Lecture
Steganography is the science of the hidden transfer of information by keeping secret the fact of transmission. The main task is to ensure that a person does not suspect that there is hidden valuable information inside the transmitted information that does not represent outwardly absolutely no value. Thus, steganography allows transmitting secret information through open channels, hiding the very fact of its transmission. Cryptography protects the message, making it useless in the event of interception, and steganography tends to make the message transmission itself hidden. Cryptography and steganography can be used together: then the message is first encrypted and then secretly transmitted. If you use cryptography without steganography, then there is a risk that the observer who intercepted the message will force the sender or recipient to decipher it.
Stegoanalysis or steganalysis is a section of steganography; the science of identifying the fact of the transfer of hidden information in the analyzed message. In some cases, steganalysis also refers to the extraction of hidden information from the message containing it and (if necessary) its further decryption. The latter definition should be used with the appropriate reservation.
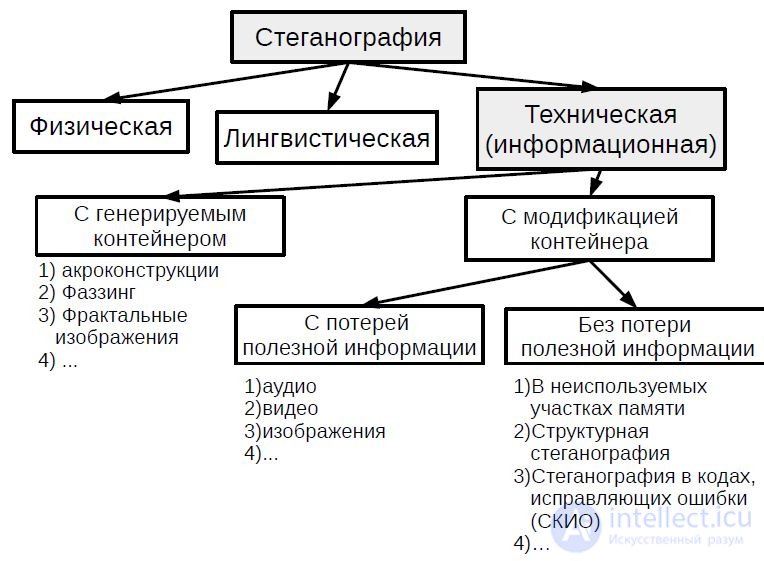
Steganography today
● Big Data - very, very much data
● A huge number of data transfer and storage protocols, file systems, operating systems
● Internet
● Internet - IoT
● Internet - a large number of participants, data channels
All of the above creates a good support for steganography.
Three goals of information hiding
● Hidden transmission or storage of data (SPD) - only this is steganography (“concealment”) in the strict sense
● Watermarks (OT, “digital watermarking”)
- certain labels that are the same for each copy
● Tsiforovye prints (TSO, "stego fingerprinting") - certain labels, different for each copy.
CO vs OT
● It is necessary to distinguish between CO and OT! At least because of the attack by collusion. VZ can be steganography: steganographic VZ (SVZ), CO - no.
● Attack by collusion. Take n copies of the container and create one copy of them - a bitwise XOR of each of them.
Remark 1. The term “informational concealment” is not established in Russian-language literature and is often the Central Organ, OT also called “steganography”
Note 2. There is a term “CEH” (digital watermark). This is the central organ, the OT. Sometimes both simultaneously in one article;)
Practical use
1. Imperceptible information transfer (SPD)
2. Hidden storage of information (SPD)
3. Non-declared information storage (SPD)
4. Protection of exclusive rights (AC)
5. Copyright Protection (OT)
6. Protection of authenticity of documents (OT)
7. Individual imprint in SEDO (CO)
8. Watermark in DLP systems
9. Hidden transmission of the control signal (SPD)
10. Steganographic botnet network (SPD)
11. Inalienability of information (OT)
12. Confirmation of the accuracy of the information transmitted (AC)
13. Funkspiel (“Radio Game”) (SPD)
14. Steganographic Tracking (SPD)
15. Steganographic distraction.
Wikipedia, the free encyclopedia
Stegoanalysis or steganalysis is a section of steganography; the science of identifying the fact of the transfer of hidden information in the analyzed message. In some cases, steganalysis also refers to the extraction of hidden information from the message containing it and (if necessary) its further decryption. The latter definition should be used with the appropriate reservation.
