Modern realities show constantly growing attacks on web applications - up to 80% of cases of system compromise begin with a web application. The article will discuss the most common vulnerabilities that are actively used by attackers, as well as effective methods to counter them using the Web Application Firewall.
As the number of tools and attack techniques increases, it becomes increasingly difficult to ensure the availability of the site, protect the web application or its components from hacking and content spoofing. Despite the efforts of technical specialists and developers, the defensive side has traditionally taken a catch-up position, implementing protective measures after the web application has been compromised. Web sites are subject to attacks due to public availability, not always well-written code, the presence of errors in the configuration of the server part, as well as the lack of control by the information security service, thereby providing attackers with access to critical data.
In this regard, there is a need to use protective tools that take into account the architecture of the web application, and do not lead to delays in the work of the site.
Zero day vulnerabilities
A zero-day or 0-day vulnerability is a previously unknown vulnerability that is exploited by hackers. The origin of the term is related to the fact that the vulnerability or attack becomes publicly known until the software manufacturer releases bug fixes (that is, the potential vulnerability can be exploited on working copies of the application without being able to protect against it).
The nature of zero-day vulnerabilities allows attackers to successfully attack web applications from a few minutes to several months. Such a long period is due to many factors:
- vulnerability needs to be localized and fixed;
- roll out a workable patch;
- notify users about the problem;
- application users to start the process of patch management (which is very difficult to do "here and now" on a large project).
This is another important factor: for the new vulnerability, there may be no rules or exceptions in the defense system, and the signature of the attack may not be recognized by classical defenses. In this case, using the white list of behavioral analysis of a specific web application to minimize the risks of zero-day attacks will help.
An example of the chronology of the Struts2 attack is: CVE-2013-2251 Struts2 Prefixed Parameters OGNL Injection Vulnerability — several days had passed since the emergence of the “combat” exploit, before many companies were able to roll a patch.
However, when using protective equipment, it was possible to identify a request of the form:
http://host/struts2-blank/example/X.action?action:%25{(new+java.lang.ProcessBuilder(new+java.lang.String[]{'command','goes','here'})).start()}
to block the attack, because it is clearly not legitimate in the context of user actions.
"Classic" attacks
Statistics show that many web applications are compromised just as they did years ago - these are different kinds of injections, inclusions, client-side attacks, so a protective tool should be able to detect and block attacks aimed at exploiting the following vulnerabilities:
- SQL Injection - sql injection;
- Remote Code Execution (RCE) - remote code execution;
- Cross Site Scripting (XSS) - cross-site scripting;
- Cross Site Request Forgery (CSRF) - intersite request forgery;
- Remote File Inclusion (RFI) - Remote Inclusion;
- Local File Inclusion (LFI) - local inclusion;
- Auth Bypass - authorization bypass;
- Insecure Direct Object Reference - insecure direct object links;
- Bruteforce - password selection.
In an ideal web application, this kind of vulnerability should be detected and fixed even at the design stage: a static, dynamic, interactive analysis should be performed, and anomalies in the application logic should be detected. But, often, such moments for one reason or another are lost sight of, there is no time or money left for them.
Application Security
Web applications differ from ordinary applications in two things: a huge variety and significant interactivity. This creates a whole range of new threats that traditional firewalls cannot cope with.
Application Layer Protocol - the protocol of the upper (7th) layer of the OSI network model, provides for network and user interaction. The level allows user applications to have access to network services, such as a database request handler, file access, e-mail forwarding. Protection at the application level is the most reliable. Vulnerabilities exploited by hackers often rely on complex user data entry scenarios, making them difficult to detect using classic intrusion detection systems. Also this level is the most accessible from the outside. There is a need to understand the groups of protocols and dependencies peculiar to web applications that are built on the http / https application protocols.
The basic principle of site security at the application level is the verification and filtering of request data transmitted by the GET, POST, etc. methods. The substitution or modification of a request is the basic basis of almost all methods of hacking and site attacks.
