Lecture
One of the most popular methods to protect a local network from outside attacks is to use a firewall (ITU). A firewall (firewall) is a software or hardware / software system that is installed on the border of the protected computer network and filters network traffic in both directions, allowing or prohibiting the passage of certain packets into the local network (into the perimeter of security) or from it depending on the chosen security policy. However, modern ITU tasks are not limited to packet filtering; they also perform many additional actions:
There are two main types of ITU: packet filters and application gateways. In this case, both types can be implemented simultaneously in the same firewall. Packet filters are network routers that decide whether to pass or block a packet based on the information in its header (Fig. 5.3).
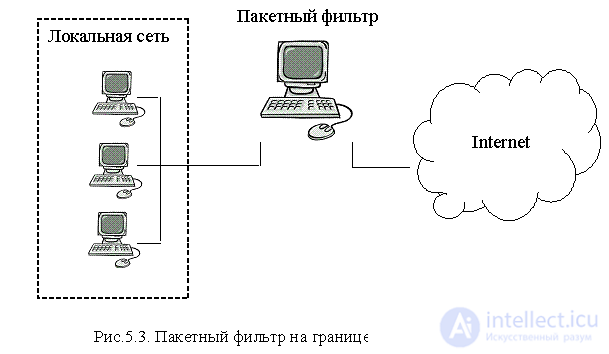
Packet filters work with information in the IP, ICMP, TCP, and UDP header lines. Packet filtering rules are based on the following data:
When defining filtering rules, you must adhere to one of two security policy strategies:
1. Allow all traffic not prohibited by filtering rules.
2. Deny all traffic not allowed by filtering rules.
From the point of view of security, the second strategy is preferable, according to which rules are established that allow the passage of packets of a certain type, the passage of the remaining packets is prohibited. This is due to the fact that, firstly, the number of prohibited packages is usually much more than the number of allowed ones, and secondly, over time, new services may appear, for which, when using the first strategy, it will be necessary to add forbidding rules (if access to them is, of course, undesirable), while the second strategy will prohibit access to them automatically.
Packet filters are classified into memoryless filters and memory filters (dynamic). The first of them filter information only on the basis of information in the header of the package in question. Dynamic packets, when filtering, take into account the current state of connections, form tables of incoming and outgoing packets, and make a decision based on information in several interconnected packets.
In addition, packet filters can also implement many additional features. For example, packet forwarding, packet duplication, traffic counting, bandwidth limiting, writing packets to a protocol file, and more. Setting up a packet filter requires an administrator of considerable qualifications and an understanding of the principles of operation of all protocols of the TCP / IP stack, from application layer protocols to network layer protocols.
Most modern operating systems have built-in packet filters, for example ipfw on Unix or Internet Connection Firewall on Windows. Packet filter functions can also be performed by hardware routers, for example, CISCO PIX 515E.
The main drawback of packet filters is the impossibility of filtering packets according to the contents of the information part of the packets, that is, according to the data related to higher-level packets. This deficiency can be eliminated by using application gateways (application gateway, proxy-server). Proxy servers operate at the application level, ensuring the operation of a network service. At the same time, unlike packet filters, which only redirect a packet from one network to another, proxy servers accept the request from the client and send it to the external network on their own behalf, thus disrupting normal network traffic (see Figure 5.4). Therefore, an application gateway firewall can be implemented on a computer with only one network interface.
