Lecture
Consider an example implementation of a firewall. Suppose that there is some organization that has its own local network connected to the global Internet. We assume that the provider has allocated to our organization one static IP address 195.209.133.1. Inside the local network, the administrator can use any of the address ranges intended for use in private networks: 10.0.0.0/8, 172.16.0.0/12 and 192.168.0.0/16. For example, take a range of 10.0.0.0/8. Access to the global Internet will be via a computer that has two network interfaces, one of which is connected to the global Internet and has an IP address of 195.209.133.1, and the second is connected to the organization's local network and has an IP address of 10.0.0.1. Further we will designate this computer with the symbol S. We also assume that our organization has an official WEB server www.myorg.ru and an email server that serves the domain myorg.ru. The server data as well as the main DNS server for the myorg.ru zone will be installed on computer S. The secondary DNS server for the myorg.ru zone is maintained by the provider. In addition, suppose that computer S also has a local FTP server and a proxy server that provides access to the Internet for other computers belonging to our organization. Also suppose that in our organization there are two computers of the advertising department, then R1 and R2, two computers of the sales department P1 and P2, computer director D, computer deputy director Z, two accounting computers B1 and B2, computer personnel department O and demonstration computer W For all computers of the organization, it is necessary to provide access to the mail server, to the local FTP server, as well as to the WWW server of the organization. An exception is the computer W, for which it is necessary to provide access only to the WWW-server. In addition, for computers R1, R2, P1, P2, Z and D, you must provide access to the global Internet through a proxy server.
To fulfill all the requirements presented above, as well as to ensure security and prevent unauthorized access, it is advisable to install a packet filter on computer S. Consider a sample table of rules for our case. Let's assign IP addresses for computers of our organization: R1 - 10.0.0.16, R2 - 10.0.0.17, P1 - 10.0.0.20, P2 - 10.0.0.21, D - 10.0.0.24, Z - 10.0.0.25, B1 - 10.0.0.32, B2 - 10.0.0.33, O - 10.0.0.36, W - 10.0.0.38. Such an uneven distribution of addresses was chosen to enable the use of IP address ranges for computers of different departments. For example, computers in the advertising department belong to the range 10.0.0.16/30. And the computers of the advertising department, sales department, deputy director and director - range 10.0.0.16/28. This grouping greatly simplifies administration and reduces the number of rules for a packet filter. In addition, in this example, left IP address ranges for further expansion of the organization. For example, if computers R3 and P3 appear later, they can be assigned IP addresses 10.0.0.18 and 10.0.0.22, respectively. At the same time, changes in the packet filter rules and other configuration files will be minimal. The entire network of our organization in the classless addressing model will be represented as 10.0.0.0/26. The broadcast address for our local network will be 10.0.0.63. In general, when using private address ranges, the administrator can use any subnet mask available for the selected range. For example, in our case it would be possible to use the network 10.0.0.0/24 with the broadcast address 10.0.0.255. The scheme of the local network described above is shown in Figure 5.7. This scheme implements the architecture of a two-channel computer.
