Lecture
Communication security (security), in particular, is protection against unauthorized access to communication channels. Despite the complexity of the technical implementation of cellular mobile communication systems, they are not protected against eavesdropping unless special measures are taken to do this.
In analog systems, it is easier to eavesdrop on transmitted information, in digital it is more difficult, but in both cases this task is technically solvable.
To listen to information in digital cellular mobile communication systems, as noted in clause 8.3, it is necessary to have a highly sensitive radio receiver capable of solving three main tasks:
- tuning to the frequency of the desired radio channel;
- time synchronization (allocation of a certain physical channel, that is, the desired time slot in each frame of transmitted information);
- correct decoding of the selected physical channel information.
It is quite clear that such a receiver is comparable in complexity with the MS subscriber terminal, although its cost is much more expensive than MS due to the small volume of production. To protect against eavesdropping, various methods of encrypting the transmitted information are used. In the GSM standard, the encryption procedure is defined fairly transparently [8.10, 8.11].
Encryption is carried out by noise-resistant coding and interleaving and consists in the bitwise addition modulo 2 of an information bit sequence and a special pseudo-random bit sequence constituting the basis of the cipher.
The definition of the modulo-2 addition operation was given in connection with the description of channel coding (Chapter 4). Repeated application of the addition modulo 2 operation with the same pseudo-random sequence to the encrypted information sequence restores the original information bit sequence, that is, implements the decryption (decryption) of the encrypted message (Fig. 8.2).
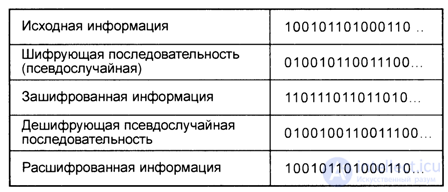
Fig. 8.2. The principle of encryption and decryption of information in the GSM standard.
When assigning the encryption mode, two pseudo-random sequences are simultaneously used: the first —S1 on the forward channel to encrypt information at the BTS base station and decrypt it on the MS mobile station (Fig. 8.3, a), the second —S2 on the reverse channel to encrypt information on the mobile station and decryption at the base station (Fig. 8.3, b).
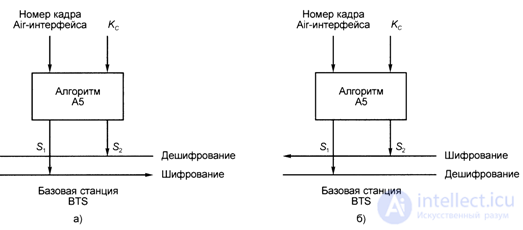
Fig. 8.3. Encryption and decryption of information in the GSM standard.
The pseudo-random sequences 51 and S2 are generated by the A5 algorithm as a function of the frame radio interface number and the encryption key Kc.
Kc is calculated using the A8 algorithm (that is, the encryption key calculation algorithm) using the Kt (authentication key) and R (pseudo-random number) arguments. This is done simultaneously with the calculation of the AZ algorithm of the encrypted response S for the authentication procedure, that is, the encryption key Kc is updated during each communication session.
Thus, although the GSM encryption procedure is really quite transparent, to reproduce it in order to decrypt the encrypted messages is not so easy, since for generating the S1 and S2 sequences in real time, it is necessary to determine the radio interface frame number and the encryption key Kc. In addition, the A5 algorithm is secret. Its description is not included in the general specifications of the GSM standard, and it is distributed under the strict control of the International Association of GSM Standard Operators - GSM MoU Association.
It should be noted that there is also the possibility of protection against eavesdropping: this is the so-called scrambling (scrambling - shuffling, shuffling), which is a kind of encryption by rearranging spectrum segments or speech segments, carried out in an external device with respect to the mobile phone with appropriate descrambling at the receiving end .
Comments
To leave a comment
GSM Basics
Terms: GSM Basics