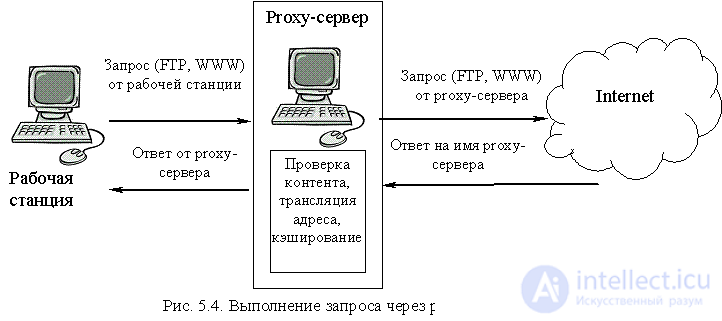
Let us explain the scheme in Figure 5.4. The client makes a request to the server of any service on the Internet (for example, a request to an external Web server). The request goes to the proxy server (the firewall configuration must be such that all requests to any service on the Internet must go to the appropriate proxy server). Having received a request from the client, the proxy server checks it according to the specified packet content filtering rules and, if the request does not contain any forbidden parameters, creates a packet with the request already on its behalf (with its return address) to the external server. The response from the external server comes, obviously, in the name of the proxy server. Having passed the test similar to the request, the answer can be accepted or rejected. If the answer is accepted, the answer is sent to the address of the client who originally formed the request.
Content can be filtered by a variety of parameters:
An important function of modern proxy servers is the translation of network addresses (Network Address Translation, NAT), which involves replacing the client's address in the request to the external network with its own address (or several addresses) of the proxy server. This allows you to hide from outsiders the structure of the internal network, the list of addresses used in it. On the other hand, this allows you to have only one legal IP address for the entire local network, which must be assigned to the proxy server. Workstations within the network can have any IP addresses, including those that are not allowed to use in the external network. NAT can be organized in a static and dynamic pattern. With static translation, the client's address in the local network is tied to a specific address that is broadcast to the external network. Dynamic translation presupposes the availability of a range of available external addresses and each time a client requests a proxy server allocates one of the free addresses to represent the client in the external network, upon completion of the transaction this address is returned to the free list and can be used later to send a request to another client. The development of the NAT idea is the translation of port addresses (Network Address Port Translation, NAPT), when the same IP address is distributed during translation to several users and each user is mapped to a packet in the external network with a unique combination of the IP address and the port number of the sender. In other words, the proxy server maps the same IP address to different users of the network, but assigns different port numbers in outgoing requests. This became possible due to the fact that the port of the sender often does not carry any useful information in the request and can be used to uniquely identify the client of the local network for the proxy server.
Modern proxy servers usually perform another important function — information caching. Information sent to the proxy server is stored on local storage devices, and at the next client request, the information requested by it is first searched in the local memory, and only if it is not there - the request is transmitted to the external network. This allows you to reduce the amount of traffic consumed from the external network, as well as reduce the time to access information for the end client.
Consider the properties of the most common proxy servers.
Microsoft Proxy Server (version 2.0) is an expandable feature firewall and information caching server, provides support for the HTTP and gopher protocols, as well as support for client applications (for example, Telnet and RealAudio) for intranet computers using TCP / IP or IPX protocols. SPX, supports VPN, serves as a packet filter. Works in the Windows environment.
Squid is a high-performance caching proxy server for web clients with support for FTP, gopher, and HTTP, with implementations for both Unix and Windows platforms. Squid stores metadata and especially frequently requested objects in RAM, caches DNS requests, supports non-blocking DNS queries and implements negative caching of failed queries. Supports Internet Casing Protocol (ICP), which allows organizing hierarchical caching structures to multiple servers.
In addition to the above, in practice, so-called personal firewalls can be used. They are installed on the user's computer, and all security rules are set for the exchange of this computer with an external network. This allows you to customize the security policy for each individual user directly on his workstation. An example of such an ITU is the AtGuard firewall, which includes proxy server and local packet filter functions. AtGuard is able to block banners, cookies, Java-scripts and applets, as well as ActiveX controls. Another feature of AtGuard is the ability to work in the training mode, when each time you try to connect to a port, permission to establish a connection is requested, and the choice made by the user becomes the rule for further program operation.
The ITU used in practice is an integrated security system that includes both a packet filter and a proxy server. They can be located on one or on several computers, in connection with which there is a possibility to choose the architecture of the used ITU [8].
