Lecture
Triple DES- A symmetric block cipher created by Whitfield Diffie, Martin Hellman and Walt Tachmann in 1978 based on the DES algorithm in order to eliminate the main shortcoming of the latter - a small key length (56 bits), which can be cracked using the full brute force key. The speed of 3DES is 3 times lower than that of DES, but the resistance to cryptanalysis is much higher - the time required for 3DES cryptanalysis may be a billion times longer than the time required for opening DES. 3DES is used more often than DES, which breaks down easily with today's technology (in 1998, the Electronic Frontier Foundation organized the use of the DES Cracker computer to break DES for 3 days). 3DES is an easy way to troubleshoot DES flaws. The 3DES algorithm is based on DES, so for its implementation it is possible to use programs created for DES.
Algorithm
The 3DES algorithm has the following form. A simple version of 3DES can be represented as follows:
DES (k3; DES (k2; DES (k1; M)))
where k1, k2, k3 - keys for each DES-step,
M - the input to be encrypted
This variant is known as in EEE, since the three DES operations are encryption.
There are 3 types of 3DES algorithm: DES-EEE3: Encrypted three times with three different keys (encryption-encryption-encryption operations).
DES-EDE3: 3DES operations encryption-decryption-encryption with three different keys.
DES-EEE2 and DES-EDE2: Like the previous ones, except that the same key is used in the first and third steps.
The most popular type of 3DES is DES-EDE3, for it the algorithm looks like this:
Encryption:
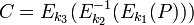
Decryption:
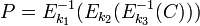
When running the 3DES algorithm, the keys can be selected as follows:
k1, k2, k3 are independent.
k1, k2 are independent, and k1 = k3
k1 = k2 = k3
Work principles
DES performs the DES algorithm 3 times, the DES key length is 64 bits, and the 3DES length is 3 times longer, that is, 192 bits. For DES, the 64-bit key is divided into 8 bytes, only 7 bits are used in each byte, so the key length is actually 56 bits, not 64, so the 3DES key length is actually 168, not 192 bits.
Comments
To leave a comment
Information security, Cryptographic ciphers
Terms: Information security, Cryptographic ciphers