Lecture
Over the past 2 years, the number of DNS attacks in cyber reality has almost doubled. This tendency is by no means accidental and brings the relevance of this type of attack to a single row with a giant like DoS / DDoS. This is not surprising, given the similarity of DNS and DDoS attacks.
There are a lot of questions in this topic. And besides the obvious (what dangers are concealed in the DNS protocol and attacks on it), another comes to mind immediately - a more paradoxical one: why do we still use an unsecured open UDP protocol in such an important and integral part of the network as DNS? on which DNS is implemented)? One can guess at the answer for a long time, but the majority opinion, like my personal one, boils down to ordinary disorder and laziness of modern IT representatives. Although in recent years the solution to the problem of combating DNS-attacks are beginning to emerge and be implemented in the practice of IT-offices. But first things first. Actually, what types of DNS attacks are there and how can you resist them?
The basics of the DNS protocol and basic DNS attack patterns are described in an earlier DNS attack article: basic patterns and principles. And in the current we will talk in more detail about the specific implementation schemes and how to protect against attacks on the DNS protocol.
2012 is considered to be the year of DNS attacks, in which not only their number significantly increased, but, more importantly, they became more sophisticated and began to entail more serious consequences.
Why has the popularity of DNS attacks increased? The answer to lies in the recent history of DoS / DDoS attacks. DoS / DDoS attacks appeared simultaneously with the advent of the Internet itself and since then they have not yielded their leadership to almost anyone: until 2010-2011 there were practically no real ways of protection from them (yes, there are almost no them now, to tell the truth: there is only more sophisticated ways of implementation). But obviously they took the leading position among other hacker attacks in the second half of 2010: just at that moment when the notorious group Anonymous chose them as their main tool. At first, no one was ready for them, and any attacks by intruders reached their goal.
The situation changed by the end of 2011, when organizations began to introduce reflection systems to counter DoS / DDoS attacks, which led attackers to look for new ways to achieve their same goal and show great ingenuity. And such ingenuity was found: a new attack vector headed for the DNS server. In 2012, the annual growth in the number of DNS attacks is observed at 170%. Almost half consists of reflex DNS-attacks that use the reflection of requests (including recursive queries), for the implementation of which does not even require the presence of a DNS server from the organization-victim.
DNS attacks are a natural step in the evolution of the DoS / DDoS attacks in general. If the IT consciousness of the IT world used to perceive DDoS as attacks, for the effectiveness of which a rough storm of a large number of requests (traffic) is required, now DNS attacks show the opposite: their complex types can be asymmetrical and be powerful and destructive with relatively low speed of implementation and intensity of exposure. Such a use of DNS attacks for DoS / DDoS implementation is just one of the possible threats. There is one more important type of consequences, which will be discussed further.
There are three types of threats in this case. And they are tied to the 3rd classic elements of the information security triangle: integrity, availability, confidentiality.
So, the types of threats of DNS attacks:
1. Violation of the availability of web-resources when referring to the DNS-name.
2. Interception of almost any passing traffic (by target resources).
3. Substitution of a trusted network object / substitution of network requests / responses.
With type 1 everything is clear, but we will look at 2 and 3 with an example.
Suppose a victim (that is, one of us) wants to log into his account on a trusted site and perform some kind of operation (mail, Internet bank, social network, ...); sends a DNS query in a browser or special program (for example, RBS); receives a false DNS response from the IP address of the hacker's server, on which the same resource / service that the client needs is deployed; the client enters his login and password on the hacker's website, which, naturally, are remembered by the attacker's server and then sent to the real service, where the hacker receives a response about successful authorization and subsequent authorized pages that he simply transmits back to his victim, thus becoming an intermediary between the real resource and sacrifice. Thus, the hacker will not only see all the traffic, he can also replace any requests (for example, the addressee of the recipient of the transfer of funds in the Internet Bank, if this bank does not use EDS authentication). The possible consequences of such an attack scheme do not need explanations.
Consider the basic schemes of DNS attacks used in modern times:
1. Substitution DNS-response; implementation of a false DNS server.
Goals and threats: substitution of trusted network objects; interception of virtually any victim traffic; substitution of network requests / responses.