The architecture of using a computer with two network interfaces as an ITU is similar to a packet filtering circuit (Fig. 5.3), but the ability to route packets should be turned off by the ITU. This allows you to completely block traffic to the external network on this computer, and all necessary services should be provided by proxy servers running on a dual-channel computer. For additional security, you can place a packet-filtering router between the external network and a dual-channel computer. The architecture with a shielded node implies the use of both a packet filter and a proxy server at the same time (Fig.5.5).
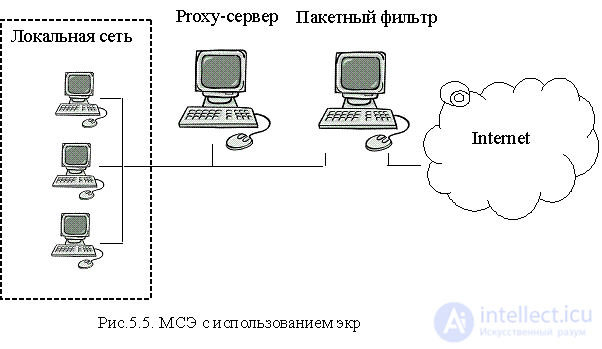
On the border with the external network, a packet filter is installed, which must block potentially dangerous packets so that they do not reach the application gateway (proxy server) and local network. It rejects or allows traffic in accordance with the following rules:
The application gateway must provide proxy server functions for all potentially dangerous services and only one network interface is enough for it to work. Such a firewall connection scheme is more flexible than a dual channel ITU, since a packet filter can allow you to skip requests to reliable services bypassing the application gateway. These reliable services can be those services for which there is no proxy server, and which can be trusted in the sense that the risk of using these services is considered acceptable.
The development of the concept of an isolated node has become an architecture with an isolated subnet. Here two packet filters are used (Fig.5.6) to organize an isolated subnet, which is also called a demilitarized zone (DMZ).
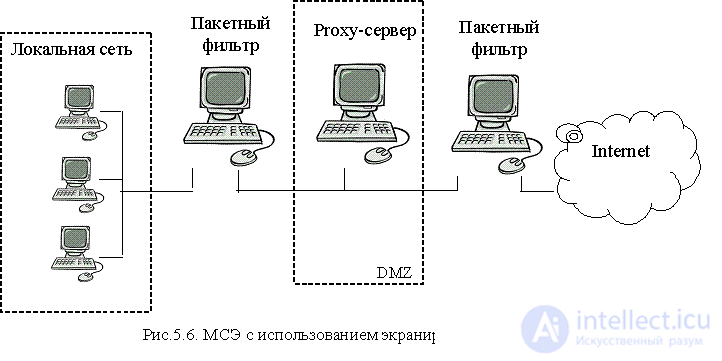
An application gateway should be located inside an isolated subnet, and various information servers (mail, WWW, FTP), modem pools, etc. can also be located. A packet filter installed at the boundary with an external network must filter packets according to the following rules:
The internal packet filter controls the traffic “local network - demilitarized zone” according to the following rules:
This scheme makes it possible to formulate security policy even more flexibly by setting different filtering rules for two packet filters (for example, you can allow FTP packets to pass through the DMZ from the local network to update information on the WWW server and deny access via the FTP protocol to the DMZ from external network). Computers located in the demilitarized zone are subject to more attacks than computers on a local network. Therefore, all computers located in the DMZ should be maximized (bastion host, reinforced computer). All unused services should be removed on them, operating system security tools should be maximally activated (access rights to facilities are tightened, the number of registered subjects is minimized, strict audits are conducted).
Obviously, you can create multiple shielded subnets separated from each other by their own packet filter with the definition of access rules for each of the subnets. The choice of a specific ITU architecture depends on the tasks facing the administrator, the operating conditions, the cost of a particular solution.
Comments
To leave a comment
Information security, Cryptography and cryptanalysis, Steganography and Stegoanalysis
Terms: Information security, Cryptography and cryptanalysis, Steganography and Stegoanalysis