Lecture
The Vernam code, or one-time pad, was invented in 1917 by Major Joseph Mauborn and Gilbert Vernam from AT & T (American Telephone & Telegraph). In the classical sense, a one-time pad is a large, non-repeating sequence of key symbols, randomly distributed. It was originally a disposable tape for teletypes. The sender used each key character to encrypt only one plaintext character. Encryption is the addition modulo n (power of the alphabet) of a plaintext symbol and a key symbol from a one-time pad. Each key symbol is used only once and for a single message, otherwise even if you use a notebook of several gigabytes in size, when the cryptanalyst receives several texts with overlapping keys, he will be able to restore the original text. He will shift each pair of ciphertexts relative to each other and count the number of matches in each position. if the ciphertexts are shifted correctly, the ratio of matches will increase dramatically. From this point of view, cryptanalysis is not difficult. If the key is not repeated and accidental, then the cryptanalyst, whether he intercepts the texts or not, always has the same knowledge. A random key sequence, combined with non-random plaintext, gives a completely random cryptotext, and no computational power can change this.
Of use
In real systems, first prepare two identical tapes with random key numbers. One remains with the sender, and the other is transmitted in a "non-intercepted" manner, for example, by courier with a guard, to the legal recipient. When the sender wants to send a message, he first converts it into binary form and places it in a device that adds two digits read from the key tape to each digit of the message. On the receiving side, the encoded message is recorded and passed through a machine similar to the device used for encryption, which adds to each binary digit of the message (subtracts since the addition and subtraction modulo two are equivalent) modulo two digits read from the key tape, receiving thus plaintext. At the same time, of course, the key tape should move absolutely synchronously with its duplicate used for encryption.
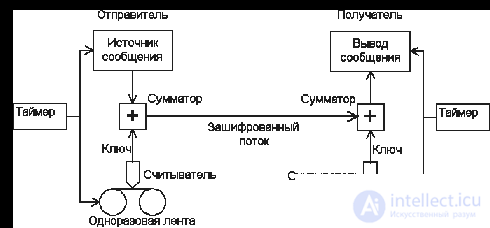
Figure 1 shows the operation of encryption cipher Vernama
disadvantages
The main disadvantage of this system is that for each bit of information transmitted, a bit of key information must be prepared in advance, and these bits must be random. When encrypting a large amount of data, this is a serious limitation. Therefore, this system is used only to transmit messages of the highest secrecy.
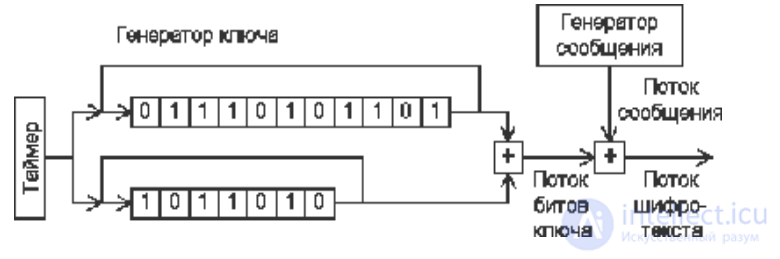
To get around the problem of pre-transferring a high-volume secret key, engineers and inventors have come up with many ingenious schemes for generating very long streams of pseudo-random numbers from several short streams according to some algorithm. The recipient of an encrypted message must be provided with exactly the same generator as the sender. But such algorithms add regularity to the ciphertext, the detection of which can help the analyst to decrypt the message. One of the main methods of constructing such generators is to use two or more bit tapes, read from which the data are added bit by bit to obtain a "mixed" stream.
Comments
To leave a comment
Information security, Cryptographic ciphers
Terms: Information security, Cryptographic ciphers