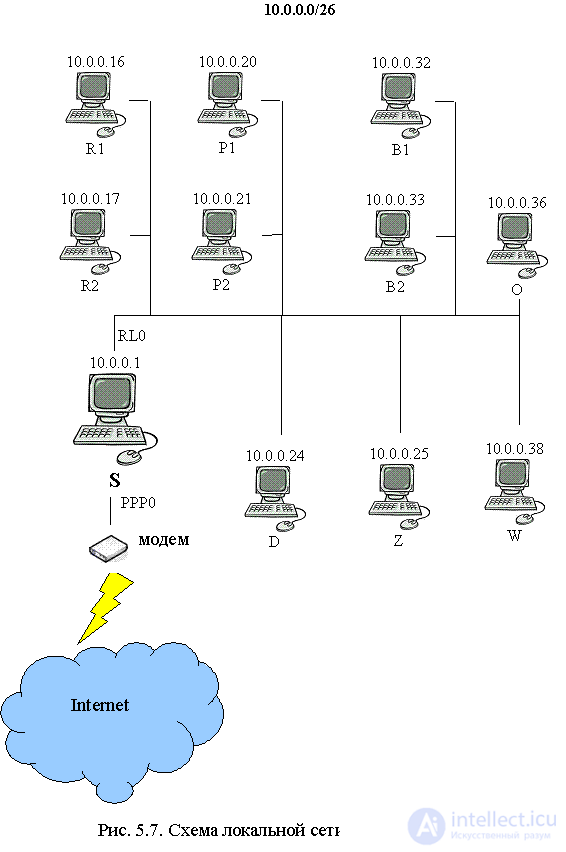
In accordance with all the above requirements and taking into account the assigned IP addresses, we obtain a set of rules for the computer’s packet filter S given in table 5.1. We assume that the proxy server is running on TCP port 3128. This proxy server provides access to WWW servers on the global Internet network running on TCP port 80 using the http protocol and to WWW servers running on TCP port 443 using the HTTPS protocol . In addition, we will assume that the secondary DNS server is supported by the provider and has the address 195.209.133.2. Computer S is connected to the local network via a network adapter, and communication with the provider is carried out using a modem. Further we will denote these network interfaces in the notation of the UNIX family of operating systems, i.e. RL0 and PPP0 respectively. The table below contains the following fields: No. - rule number, “protocol” - protocol stack of TCP / IP protocols (ALL for any protocol running over IP), “Sender.Address” —IP address or range of sender IP addresses of the datagram, “Sender .Port "- TCP or UDP port of the sender of the TCP segment or UDP datagram," Recipient.Address "- IP address or address range of the recipient IP datagram," Recipient.Port "- TCP or UDP port of the recipient TCP segment or UDP datagram," Action " - the action that must be performed if the package satisfies Ravilou (possible options: allow - skip packet, deny - reject packet), “Interface” is the network interface through which the packet is sent or received, “Direction” - packet direction (IN packet comes through this interface, OUT - the packet is sent via this interface).
Table 5.1
Computer packet filter rules S.
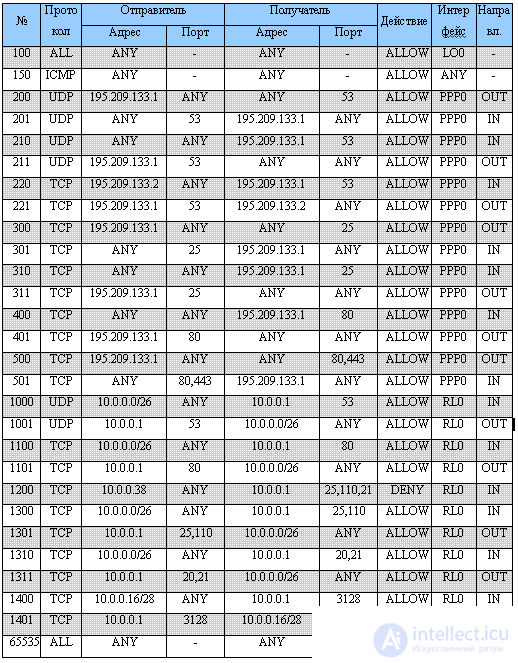
Consider the above rules in more detail. Rule numbers are chosen arbitrarily, however, it should be noted that rules with lower numbers are processed earlier. The order of processing the rules is very important. By default, in most packet filters, if the packet satisfies the condition of the rule, the action specified in the rule is executed and the following rules are not checked. In this example, the odd-numbered rules are “inverse” and allow packets that are responses to the rules with the previous number to pass. In some packet filters, these rules are added automatically, or there are special options for automatically generating such rules. An example would be the use of dynamic rules and check-state and keep-state options in the ipfw packet filter of Unix-based operating systems.
