Lecture
There is a growing concern in society that computers now represent or will pose in the near future a dangerous threat to privacy. Since many computers contain personal data and are accessible through remote terminals, they are an unsurpassed means of accumulating large amounts of information about individuals and groups of people. Experts believe that it will soon become technically feasible to maintain a detailed dossier for each citizen, whereas, until very recently, the data for such dossiers were scattered in many places, also belonging to the jurisdiction of completely different departments. However, I'm going to show in this article that computer systems can still be adapted to protect the information stored on them from all people, except, of course, those who are allowed to access them, by encrypting the data into forms that are very resistant to hacking attempts. .
Traditionally, the people most in need of secrecy were military and diplomats. The elements of surprise are often necessary in their work, and a surprise of this kind always assumes secrecy. As for ordinary people, whatever the need for secrecy they felt, it remained their personal problem and was rarely submitted for public discussion; lovers and thieves always themselves, as they could provide their needs for secret communication. This state of affairs did not change much until the middle of the XIX century - just about that time, scientific methods and ways of thinking were involved in improving the technique of secret writing. Despite this, until our century, the methods used for secret communication continued to be procedures performed with the help of pencil and paper.
Cryptographic encryption can be achieved in two completely different ways: using ciphers and using codes. The difference between them is as follows: the cipher always defines wildcards for some given set of letters of the alphabet. Being in its nature a procedure knotted in alphabet, the cipher allows you to express everything that can be typed on a typewriter in any language. This means that through the cipher you can express thoughts that have never been expressed before or even assumed that in the future it may be necessary to express them. On the other hand, the code is semantic in its internal character. With the help of the code, it is possible to express only what was thought out beforehand and is provided for transmission in the form of a secret list, such as a code book, for example.
It must be remembered that in our time the word "code" is often used in a meaning not related to cryptography. In such cases, the term usually has a broad meaning, including sets of characters with a special purpose. So, they talk about error detection and correction codes, data compression codes, telecommunication codes, commercial codes and codes that include all kinds of intricate electrical signals and waveforms.
Taking on the IBM Watson research center of IBM for the security problem created by modern computers, we assigned the main role in its solution to the use of encryption methods. Of course, it would have been impossible to cover in this article the whole subject of ensuring the confidentiality of data warehouses and the security of computer operations. I, however, hope to show you the principles closely related to these problems that underlie data encryption and authentication of their sources.
In modern machine-to-machine networks of the type that is needed to create data warehouses, the concept of secrecy implies something more than just hiding messages from outsiders. Data warehouses include as part of the terminal-computer networks. The communication lines connecting the terminals with computer centers are completely open not only for intercepting information, but also for its deliberate change and distortion. Thus, in addition to the already fairly obvious aspects of data secrecy, it is necessary to provide adequate protection against possible abuses in the system. Simple error detection cannot solve this problem. It requires that the system itself make it extremely unlikely that a non-authorized, but smart and sophisticated person could enter and read or distort the data, or execute commands in such a system.
This is vital, since even the minimum amount of spurious data that has been accidentally entered into the data storage system or intentionally entered into the data storage system can make its work meaningless. A computer without sufficient protection is easily deceived, especially by a person who is well versed in the principles of his work. Indeed, terminals can be used for ingeniously planned insertions of false data into the system. To protect the purity of the data bank, it is necessary to verify the authenticity of the legitimate source and the nature of any data obtained from it, and to do it very quickly and with a high degree of reliability.
Let's start considering the question from the most elementary fact about ciphers: all cryptography comes down to substitutions. In its simplest form, the substitution can be specified using a table, as shown in the following illustration. The left column of the table lists the usual letters of the alphabet from which the plaintext is composed; on the right side, their equivalents, which are specified by the cipher, and which are the substituted values. Amateurs are often discouraged by a huge number of ways to perform such substitution or permutations of the alphabet. For the Latin alphabet containing 26 letters, there are 123 ... 26 ways to write a single substitution alphabet. (Such a product is called 26- "factorial" and is written 26! The factorial of any number n! Is the product of all integers from 1 to n.)
The number n! possible permutations of a table with n entries is the number of possible "keys". In this case, 26! - this is a very large number, more than 41026. But despite this, any simple alphabetical substitution can easily be uncovered by statistical analysis based on the definition of the frequency of characters in the text. If the letter Q is more common than any other letter in a sufficiently long section of ciphertext, the analyst can be quite sure that this letter replaces E, the letter that is most often found in English texts.
