The audit subsystem in the UNIX family of operating systems allows you to effectively track the actions of users in the system. Most Unix operating systems use a centralized syslog system message logging system. This system allows the administrator to maintain full control over the messages of both the system and system processes, and application processes. It is very flexible and allows sorting messages by source as well as importance and direct them to various destinations: to log files, to user terminals and even to other machines on the network. Thus, the administrator can organize a centralized procedure for registering system messages throughout the network.
Syslog system consists of three components:
- the syslogd daemon that logs events;
- library functions openlog (), syslog (), closelog () , which send messages to the syslogd daemon;
- a logger command that receives messages from the command interpreter.
The syslogd daemon starts at boot time and runs continuously. Processes and daemons interact with this daemon through the syslog, openlog, closelog library functions, which are described in /usr/include/sys/syslog.h . The /etc/syslog.conf file is the syslogd daemon configuration file. In order for the daemon to re-read the configuration file, it needs to send a HUP signal.
The configuration file itself consists of lines of the form
action selector
Blank lines and lines starting with a '#' character are ignored. It is allowed to have several tabs between the selector and the action, however the use of spaces as separators is not allowed. This can lead to hidden errors when using different editors, so the administrator must be very careful when editing this file.
The selector format is as follows:
remedy
where the tool indicates the source of the message and the level determines the severity level of the message. Both the names of the means and the levels have a standard set of values; the administrator cannot use arbitrary values for them. You can also use the characters '*' and none as means and level values. These symbols denote “all” and “nothing”, respectively. It is allowed to specify several selectors, separated by the symbol ';' or ',' in one line. for example
tool 1. level 1; tool 2. *; *. level 3 action
In this case, the selectors are combined according to the “OR” scheme, i.e. action will be performed for the message corresponding to any of the selectors. The basic set of tools and levels are given in Tables 6.1 and 6.2, respectively [13].
Table 6.1
System syslog tools.

Table 6.2
Syslog system severity levels
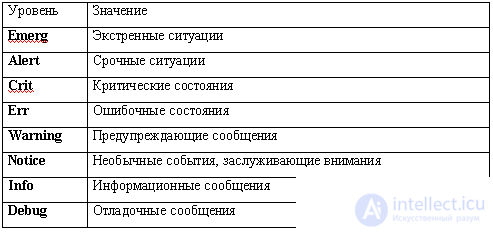
The message level determines its importance. In table 6.2, the levels are given in descending order of importance. By default, the syslog.conf file specifies the minimum importance that a message must have in order to be registered. In other words, if specified
mail.warning action1
This “action1” will be performed for all messages from the mail subsystem with warning levels, as well as with err, crit, alert and emerg levels . In BSD systems, additional level indication capabilities are also allowed. For example, mail.> = Warning is the same as using mail.warning; mail. = warning - for registration of messages of the warning level only ; mail. <= warning - to log messages of warning level and below; mail. <warning <b = ""> - to log messages below the warning level ; mail.> warning - to register messages above the level of warning .
The action determines what to do with the message. The following options are possible: filename - write a message to the specified file (you must use the absolute path to the file); @ machine_name - send a message to the syslogd daemon on the machine with the specified name; @ ip_address - send a message to the syslogd daemon on the machine with the specified IP address; user1, user2 - print a message to the terminals of the specified users; * - display a message on the terminals of all users.
By default, the syslogd daemon works on port 514 UDP , you can use the ss flag when starting the daemon, to disable work on the network. In addition, in BSD systems it is allowed to register messages from application processes that do not correspond to any standard means. To do this, use the following syntax.
! myprog>
* .error /var/log/myprog_error.log
*. * /var/log/myprog.log
In this case, after the line ! Myprog , the process myprog is implied as a means, right down to the next line with a '!' .
It should also be particularly noted that the syslogd daemon does not create the files specified in the "action" field, and for it to work correctly, the files must already exist. To create files, you can use the touch command or use the special utility newsyslog , which will be discussed later. The administrator should be especially careful when setting permissions for log files, as these files may contain some important information and even in some cases user passwords.
