Lecture
IDEA (English International Data Encryption Algorithm, international data encryption algorithm) is a symmetric block data encryption algorithm patented by the Swiss company Ascom. Known for being used in the PGP encryption software package and in its free alternative to GnuPG. In November 2000, IDEA was presented as a candidate for the NESSIE project in the framework of the European Commission IST program (information Societes Technology, information social technologies).
Description
Since IDEA uses a 128-bit key and a 64-bit block size, the plaintext is divided into blocks of 64 bits. If such a partition is not possible, different encryption modes are used. Each initial unencrypted 64-bit block is divided into four sub-blocks of 16 bits each, since all algebraic operations used in the encryption process are performed on 16-bit numbers. IDEA uses the same algorithm for encryption and decryption.
A fundamental innovation in the algorithm is the use of operations from different algebraic groups, namely:
addition modulo 216
multiplication modulo 216 + 1
Bitwise exclusive OR (XOR).
These three operations are incompatible in the sense that:
None of the two satisfy the distribution law.
No two of them satisfy associative law.
Encryption
The structure of the IDEA algorithm is shown in the figure.
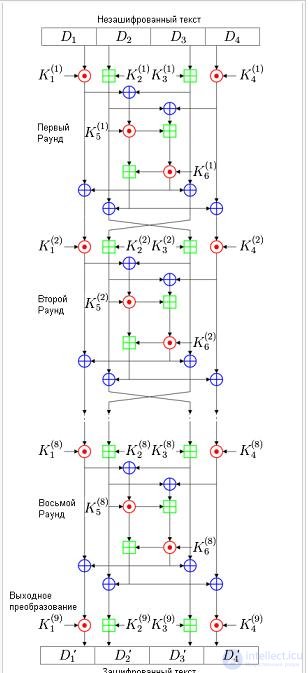
The encryption process consists of eight identical rounds of encryption and one output transform. The original unencrypted text is divided into blocks of 64 bits. Each such block is divided into four sub-blocks of 16 bits each. In the figure, these sub-blocks are designated D1, D2, D3, D4. Each round uses its own plug-in according to the plug-in table. The following operations are performed on 16-bit subkeys and non-cipher sub-blocks:
multiplication modulo 216 + 1 = 65537, with 216 being used instead of zero
addition modulo 216
bitwise exclusive OR
At the end of each encryption round, there are four 16-bit sub-blocks, which are then used as input sub-blocks for the next encryption round. The output transformation is a shortened round, namely, four 16-bit sub-blocks at the output of the eighth round and four corresponding subkeys are subjected to operations:
multiplication modulo 216 + 1
addition modulo 216
After the output transform, the concatenation of the D1 ', D2', D3 ', and D4' subblocks is the encrypted text. Then the next 64-bit unencrypted text block is taken and the encryption algorithm is repeated. This continues until all 64-bit blocks of the source text are encrypted.
Comments
To leave a comment
Information security, Cryptographic ciphers
Terms: Information security, Cryptographic ciphers