The intruder (analyst) seeks to crack the steganographic system, that is, to detect the fact of the message being transmitted, to extract the message and either modify the message or prohibit the message transmission [1]. Usually analysts spend several stages hacking the system [1]:
In this case, the system is considered hacked if the analyst succeeds in proving at least the presence of a hidden message. [1]
During the first two stages, analysts can usually hold such events [2]:
There are several types of offenders [2]:
Some attacks on steganosystems are similar to cryptographic attacks [1]:
But there are also attacks that have no direct analogues in cryptography [3]:
There are specific attacks on digital watermark systems [2]:
Head shave
An attack based on a well-known filled container against an ancient messaging system on the skin of a slave’s head. A tattoo message was put on the head of the slave and they waited for the hair to grow back. Then the slave was sent to the recipient of the message. The attack of the system is primitive - to shave the slave again and read the message [4].
Manifestation
An attack based on a well-known filled container against a message transfer system with a letter written in sympathetic ink. During World War II, analysts drove brushes moistened with developers by writing and read the messages that were shown. Transmission by ultraviolet or infrared radiation has also been used [4].
Subjective attack
Attack based on known filled container. The algorithm is simple: the analyst examines the container without the help of special tools, trying "by eye" to determine if it contains stego. That is, if the container is an image, then looks at it, if the audio is, then it listens. Despite the fact that such an attack is effective only against almost unprotected steganographic systems, the attack is widespread at the initial stage of opening the system [2].
Histogram image analysis
Attack based on known LSB-filled container. Andreas Fitzmann and Andreas Westfeld noted [5] that if the embedded message has a uniform distribution, the frequencies  the appearance of color
the appearance of color  before embedding were related by
before embedding were related by  then frequency
then frequency  after embedding, they are associated with frequencies prior to embedding in such a relation:
after embedding, they are associated with frequencies prior to embedding in such a relation:

That is, the introduction of a uniform message reduces the difference between the frequencies of the distribution of neighboring colors that have the difference in the smallest bit. It is also noted that during the LSB implementation, the sum of the frequency distribution of neighboring pairs remains unchanged. On these facts, an analysis method is built using the Chi-square test:

 where
where  - the number of histogram columns minus 1
- the number of histogram columns minus 1 that the two distributions will be the same and that there is a hidden message in the container is equal to
that the two distributions will be the same and that there is a hidden message in the container is equal to  where
where  - gamma function.
- gamma function.Usually, a series of probability measurements are carried out for the image fragments in order to also measure the length of the intended message by the probability jump.
In the case when the container is not an image with color indexation, but a JPEG image, instead of color indices, the coefficients of the discrete cosine transform are used for the analysis [5].
RS image analysis
An attack based on a well-known filled container on the system for embedding stego into an image using the LSB method. Regular-Singular analysis was proposed in 2001 by a team of researchers from Binghamton University [5].
The method is based on the division of the image into related groups.  by
by  pixels For each group, the value of the regularity or smoothness function is determined.
pixels For each group, the value of the regularity or smoothness function is determined.  . Most often, the regularity function is the sum of the differences of neighboring pixels in a group [5].
. Most often, the regularity function is the sum of the differences of neighboring pixels in a group [5].
Flipping function is introduced - function  such that
such that  . In this analysis, three functions of flipping are used [5]:
. In this analysis, three functions of flipping are used [5]:
 - inversion of the least significant bit of color in the image
- inversion of the least significant bit of color in the image - leaving unchanged
- leaving unchanged - inversion of the least significant bit of color in the image with transfer to the most significant bit (that is
- inversion of the least significant bit of color in the image with transfer to the most significant bit (that is  ,
,  etc.).