During system operation, the volume of log files may increase significantly. Working with large files is not very convenient, in addition, if no action is taken, these files can fill up all the free space on the hard disk. In addition, the administrator is unlikely to be useful information with a very long limitation period. Therefore, periodically it is necessary to archive old log files. Most systems use the newsyslog utility for this. This utility uses the principle of rotation of log files. This means that several archived versions of files are stored, and if necessary, the current log file is archived, all versions are renamed, and the oldest version is deleted. By default, the newsyslog utility is started by the cron daemon every hour and checks for the need to archive certain files. The /etc/newsyslog.conf file is the configuration file for this utility. Using the newsyslog utility allows the administrator to very flexibly and effectively configure the procedure for archiving log files. In addition, the newsyslog utility , after archiving a file, creates an empty file with the specified access rights, which facilitates the use of the syslog system.
The newsyslog.conf file consists of text lines containing the following fields: logfilename is the name of the log file, owner.group is the user name and group that will be used as owners for the new log file; mode - access mode for the new log file; count - the number of archive copies of the file to be stored; size - archives and rotates the log file specified in the logfilename field if its size exceeds the specified number of kilobytes; time - perform archiving and rotation of the log file, if the specified number of hours has passed since the last backup; ZB - flags field, if the Z flag is present, the files should be archived during rotation, if the B flag is present, the file is considered binary and newsyslog will not add any information to this file (by default newsyslog adds a text line to the new file); The last two fields contain the file in which the process identifier and the signal number are stored. If these fields are not empty, then after creating a new file, the specified signal will be sent to the specified process. Thus, the process will be informed about the replacement of the log file. Usually, either the size field or the time field is filled in, the '*' symbol in these fields indicates any value. If both fields are filled in, archiving will be performed if at least one of the two conditions is met.
Thus, we can conclude that in the Unix family of operating systems, the audit system is implemented very effectively and allows the administrator to organize a centralized message accounting policy for the entire network with the possibility of timely archiving of log files.
Configuring syslog.conf
syslog.conf By default, /etc/syslog.conf is configured in such a way that a lot of messages are displayed directly to the console. Perhaps this is not what you want. Here is a way to change this.
syslogd syslog is a function used by many programs to write messages to the system message logger ( syslogd ). The syslogd daemon reads and displays messages on the system console, in the registration files (log files), on other machines and users according to its configuration file ( /etc/syslog.conf ).
syslog.conf The first thing you need to know about syslog.conf is that it requires tabs, not spaces! Therefore, if, after editing this file, you suddenly begin to receive errors, then most likely, instead of tabs you inserted spaces. Keep in mind that the editor inserts spaces in it, even if you press the tab key, while vi is not seen in this sin. This is the default syslog.conf shipped with FreeBSD 3.1: # $ Id: syslog.conf, v 1.9 1998/10/14 21:59:55 nate Exp $
#
# Spaces are NOT valid field separators in this file.
# Consult the syslog.conf (5) manpage.
* .err; kern.debug; auth.notice; mail.crit / dev / console
* .notice; kern.debug; lpr.info; mail.crit; news.err / var / log / messages
mail.info / var / log / maillog
lpr.info / var / log / lpd-errs
cron. * / var / cron / log
* .err root
* .notice; news.err root
* .alert root
* .emerg *
# uncomment
# news.crit /var/log/news/news.crit
# news.err /var/log/news/news.err
# news.notice /var/log/news/news.notice
! startslip
*. * /var/log/slip.log
! ppp
*. * /var/log/ppp.log
And this is syslog.conf , which I did for a friend: *. *; mail.none; cron.none; kern.none; local0.none;
ftp.none; auth.none; authpriv.none / var / log / messages
mail. * / var / log / maillog
cron. * / var / cron / log
kern. * /var/log/kernel.log
auth. *; authpriv. * /var/log/auth.log
# uncomment
# news.crit /var/log/news/news.crit
# news.err /var/log/news/news.err
# news.notice /var/log/news/news.notice
local0. * /var/log/tcpd.log
local0.info; local0.debug /var/log/firewall.log
local0.err /var/log/firewall.err
ftp. * /var/log/ftp.log
! startslip
*. * /var/log/slip.log
! ppp
*. * /var/log/ppp.log
! popper
*. * /var/log/popper.log
man syslog.conf What you really need to read is man syslog.conf .
Which changes The first thing you should pay attention to is that I removed / dev / console from the file. That is, messages will no longer appear on the console. Also, you can see that some messages are redirected to other places.
After change After all the changes made to /etc/syslog.conf , do not forget to report this to syslogd . This command will force syslogd to re-read its configuration file. killall -HUP syslogd |




Comments
To leave a comment
Information security, Cryptography and cryptanalysis, Steganography and Stegoanalysis
Terms: Information security, Cryptography and cryptanalysis, Steganography and Stegoanalysis