Lecture
PGP combines the best of both traditional cryptography and public key encryption. PGP is a hybrid cryptosystem.
When a person encrypts data using PGP, PGP compresses them to start. Compression reduces their modem transfer time and saves disk space and, more importantly, enhances cryptographic strength. Most cryptanalytic techniques are based on the search for plaintext patterns. Compression reduces the number of such patterns, which significantly improves the resistance to cryptanalysis. (Too short files and files that are not compressed well enough are not compressed at all.)
Then, PGP creates a session key, which, in essence, is a one-time symmetric key that is used for only one operation. This key is a pseudo-random number generated from random mouse movements and keystrokes. The session key works on the basis of a very reliable, fast conventional algorithm that PGP encrypts a compressed message with; the result is encrypted text. As soon as the data is encrypted, the session key is also encrypted but already with the public key of the recipient. This public key encrypted session key is transmitted to the recipient along with the encrypted text.
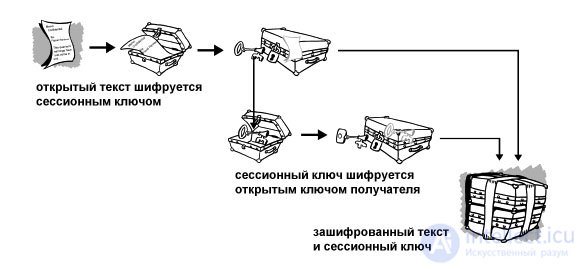
Fig. 1. This is how PGP encryption works.
Decryption occurs in reverse order. The recipient's PGP uses his private key to extract the session key from the message, which then decrypts the conventionally encrypted text.
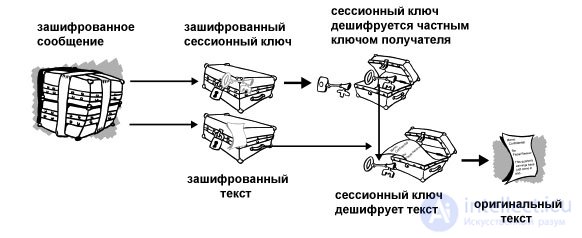
Fig. 2. This is how PGP decryption works.
Thus, the combination of these two methods combines the convenience of public key encryption with the speed of the conventional algorithm. Conventional encryption is almost a thousand times faster than asymmetric. Public key encryption, in turn, provides a simple solution to the key distribution and data transfer problem. Used together, the speed of execution and distribution of keys are mutually complemented and improved without any damage to security.
Comments
To leave a comment
Information security, Cryptographic ciphers
Terms: Information security, Cryptographic ciphers