Audit is a very important element of the security system, allowing to record in special logs events related to the actions of users in the system. Windows supports an auditing system that allows you to select the types of events to be monitored and log them in system logs. The main audit tool in Windows is the Event Viewer utility (Event Viewer). This utility is run from the Administrative Tools folder [16].
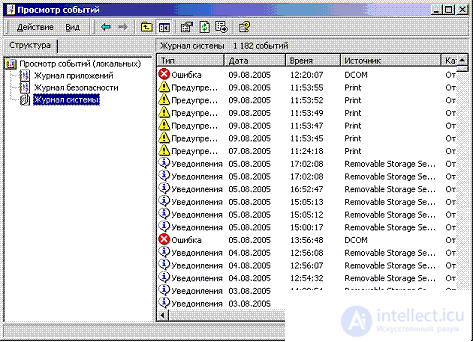
Fig.6.3. The appearance of the utility Event Viewer ( Event Viewer ) Windows
Windows records events in three logs:
- System log - (system log) contains error messages, warnings and other information coming from the operating system and third-party components. The list of events logged in this log is predefined by the operating system and third-party components and cannot be changed by the user. The log is in the Sysevent.evt file.
- Security Log - (Security Log) contains information about successful and unsuccessful attempts to perform actions recorded by means of auditing. The events logged in this log are determined by the administrator-defined audit strategy. The log is in the Secevent.evt file.
- Application Log - (Application Log) contains error messages, warnings and other information issued by various applications. The list of events recorded in this log is determined by application developers. The log is in the Appevent.evt file.
All logs are located in the % Systemroot% \ System32 \ Config folder .
When selecting events for the audit should consider the possibility of overflow log. To configure each log, you can use the Event Log Settings dialog box ( Log Properties, Fig. 6.4)
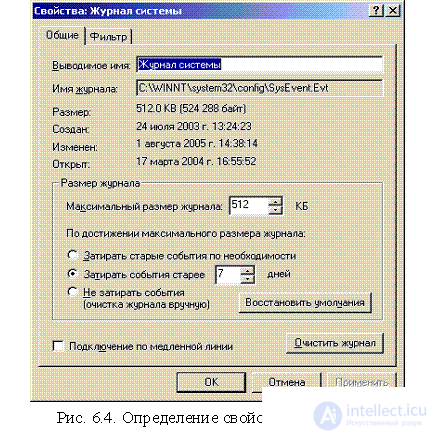
Using this window you can manage:
- the size of archived logs (the default size is 512 KB, you can change the size from 64 to 4 194 240 KB.);
- method of replacing outdated journal entries:
Overwrite old events as needed - in case of filling the log when recording new events, the operating system deletes the oldest events;
Overwrite events older than N days - in case of filling the log when recording new events, the most events are deleted, but only if they are older than N days, otherwise new events will be ignored;
Do not overwrite events - in case of filling the log, new events are not recorded. The log is cleared manually.
Each journal entry contains information about the action performed, the user who performed it, and the date and time of the event. You can audit both successful and unsuccessful attempts to perform certain actions. 5 different types of records are recorded in the log:
- Error Serious difficulties, such as loss of data or functionality. For example, if the service load fails at startup, an error message is logged.
- Warning Events that were not significant at the time of logging, but could lead to difficulties in the future. For example, if there is not enough free space on the disk, a warning is logged.
- Information An event that describes the successful completion of an action by an application, driver, or service. For example, after a driver is successfully loaded, a notification event is logged.
- Success Audit An event corresponding to a successfully completed action related to maintaining system security. For example, if the user logs in successfully, a “Success Audit” event is logged.
- Failure Audit An event corresponding to an unsuccessfully completed action related to maintaining system security. For example, in case of unsuccessful attempt by a user to access a network drive, a “Failure audit” event is logged.
The administrator has the ability to define a set of events to be audited. In Windows XP, this is done in the Audit console policy snap-in. Local security policy The main events that can be logged are:
- Audit login events — Determines whether each attempt by a user to log in or log out on another computer, subject to the fact that this computer is used to authenticate the account, is audited;
- Account Management Audit - determines whether all events related to account management on a computer are subject to audit;
- Audit directory service access — determines whether the event of a user's access to an Active Directory directory object for which its own access control system table (SACL) is specified is audited;
- Logon Audit - determines if each user attempt to log in or log out on this computer, or connect to it through a network, is auditable;
- Object Access Audit - determines whether the event of a user's attempt to access an object (for example, a file, folder, registry key, printer, etc.) for which its own system access control list (SACL) is specified is audited;
- Audit policy change - determines whether each fact of a change in the policies for assigning user rights, audit policies or trust relationship policies is subject to audit;
- Privilege Use Audit — Determines whether each attempt by a user to exercise the right granted to him is subject to audit;
- Process Tracking Audit - determines whether events such as program activation, process termination, repetition of descriptors and indirect access to an object are subject to audit;
- System Event Audit — Determines whether to restart or shut down computer events, as well as events that affect system security or the security log.
Setting up an audit of user access to a particular file or folder is carried out in the property window of this object, the Security-> Advanced-> Audit tab. Using the window interface, you can define events related to the file or folder, the occurrence of which should be reflected in the system log. The list of possible events is displayed in fig. 6.5.
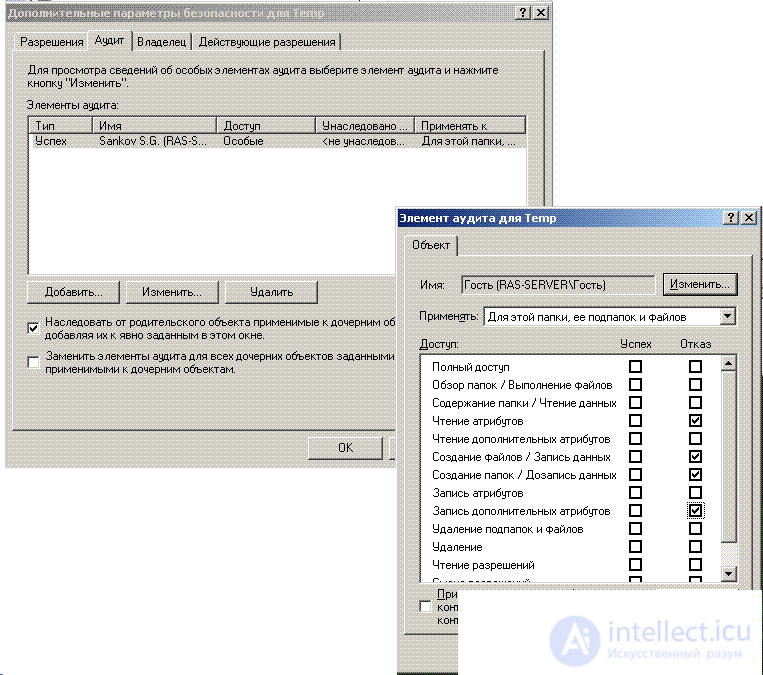
Fig.6.5. Definition of events related to the file to be audited



Comments
To leave a comment
Information security, Cryptography and cryptanalysis, Steganography and Stegoanalysis
Terms: Information security, Cryptography and cryptanalysis, Steganography and Stegoanalysis