Lecture
Each GSM mobile subscriber receives a standard subscriber identity module, a so-called SIM card (SIM — Subscriber Identity Module, SIM card) while using the cellular system.
In the GSM devices (mobile phones) of the GSM standard, a unified removable SIM card is used, the same for all GSM standards: GSM 900, GSM 1800 and GSM 1900 and made in two versions:
- standard (ISO standard) - size 55x85 mm, such as a bank credit card;
- more often, miniature, “plug-in” (plug-in) size of 15x25 mm.
The thickness of the SIM card in both cases is less than 1 mm.
MS without a SIM-card is inoperable, although in this case it is possible to make emergency calls from it to number 112 - the international emergency number.
The SIM module is handed to the subscriber at the same time as the mobile phone and, in principle, allows you to have a conversation from any GSM device, including from a payphone. The SIM card contains the following information:
- PIN (Personal Identification Number) - personal identification number of the subscriber, the so-called PIN-code;
- IMSI (International Mobile Subscriber Identity) - international mobile subscriber identity;
- Ki - individual subscriber authentication key;
- AZ - individual subscriber authentication algorithm;
- AS - encryption key calculation algorithm.
After switching on the MS with the installed SIM card, the subscriber must first unlock the last one - enter the PIN code known only to the subscriber, which should serve as protection against unauthorized use of the SIM card, for example, if it is lost.
After three unsuccessful attempts to dial a PIN-code, the SIM-card is blocked and the lock can be removed either by dialing an additional code - the personal unblocking key (PUK) unlock code, or by a command from the switching center.
The PIN code can be changed at the discretion of the subscriber by agreement with the network operator.
In addition, there is a certain amount of RAM available for the subscriber on the SIM card that allows you to record up to 100 phone numbers with comments (for example, with the names of subscribers) and up to 10 texts of short messages.
When a SIM card is removed from an MS, it stores all the information on it: personal identifiers; keys; ciphers and passwords, as well as telephone numbers and messages recorded by the subscriber, and can work with other MS GSM standard.
Thus, the SIM card “personalizes” the subscriber unit MS, in which it is installed.
Authentication (authentication) - a procedure for authenticating (having rights to use cellular services) of a subscriber of a mobile communication system.
Identification is the procedure for identifying a mobile station, that is, the procedure for establishing its belonging to one of the groups with certain characteristics. This procedure is used to identify lost, stolen or faulty MS.
The idea of the identification procedure in digital cellular systems is to encrypt some passwords — identifiers using quasi-random numbers, periodically transmitted to the mobile station MS from the MSC switching center, and an individual encryption algorithm for each mobile station.
Such encryption, using the same source data and algorithms, is performed both at the mobile station and at the switching center (or at the authentication center), and authentication is considered to have ended successfully if both results coincide.
The GSM authentication procedure is schematically shown in Fig. 4.22. The dotted line indicates elements that are not directly related to the authentication procedure, but are used to calculate the encryption key Kc. The calculation is performed each time authentication is performed.
The authentication procedure is implemented as follows:
- the cellular network (from the AUC center) transmits to the MS some random number R (RAND - Random Number), which is output by the random number sensor in the AUC;
- in the MS cell phone equipment, using the individual Kt key and the AZ authentication algorithm, the resulting number is converted (by mathematical calculations) and the result is calculated (SRES —Signed RESponse), that is, a new number.
- this is the number of Si the mobile station sends back to the switching center, in which this response Si is compared with the value calculated directly at the AUC - S2 center;
- if both values Si and S2 coincide, then the switching center grants permission to get MS access to the cellular network.
- otherwise, the connection is interrupted, and the indicator of the mobile station shows that the identification - authentication did not take place.
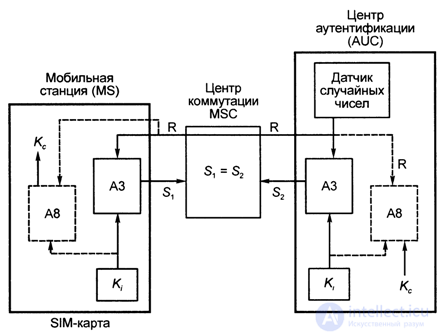
Fig. 4.22. GSM authentication procedure procedure [4.4]:
R - (RAND - Random Number) - a random number; AZ - authentication algorithm;
A8 - encryption key calculation algorithm; Kc - encryption key;
K - authentication key; S (SRES - Signed RESponse) - Encrypted Response
It should be noted that in MS, to ensure the secrecy of the transmitted information, the latter is subjected to encryption.
The algorithm for generating and calculating A8 encryption keys is stored in the SIM card. Simultaneously with the calculation of the response Si, the MS equipment determines the encryption key Xc-This key is not transmitted over the radio channel, but is calculated in AUC and in MS in A8 blocks simultaneously. When transmitted from the side of the AUC authentication center to a random sequence of R numbers, it contains the encryption key Kc. This number is associated with the actual value of the Kc - encryption key and avoids the formation of the wrong key. This number is stored in the MS (SIM-card) and is contained in each of the first message sent to the cellular network.
The identification procedure consists in comparing the MS identifier with the numbers contained in the corresponding blacklists of the network equipment register with the aim of removing the stolen or faulty MS from circulation.
The MS identifier is made so that changing or counterfeiting it is difficult and economically unprofitable.
Comments
To leave a comment
GSM Basics
Terms: GSM Basics