Rule 100 allows all IP datagrams to pass through the local interface. This interface usually has the address 127.0.0.1 and exists on each host and gateway of the IP network. It is necessary for the internal operation of the TCP / IP stack and is also called the local “stub” or local “loop”. This rule also includes all IP packets that have the sender and receiver addresses of any of the local addresses of this computer. For our case, these are the addresses 127.0.0.1, 10.0.0.1 and 195.209.133.1. In other words, this rule allows all the "internal" traffic of computer S. Rule 150 provides the ICMP control message internetwork protocol. This protocol is necessary for the correct operation of utilities such as ping and traceroute, as well as for working with messages about unavailability of a host, network and port, monitoring network congestion, etc. Sometimes it is advisable to prohibit some of these messages, for example, a message with type 5 - message about redirection. Rules 200 and 201 allow our DNS server requests to other DNS servers and are necessary for the correct operation of our caching DNS server. Rules 210 and 211 allow queries from other DNS servers to our primary DNS server. Rules 220 and 221 allow zone transfer between the provider's secondary DNS server serving the myorg.ru zone and our main DNS server. Rules 300 and 301 allow our SMTP server to send mail to other servers. Rules 310 and 311 allow other SMTP servers to send mail to our server. Rules 400 and 401 provide access to the organization’s WWW-server from the Internet. Rules 500 and 501 provide proxy server access to WEB and HTTPS servers on the global Internet. Next come the rules for computers on the local network. Rules 1000 and 1001 provide access for all computers on the local network to the DNS server. Rules 1100 and 1101 provide access for all computers on the local network to the organization’s WWW server. Rule 1200 should be noted. This rule prevents W from accessing SMTP and POP3 mail servers, as well as an FTP server. The following rules 1300, 1310 will allow access to these servers for all computers on the local network, to which computer W also applies. However, since rule 1200 will be processed first, in case of coincidence other rules will not be processed and access to mail and FTP servers organization for computer w will be banned. Note also that there is no “reverse” for this rule. Since the first TCP segment with the SYN flag sent by the computer W, which initiates the establishment of the TCP connection, will be prohibited. Accordingly, the TCP module of computer S will not even be aware of the desire of computer W to establish a connection on ports 21,25,110 and therefore will not generate any response packets. Rules 1300 and 1301 allow access to the SMTP and POP3 server for all computers on the local network. Rules 1310 and 1311 ensure the operation of all computers on the local network with a local FTP server. In this case, only the active mode of the FTP server is allowed. Port 20 was not prohibited in rule 1200, since it is used only when establishing a data connection. And this connection cannot be established without first establishing the connection of commands on port 21. Rules 1400 and 1401 allow access to the proxy server for computers R1, R2, P1, P2, Z and D. In general, these rules allow access to proxy server for computers in the range 10.0.0.16 - 10.0.0.31. Finally, rule 65535 prohibits all other IP packets from passing.
Thus, using this table of rules for a packet filter, we ensured that all the requirements are met. In addition, they excluded the possibility of any attacks or unauthorized access to the computer S both from the Internet and from the local network. The above rule table contains only a basic set of rules. Real tables can contain many more rules and be much more complicated. In this example, the principle “everything that is not allowed is prohibited” was used.
Firewalls are powerful tools for ensuring the security of a local network when it is connected to an external network, providing protection from unwanted intrusions from outside through all protocols of the OSI model. The use of ITU is an integral part in ensuring the security and correct operation of a local area network connected to the Internet. Proper ITU setup allows you to avoid many problems and significantly simplify the solution of other tasks during network administration.
Modern information systems function in conditions of constant threats emanating from the Internet. To protect against these threats, there are many tools at various levels. To ensure the confidentiality and integrity of information transmitted over the global network, you can use secure network protocols that use cryptographic methods. To prevent rejection from the outside, protection against attacks such as DoS, you must use firewalls, whose main task is to filter incoming and outgoing network traffic depending on the adopted security policy.
Comments
To leave a comment
Information security, Cryptography and cryptanalysis, Steganography and Stegoanalysis
Terms: Information security, Cryptography and cryptanalysis, Steganography and Stegoanalysis