Lecture
As the main classification criterion for cryptographic algorithms, we will use the type of conversion performed on the source text. Classification by this criterion is presented in Fig. 2.1.
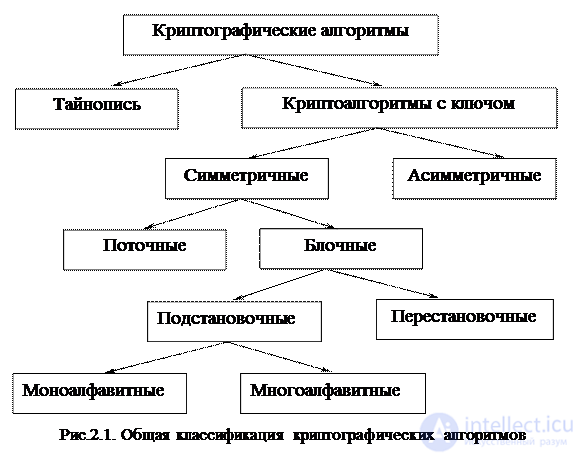
Secret writing assumes that the sender and the recipient perform on the message conversion, known only to them two. Third parties do not know the changes made by the algorithm over plaintext, which is a guarantee of data non-secretability at the analysis stage.
In contrast to cryptography , cryptoalgorithms with a key are based on the principle that the algorithm for influencing the transmitted data is known to all third parties, but it depends on some parameter that is kept secret - the "key" that is known only to two persons involved in the exchange of information. The basis of this approach to encryption was laid at the end of the 19th century by the Dutchman Auguste Kerkhoff, who suggested that the strength of a cipher should be determined only by the secrecy of the key, i.e. The cryptanalyst may know all the details of the process (algorithm) of encryption and decryption, but it is not known which key is used to encrypt this text. Currently, cryptography deals exclusively with algorithms with keys. This is due to the fact that the security of the system should not depend on the secrecy of something that cannot be changed quickly in case of leakage of secret information, and changing the encryption key in practice is much easier than the entire algorithm used in the system.
Key cryptosystems are divided into symmetric and asymmetric encryption systems. The model of a symmetric encryption system is presented in Fig. 2.2.
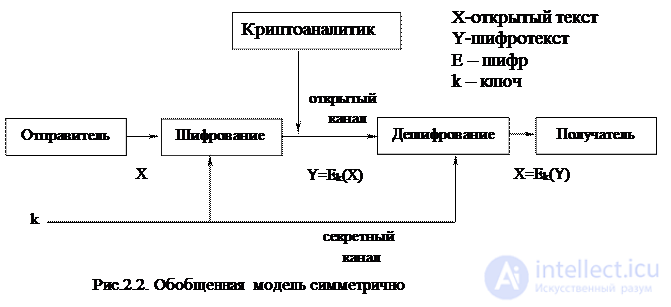
A distinctive feature of symmetric encryption algorithms is the presence of one encryption key (k in Fig. 2.2), which should be known only to the sender and recipient of the message. The sender on the key k encrypts the message, the recipient decrypts the received cipher text with the key k. A cryptanalyst can intercept a ciphertext Y transmitted over open communication channels, but since it does not know the key, the task of opening a ciphertext is very time consuming. The principal point is the need for a secret communication channel between the recipient and the sender to transfer the encryption key without the possibility of its interception by the cryptanalyst.
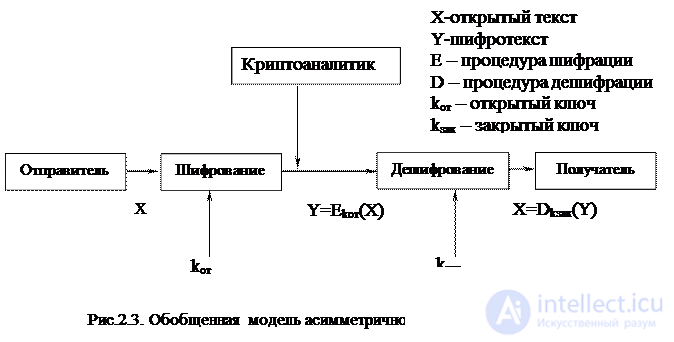
The asymmetric encryption system works according to the scheme shown in Fig. 2.3.
A distinctive feature of asymmetric algorithms is the presence of a pair of encryption keys: open k from , which is transmitted to the second side via an unprotected communication channel and therefore can be known to the cryptanalyst, as well as the closed k zack , which is known only to one person (the message recipient) and is kept secret. A pair of keys has the property that a message encrypted on one of the keys can only be decrypted on another key. In fact, this means that the secret channel for transmitting information in the diagram in fig. 2.3 is the “sender-receiver” direction, since a message encrypted in the public key by the sender can only be decrypted with its private key.
Depending on the block size of encrypted information, cryptoalgorithms are divided into block and stream ciphers. The coding unit in stream ciphers is one bit. The coding result does not depend on the previously passed input stream. The scheme is used in systems for transmitting information flows, that is, in cases where the transfer of information begins and ends at arbitrary points in time and can be interrupted by chance. For block ciphers, the coding unit is a block of several bytes. The result of the encoding depends on all the original bytes of this block. The scheme is used for batch transfer of information and file encoding.
Another criterion for the classification of cryptographic algorithms is the type of transformations performed over blocks of plaintext. By this criterion, cryptoalgorithms are divided into permutation and permutation. In the permutation ciphers, the blocks of information do not change by themselves, but their sequence changes, which makes the information inaccessible to an outside observer. Wildcards modify the information blocks themselves according to certain laws.
The division of cryptoalgorithms into mono-alphabetic and multi-alphabetic is typical for substitution ciphers. Mono- alphabetic cryptographic algorithms replace the input text block (input alphabet symbol) with the same ciphertext block (output alphabet symbol). In multi-alphanumeric ciphers, different ciphertext blocks may correspond to the same block of input text, which makes cryptoanalysis much more difficult.
According to the degree of secrecy cryptographic algorithms are divided into absolutely resistant and practically resistant. Absolutely strong ciphers cannot be opened. In practice, this can be achieved only if the size of the encryption key used exceeds the size of the message being encoded and the key is used only once. A cipher is called practically strong , for which there is no more efficient way of hacking, except for a complete enumeration of all possible encryption keys.
Speaking of attacks on ciphers, we can distinguish the following types of attacks: an attack based on a ciphertext, an attack based on known plaintext, an attack based on selective plaintext.
During an attack based on a ciphertext, the cryptanalyst knows only the coded text and, based on it, he must learn the secret encryption key.
The plaintext attack suggests that the cryptanalyst knows one or several plaintext / ciphertext pairs, encrypted in the same key, and based on this information, he carries out his analysis.
Performing an attack based on selective plaintext, the attacker It has the ability to submit an arbitrary plaintext to the input of the encrypting device and obtain the corresponding encryption code. In order to be called practically resistant, the cryptoalgorithm must successfully withstand any of these types of attacks.
Comments
To leave a comment
Information security, Cryptography and cryptanalysis, Steganography and Stegoanalysis
Terms: Information security, Cryptography and cryptanalysis, Steganography and Stegoanalysis