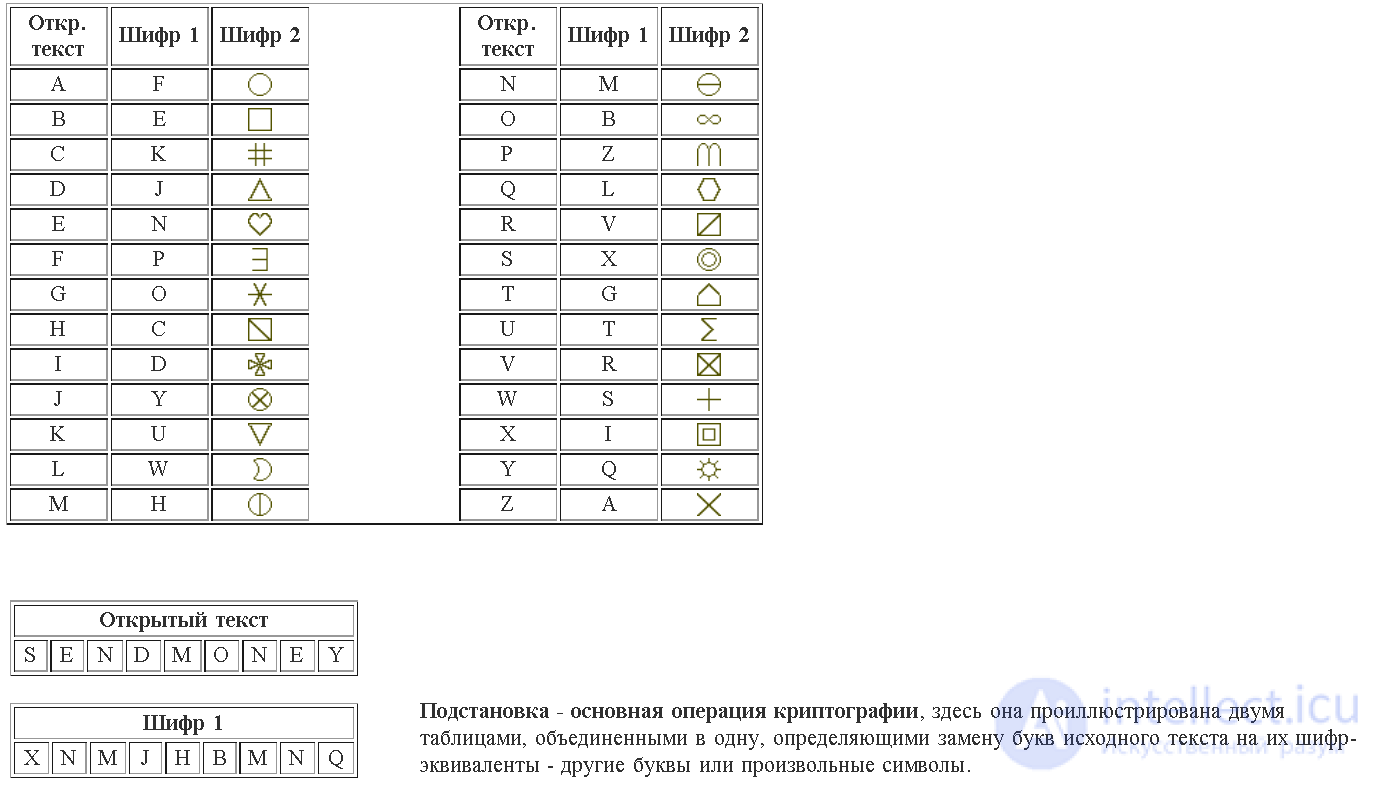
Of course, replacing the letters of the alphabet with substitutions for mysterious-looking characters does not bring any advantages. The analyst may not worry about how complex the characters of the message look, he will simply replace them arbitrarily with the letters of a regular alphabet or number, and subject the message to frequency analysis. The “mysterious characters” approach, however, demonstrates the flexibility of the cipher with respect to possible replacement characters. Since lookup tables, despite their well-known weakness, are fundamental to cryptographic developments, let's consider the possibility of using really useful lookup characters.
This can indeed be done. The binary number system, which contains exactly two digits, 0 and 1, is ideal for cryptographic data conversion by computers. Using n binary digits, 2n different binary codes can be written. So, using a block of 5 binary digits, you can write 25 or 32 different combinations, more than enough to encode 26 letters of the alphabet (see the following illustration). If we want to name or mark more elements, we will have to increase our stock of binary numbers, simply by increasing the size of the digital block. Every time we increase the block size by one digit, we double the number of possible codes. Consequently, a six-digit code provides 26 or 64 different codes, or enough to include decimal digits, punctuation, etc.
In addition to the ease with which binary digits can be represented in electrical circuits (for example, by the presence or absence of a signal in a conductor), they have all the useful properties of ordinary decimal numbers. Thus, binary numbers can be added, subtracted, multiplied, etc. just like ordinary decimal numbers. We show that arithmetic data manipulations play a vital role in cryptographic techniques developed for computers.

Comments
To leave a comment
Information security, Cryptography and cryptanalysis, Steganography and Stegoanalysis
Terms: Information security, Cryptography and cryptanalysis, Steganography and Stegoanalysis