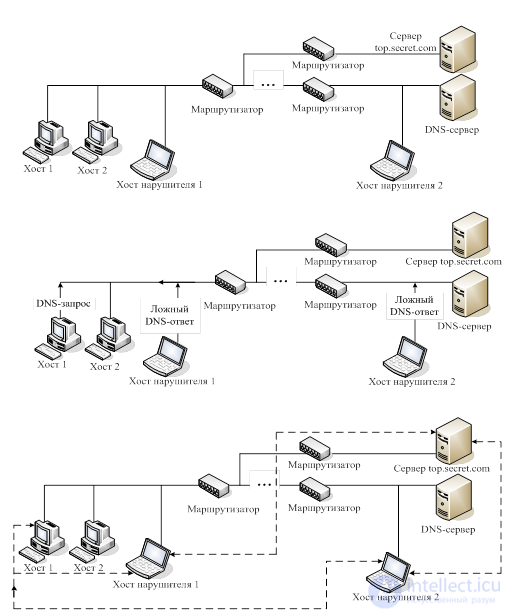
The scheme of the attack if there is access to the victim’s traffic (the case in the picture):
The scheme of the attack if there is no access to the victim’s traffic:
If the attacker is behind a separate router and does not have access to client traffic, but is in the same network segment as the victim's DNS server (the victim itself), the scheme remains almost the same. Phase 1 is replaced by the phase of a massive sending of DNS-answers, without waiting for the request of the victim. In this case, the victim immediately after the request will receive a response, one of which will be correct.
It should be noted that this threat is based on the use of shortcomings of remote search algorithms. If network objects initially do not have address information about each other, various remote search protocols are used (for example, SAP on Novell NetWare networks; ARP, DNS, WINS on networks with the TCP / IP protocol stack), which consist of transmitting special requests and receiving answers to them with the information sought.
2. Attack on the DNS server cache / substitution of the upstream DNS server (Kaminsky attack).
Goals and threats: substitution of trusted network objects; interception of virtually any victim traffic
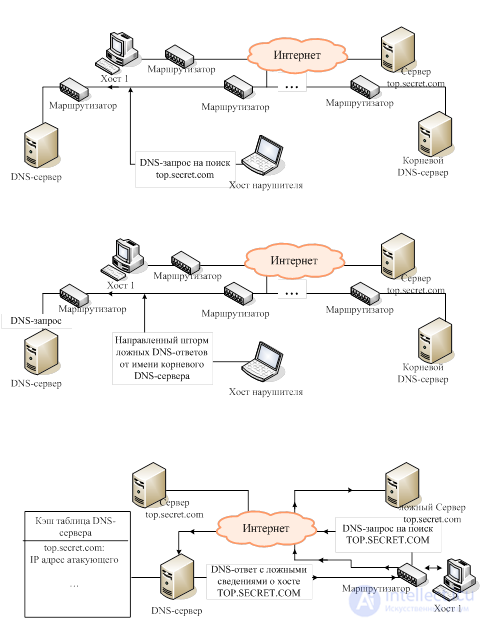 The scheme of the attack:
The scheme of the attack:
Important note: as a result of the attack, the substitution of target DNS responses (IP addresses of DNS names) occurs not only for one victim host, but for all users of this DNS server!
3. Attack by means of reflected DNS requests.
Goals and threats: deactivating the victim’s host (including the DNS server); the fall of the gateway (Internet access channel) / firewall.
An attack using reflected DNS is based on the fact that a DNS response is always 3-4 times longer than a query. In some cases (for some DNS names) the size of the response packet may be 10 or more times the size of the request. Thus, due to this fact and the use of UDP-protocol, the following scheme of attack on an arbitrary host on the Internet became possible.
The scheme of the attack:
As can be seen from the diagram and description, this type of attack can be organized in conditions of rather limited resources, reaching a 4-10-fold effect of enhancing the attack. If, at the same time, the attacker also creates certain domains that require DNS packets of enormous size to be sent, then by sending requests only to such domain names, the attacker can reach a 100-fold increase in the effect of the attack.
