Lecture
Vigener's cipher is a method of encrypting alphabetic text using a keyword.
This method is a simple form of multi-alphabetic substitution. Vigenera cipher was invented many times. This method was first described by Giovanni-Battista Bellaso (Giovan Battista Bellaso) in the book La cifra del. Sig. Giovan Battista Bellaso in 1553, but in the 19th century he received the name of Blaise Vigener, a Swiss diplomat. The method is simple to understand and implement, it is not available for simple cryptanalysis methods.
Encryption
Vigeneur square or Vigenere table, can be used for encryption and decryption.
In Caesar's cipher, each letter of the alphabet is shifted by several positions; for example, in Caesar's cipher with a shift of +3, A would become D, B would become E and so on. Vigener's cipher consists of a sequence of several Caesar ciphers with different shift values. For encryption, a table of alphabets called the Vigenere square can be used. In relation to the Latin alphabet, the Vigenere table is composed of lines of 26 characters each, with each subsequent line shifted by several positions. Thus, the table produces 26 different Caesar ciphers. At different stages of encoding, the Vigenère cipher uses different alphabets from this table. At each stage of encryption, different alphabets are used, selected depending on the keyword symbol. For example, suppose the source text is:
ATTACKATDAWN
The person sending the message writes the keyword ("LEMON") cyclically until its length matches the length of the source text:
Lemonlemonle
The first character of the source text A is encrypted with the sequence L, which is the first character of the key. The first character L of the cipher text is located at the intersection of row L and column A in the Vigener table. Similarly, the second key symbol is used for the second source symbol; those. The second character of the cipher text X is obtained at the intersection of line E and column T. The rest of the source text is encrypted in a similar way.
Example
Source Code: ATTACKATDAWN
Key: LEMONLEMONLE
Encrypted text: LXFOPVEFRNHR
Decryption
Decryption is performed as follows: we find in the Vigener table the string corresponding to the first character of the keyword; in this line we find the first character of the cipher text. The column in which this symbol is located corresponds to the first character of the source text. The following ciphertext characters are decoded in the same way.
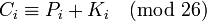
From the observation of the frequency of coincidence follows:
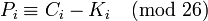
Comments
To leave a comment
Information security, Cryptographic ciphers
Terms: Information security, Cryptographic ciphers