etc.).Inside the group, you can use different flipping functions for different pixels, so they write a mask  -
-  -dimensional vector in space}
-dimensional vector in space}  indicating which pixel in the group corresponds to which flipping:
indicating which pixel in the group corresponds to which flipping:  [five]
[five]
All received groups  divided into three types [5]:
divided into three types [5]:
 increases smoothness value
increases smoothness value reduces smoothness
reduces smoothness does not change the value of smoothness
does not change the value of smoothnessNext, count the number  number of regular groups
number of regular groups  singular groups for the mask M and similar quantities
singular groups for the mask M and similar quantities  ,
,  for the inverted {-M} mask. The statistical hypothesis of researchers, confirmed by the study of a sample of real photographs, is that the inversion of the mask almost does not change the number of regular and singular groups for an empty container [5]:
for the inverted {-M} mask. The statistical hypothesis of researchers, confirmed by the study of a sample of real photographs, is that the inversion of the mask almost does not change the number of regular and singular groups for an empty container [5]:
 ,
, 
At the same time, the researchers noticed that introducing random distortions into this ratio violates this ratio so that random distortions reduce the difference between  and
and  with increasing the length of the message being injected. This fact is based on the method of RS-analysis [5]:
with increasing the length of the message being injected. This fact is based on the method of RS-analysis [5]:
 and the proportion of changes in the lower bits when writing a message is 50%:
and the proportion of changes in the lower bits when writing a message is 50%:
 and
and  built at two points: with an unchanged image (that is, at the point with the abscissa
built at two points: with an unchanged image (that is, at the point with the abscissa  ) and in the image with inverted low-order bits (i.e. at the point with abscissa
) and in the image with inverted low-order bits (i.e. at the point with abscissa  )
) and
and  build on three points: at the point with the abscissa
build on three points: at the point with the abscissa  at the point of abscissa
at the point of abscissa  and at the point with the abscissa 50% (writing random values to the low bits)
and at the point with the abscissa 50% (writing random values to the low bits) over 0 and abscissa
over 0 and abscissa  for 1, determine the abscissa
for 1, determine the abscissa  curve intersection points
curve intersection points  and
and  and consider the estimated length of the message:
and consider the estimated length of the message: 
Machine learning method for image analysis
The method coined by Sewie Liu and Honey Farid in 2002 in response to the improvement of message embedding algorithms. They suggested using the support vector method, well-known in machine learning. As a feature vector, the method uses a vector calculated on the basis of the statistical regularities of the distribution of groups of image pixels: expectation, variance, standard deviation, etc. [5]
Attack using compression algorithms for analyzing audio files
It is noted [6] that files containing hidden messages can be compressed using compression algorithms worse than not containing messages. This remark is based on a group of attacks using compression methods. One of these attacks is the WAVE format audio file analysis method.
The analysis algorithm [6] assuming that the file (empty container), the algorithm for implementing the stego message, and the data compression algorithm are known:
 and filled container}}
and filled container}}  .
. and compares with a pre-selected threshold value
and compares with a pre-selected threshold value  . If a
. If a  , then we can conclude that the file contains a stego message.
, then we can conclude that the file contains a stego message.The threshold values depending on the content of the audio file and the archiver used are determined experimentally and lie in the range from 0.05% to 0.2% [6].
Attack using compression algorithms for analyzing text files
The attack is based on the same fact as an attack on audio files using compression algorithms. Let there be three texts:  ,
,  and
and  , and
, and  and
and  contain hidden messages. If you write
contain hidden messages. If you write  at the end of each text
at the end of each text  and
and  , compress the resulting texts with the archiver and measure the dimensions that the text occupies in the received archives
, compress the resulting texts with the archiver and measure the dimensions that the text occupies in the received archives  then it turns out that in the archive received from the texts
then it turns out that in the archive received from the texts  and
and 
 takes up less space. This can be interpreted as a sign of the presence of a stego message in the container
takes up less space. This can be interpreted as a sign of the presence of a stego message in the container  [7]
[7]
Algorithm:
 and
and  receiving files
receiving files  and
and  .
. and
and  both initial files. Also measured are compression ratios.
both initial files. Also measured are compression ratios. and
and  both received files.
both received files. and
and  . It was established experimentally that plain text satisfies the condition
. It was established experimentally that plain text satisfies the condition  or
or  . If the measured values do not satisfy this condition, the presence of the stegotext can be considered as established.
. If the measured values do not satisfy this condition, the presence of the stegotext can be considered as established.An attack using a compression algorithm for analyzing executable files [
The attack is based on the same facts as other attacks based on compression algorithms, but uses the features of the PE executable file format and the specific implementation algorithm [8] of the message for which analysis is used. [9]
Algorithm:
 byte of the section.
byte of the section.  chosen experimentally in advance.
chosen experimentally in advance. , then the analyst can conclude that the stego message is present in the file.
, then the analyst can conclude that the stego message is present in the file.  also determined experimentally.
also determined experimentally.Attacks on video files [
As one of the examples of the analysis of video files, one can cite a statistical analysis similar to histogram image analysis. The analyst in this case checks the statistical properties of the signal and compares them with the expected ones: for example, for the lower bits of the signals, the distribution is similar to the noise. The Chi-square test works well for comparison. [10]
To destroy the message, you can use various transformations [10]:
Comments
To leave a comment
Information security, Cryptography and cryptanalysis, Steganography and Stegoanalysis
Terms: Information security, Cryptography and cryptanalysis, Steganography and Stegoanalysis