In fact, this type of attack is an evolutionary type of ordinary DDoS.
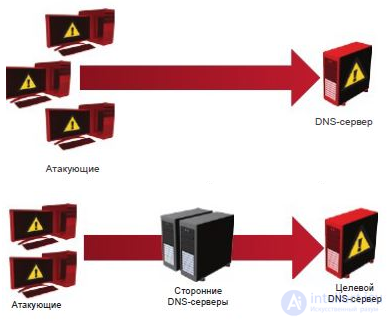
4. DNS flood attacks, attacks with recursive DNS queries / Garbage attacks.
Goals and threats: removing the DNS server - the victim - out of order.
The basis of these types of attacks is a simple DNS flood: a lot of attacker's hosts send a massive stream of requests to the target DNS server with a false SRC IP (the IP address of the source of the request). A standard computer is capable of generating 1000 requests per second, a standard DNS server is capable of processing 10,000 requests per second. By not requiring a lot of brain computation, we come to the conclusion: 10 ordinary home (or not quite home) computers are quite enough to disable the DNS server. Moreover, it will be very difficult to calculate the attacker.
The attack of the Garbage-DNS type is based on the constantly open 53 port (standard DNS port, sometimes the 80th port is used). The attack scheme is reduced to an attacker sending (from multiple hosts) large (over 1500 bytes) network packets (not necessarily DNS). Thus, it all comes down to normal DDoS, but to the DNS port. The advantage over ordinary DDoS is that the 53rd port (DNS port) is always open in any organizations, because it is needed for the DNS system to work.
A recursive DNS attack is reduced to identifying the set of non-existent in the cache DNS servers of the victim names (possibly false) and then sending DNS queries with the names from this set. As a result, the DNS server is forced to send such requests to all neighboring and upstream DNS servers in order to obtain the IP of the ordered host. As a result, the server has to send a whole set of DNS requests to other servers for each request and receive answers from them, which sometimes cost hundreds of times more resources than sending a single DNS request. In the igog, as in the previous type of attacks, having very little resources at all, it becomes real to implement a sufficiently powerful DDoS attack on the DNS server (as opposed to reflected DNS attacks, the goal of which can be not only the DNS server).
A natural question arises: how to protect against this type of attack, which, it would seem, all DNS servers are subject to without exceptions? (in particular, the good old conservative, but nevertheless very popular BIND) It turns out that there are ways. About them in detail in the next article ...
DNS attacks are an old, but still relevant area of hacker research, representing in many cases a serious danger today for almost any business. Given that the DNS DNS protocol has not changed much since the early 80s, and it was developed without any security considerations, and modern IT tools and hacker minds have improved significantly, the problem becomes even more urgent. In particular, the protection of business becomes relevant in the context of this IT threat. The types of DNS attacks existing in the modern world can lead not only to the theft of financial information (both a private person and a company) or a trade secret, but also to the theft of finances themselves, both explicitly and literally (for example, through the substitution of network packets in the RBO) ) and indirectly (trade secrets and competitors). Do not take into account this type of attack, it means to make a serious mistake in the strategic planning of the company's business.
In the previous article, we looked at all the main types of DNS attacks that currently exist and the threats they carry. This article will analyze the possible risks and ways to protect against DNS attacks.
Based on the many types of DNS attacks (discussed in the above article), you can conduct a consistent analysis of the risks associated with threats to the DNS protocol.