Attack targets
Web applications can be attacked regardless of their affiliation to a particular area of activity: low traffic sites that fail to handle large amounts of information and do not store critical data can be attacked as a result of inappropriate attacks. Significant sites with high traffic, huge amounts of user data, etc. are an attractive target for attackers and are attacked almost daily:
- Every third site has been hacked or hacked;
- 80% of sites are hacked during untargeted attacks using popular scanners or utilities;
- About 60% of hacked sites were infected and blocked by search engines.
For sites operating with payment data processing online transactions there are specialized requirements for compliance with the PCI DSS standard. Payment Card Industry Data Security Standard (PCI DSS) is a data security standard for the payment card industry, developed by the Payment Card Industry Security Standards Council (PCI SSC) established by the international payment systems Visa, MasterCard, American Express, JCB and Discover.
Clause 6.6 states that in addition to conducting an audit of a web application, it is necessary to ensure the use of specialized protective equipment:
Understanding the 6.6, we should refer to it.
It is a fact that it is important that it is important.
PCI DSS proposes two ways to achieve this requirement:
“Reviewing public-facing web applications
“Installing an automated technical solution for web-based attacks (for example, a web-based application firewall) and for all web-based firewalls.
Clause 6.6 is mandatory if the web application is included in the CDE (Cardholder Data Environment).
Site security
The best solution to protect the site is to use Web Application Firewall - an application-level firewall that allows you to effectively protect sites from malicious attacks.
Web Application Firewall is a special mechanism that imposes a specific set of rules on how the server and the client interact with each other, processing HTTP packets. It is based on the same principle as in regular user firewalls - the control of all data that comes from outside. WAF relies on a set of rules by which the fact of an attack by signatures is revealed - signs of user activity that can mean an attack.
How it works
The Web Application Firewall operates in the transparent proxy mechanism, analyzing incoming data from the client on the fly and discarding illegitimate requests:
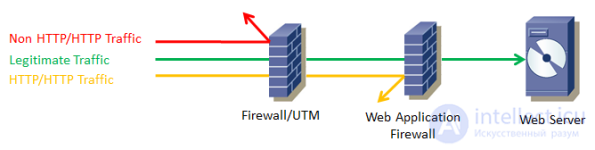
After installing the Web Application Firewall, the settings for the target web application are necessary - depending on the type and type of CMS, web application-relevant filtering settings and rules are added and the protective tool is transferred to the learning mode to collect reference models of communication with the web application, identifiers and .d
After the machine learning stage, the combat mode is activated, which operates with both ready-made filtering rules and practices collected during the training phase to detect and block attacks.
The effectiveness of a Web Application Firewall is made up of several factors:
- Easy integration into infrastructure;
- Flexible adaptation system with web application;
- Block threats OWASP Top 10;
- Analysis and blocking of protocol or data anomalies;
- Detection and blocking fake session IDs;
- Detection and blocking of passwords;
- Inspection of server responses for critical data;
- Dynamic update attack signatures;
- Low number of false positives
- WAF self-defense;
- Convenient information service about attacks;
- Statistics and regulatory reporting.
One of the sources that allows to identify new scenarios and the implementation of attacks on web applications is the "Penetration Testing Laboratories", which imitate the real infrastructure of modern companies. About 9,000 information security specialists from around the world, with varying levels of training, skills and tools, take part in the laboratories. Analysis of attacks aimed at laboratory objects allows us to make models of the offender and the implementation of attack vectors.
These data are carefully analyzed and on their basis new filtering rules are added. Thus, our solution is able to provide complete protection of the site from various types and types of attacks.
Nemesida WAF is an application level firewall (Web Application Firewall) that allows you to effectively protect sites from hacker attacks even if there is a zero-day vulnerability on the site.

Comments
To leave a comment
Information security, Malicious, and information security
Terms: Information security, Malicious, and information security