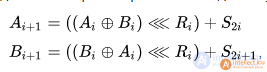
where Ri is a fixed number.
This algorithm is not well understood, but it is assumed that it is unstable to differential cryptanalysis.
In this algorithm, the number of shift bits depends on the algorithm key and on the current round:
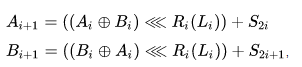
This algorithm is also not well understood.
In this algorithm, the number of shift bits is determined using some function of another “sub-block”:
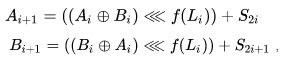
It is assumed that the RC5RA algorithm is even more resistant to known cryptanalysis methods than RC5.
Comments
To leave a comment
Information security, Cryptographic ciphers
Terms: Information security, Cryptographic ciphers