So, the risk analysis table :
|
No |
Threat description |
Probability (complexity) of implementation |
Damage |
|
one |
Non-compliance with legislation on PDN for new SPDN. (p.8.10 (requirement ZIS.15) of the Order of FSTEC №21) |
High |
Tall. For new ISPDN: recognition of IP inappropriate; suspension of the IP. |
|
2 |
For the case of being in the network segment of a user and / or DNS server (and, accordingly, access to its traffic): replacing the DNS server with its own false server and then sending false DNS responses. Example of implementation: the substitution of any web-service organization with password authentication false, reading passwords, then redirecting to a real web-service and sending users received answers (transparent to the user and effective for the attacker). All passwords will be stolen, any requests to the service can be replaced with false ones. |
Medium high (within user network segment) |
Very tall. Replacing all network resources that have dns-names with their own, which means getting access to the user's information (including his passwords). Interception of all user traffic. Substitution of any network requests. |
|
3 |
For the case of being at an arbitrary point in the network (without direct access to the victim's traffic): sending a squall of false DNS responses with the substitution of the DNS server IP and selection of the port and user ID (at any point in the network). Further, raising your own DNS server and duplicate service is analogous to risk in clause 2. |
Average |
Similar to p.2. |
|
four |
For the case of being at any point on the network (possibly without access to the victim and in the absence of their own DNS in the organization): sending a query that is not in the cache of the DNS server and a subsequent flurry of false DNS responses on behalf of (IP) superior (possibly the root) DNS server to a downstream (DNS server of the victim), which entails a change in the cache table of the downstream DNS and the subsequent strategy of replacing services similar to the risks of paragraphs.2-3. |
Medium high (works in case of a dns request that is not in the current DNS cache; there is no condition for being inside the organization’s network) |
Similarly to p.2 |
|
five |
For an arbitrary case (the location of the attacker does not matter; the attack is applicable to any hosts of the organization accessible from the external network): an attack by means of reflected DNS responses. The attacker sends a series of DNS requests with the sender's spoofed IP (on the victim's IP) to multiple DNS servers. The request contains names with a DNS response elongation ratio of 10 and up (up to 100). As a result, a massive DDoS attack occurs. |
Medium high (does not use intranet resources; does not require being inside the organization’s network) |
Tall. High damage to the violation of the availability of an arbitrary host, looking to the external network. |
|
6 |
For the case of having your own DNS server in the organization: DDoS attacks on the DNS server: simple DNS flood; recursive DNS attack; Garbage attack. The result: a complete fall of the DNS server. |
Medium high (in case of existence of own DNS server; it does not require being inside the organization’s network) |
Medium / High. High damage to the violation of the organization's DNS server (easy to recover). In the absence of a backup DNS, the entire network is disrupted. |
Items 2-5 are based on the easy formation of a DNS-UDP packet with the ability to easily insert arbitrary data by IP, ID, etc. into the packet. A more detailed description of the threats of paragraphs 2-6 is contained in the previous article, DNS attacks: a full overview of attack patterns.
As can be seen from the table, there are very serious risks in this area and they need to be processed. Let us proceed to the description of methods to combat the threats of DNS attacks and assess the effectiveness / preventiveness of these methods.
Methods of protection come down to two main areas: the proper configuration of the DNS server and the use of the DNSSec protocol. We describe both options.
So, the necessary (but not sufficient) DNS server settings:
As for the DNSSec protocol, this is quite a powerful tool, the essence of which comes down to using a whole public key infrastructure (PKI) to authenticate any domain messages with building a chain of trust. All requests and responses are signed by their EDS, the authenticity of which is provided by the corresponding CA certificate. In the context of such a measure, risks 1, 2, 3, 4 (in the case of using DNSSec on upstream servers) and - partially - risk 6 become irrelevant. In one fell swoop. There remains a risk of 5, but it is unrealistic to overcome it by the forces of one organization. It can only be reduced through the ubiquitous use of the DNSSec protocol.
The question of prevention is becoming, i.e. benefits of implementing a new protocol for business. It must be said that the protocol itself is open, free and supported by almost all modern DNS servers (including BIND) and client OS (including Windows 7 and Windows 2008 Server).
So, the problems of implementing DNSSec:
As can be seen from the list, the problems of implementing DNSSec are associated with correct software configuration (which can be easily solved) and increased requirements for the hardware resources of DNS servers, as well as the Internet channel (although this largely depends on the size of the organization).
Summing up, we can say that the implementation of the DNSSec protocol seems to be justified for medium and large business organizations with high criticality of access to the Internet and / or the use of critical network services. For small business organizations that do not use the cloud architecture or other similar services, the use of such a protocol depends on the specific situation and requires individual consideration.
Comments
To leave a comment
Information security, Malicious, and information security
Terms: Information security, Malicious, and information security