Lecture
Plan.
a) Mainframe Operating Systems;
b) Server operating systems;
c) Multiprocessor operating systems;
d) Operating systems for personal computers;
e) Real-Time Operating Systems;
e) Embedded operating systems.
a) Birth;
b) Portable UNIX system;
c) Berkeley;
d) Standard UNIX system .
a) Authorization in UNIX;
b) UNIX file system;
c) UNIX system interfaces;
d) UNIX shell
e) UNIX utilities;
Mainframe operating systems At the top level. Different from personal computers in their input-output capabilities. Thousands of disks - terabytes of data. Powerful web server, server for large-scale commercial sites, server for transactions.
Focused on processing multiple simultaneous tasks that require a huge number of input-output operations. There are three types of services: batch processing, transaction processing (group operations), time sharing.
MULTICS - the system was developed in order to provide hundreds of users with a machine "in power than the Intel 360, although it has the ability to work with hundreds of input / output devices. There were many constructive ideas for computer theorists, but it was not possible to turn it into a serious commercial product. Nevertheless, General Motors, Ford and the US National Security Authority left MULTICS only at the end of the 90s, that is, 30 years after the release of the system. The site www.multicians.org is devoted to it with a lot of information about the system, its designers and users.
The idea of a public computer enterprise is Internet servers that administer “stupid” user machines.
processing performs tasks without the presence of users. (Reporting on sales in stores, processing claims of insurance companies.) Transaction processing systems manage a very large number of small queries, for example, working in a bank, managing the sale of airline tickets. A separate request does not require large resources, but the system must serve thousands of such requests per second. Time sharing systems allow multiple remote users to simultaneously perform tasks on a single machine. For example, work with a database.
All of the above functions are closely related. Often, the mainframe OS performs them all. Examples of such OS / 390 OS derived from OS / 360.
Server operating systems . They are at a lower level. They work on servers representing very large personal computers, workstations, mainframes. Servers provide the opportunity with printers, files or the Internet. Typical server operating systems are UNIX, Windows 2000, and more recently Linux. At the same time, many users are served, allowing them to share hardware and software resources among themselves. The servers store web site pages and process requests (UNIX and Windows are typical server operating systems).
Multiprocessor operating systems . A way to increase computer power. Depending on the type of connection of the processors and the division of work, such systems are called parallel computers or multiprocessor systems. Requires special operating systems. However, often these operating systems are options for server operating systems with special features.
Operating systems for personal computers . The goal is a convenient interface for one user. Widely used for working with text, spreadsheets, Internet access. ... + Macintosh. From 1980 to the present day. started with an 8-bit microcomputer with a CP / M disk. It holds the highest position in the world for 5 years. MS-DOS and SR / M for the first microcomputers were completely based on typing commands from the keyboard. In the 60's, Doug Engelbart conducts research on a graphical user interface consisting of windows, menus, buttons, and a mouse.
Then Steve Jobs, Apple developer, came up with an idea-friendly graphical user interface (Macintosh).
Windows first 10 years of work from 1985 to 1995 played the role of a graphical environment on top of MS-DOS. 1998 slightly modified version of windows but many 16-bit processor programs
Windows NT kernel is written completely anew - 32 bits completely. Windows NT 5.0 was renamed Windows 2000 in early 1999. + Windows
ME (Millenium edition)
The main rival of Windows in the world of UNIX desktops is the most powerful system for workstations and network servers. For high-performance RISC processors and Pentium. Massachusettsky University developed graphics - X Windows, on top of it you can install the full graphical Motif interface
Real-time operating systems. Must meet stringent time requirements - production. Hard real-time systems - the action must occur at a specific point in time or within a specified range. A flexible operating system — in which there are admissible occasional missed deadlines for the operation. For example, digital audio and multimedia systems. VxWorks and QNX systems are real-time systems.
Embedded Operating Systems A pocket computer (PDA - Personal Digital Assistant - personal digital assistant) - a notebook or notebook. Embedded systems run on machines that are not usually considered computers, such as televisions, microwave ovens, and mobile phones. The same characteristics as real-time systems, but have a special size, memory. Examples: PalmOS Windows CE (Consumer Electronics - household appliances).
Operating systems for smart cards. The smallest is a credit card-sized device containing a central processing unit. Severe restrictions on processor power and memory. Are proprietary.
Some smart cards are java oriented. This means that the ROM contains an interpreter of the Java virtual machine machine. Java applets are loaded onto the map and executed by the JVM interpreter. Some cards can manage multiple Java applets simultaneously, multitasking is a need for planning. All these tasks are performed by the operating system located on the smart card.
Birth The 40s, 50s , all computers were personal in a sense, the whole machine was at the disposal of a certain user. The next step is time-sharing systems - MULTICS ( multiplex information and computing service). The system divides time between hundreds of users.
On PDP-7, Ken Thompson writes ONE, a user OS, which was jokingly called UNICS, a primitive information and computing service (Uniplexed Information and Computing Service), which later became UNIX.
After that, two technological improvements. First, it was transferred to the new PDP-11/45 11/70 hardware ( 256 KB and 2 MB). Memory hardware protection - simultaneous work of several users., 16-bit machines.
Secondly, rewritten in C.
The operating system was delivered with a complete set of documents. As a result, new ideas and improvements to the system spread with great speed. The source text consisted of 8200 lines in C and 900 lines of assembly code.
By the middle of the 80s, UNIX OS on mini-computers and workstations. Source licenses are purchased, one of such Microsoft companies - XENIX.
Portable UNIX system - Steve Johnson. Portable C compiler. The compiler can be configured to create object code for almost any machine. With a moderate amount of work. Transfer to Interdata and VAX computers.
Berkeley . The University of California creates a version designed for 32-bit VAX machines. Contained a large number of improvements. Using virtual memory, paging files - programs are created larger in size than physical memory. Support for file names over 14 characters. In the 4th version of BSD network support, with the result that the TSP / IP protocol has become the de facto standard in the UNIX world.
The university has added a new editor, a shell shell, compilers for the Pascal and Lisp languages. The result was the production of computers based on the Berkeley version.
Standard UNIX system . By the end of the 80s, two, somewhat incompatible versions of BSD 4.3 and SYSTEM V Release 3 were widely distributed. There was no standard for the binary format of the programs, manufacturers could not create programs that would work on any UNIX operating system.
The IEEE Institute of Electrical and Electronics Engineers Standards Board is developing a POSIX (Portable Operating System) + IX project that makes the name uniconomic. Standard 1003.1 is a set of library procedures that each UNIX system must comply with that standard. The software manufacturer uses only procedures that comply with this standard, ensuring work on the corresponding OS, for example, open, read, fork.
The rift in the UNIX world. IBM, DEC, HEWlett-Packard –OSF (Open Software Fondation) = standard + additional properties (window system, graphical user interface, distributed computing, distributed control).
AT & T Corporation, in response to this, creates a consortium of UI (UNIX International) to produce the same. The UI version is based on SYSTEM V.
Again two versions of UNIX. The market decided that SYSTEM V is better.
Andrew Tanenbaum, a professor from Holland, writes a Unix-like OS consisting of 11,800 lines in C and 500 lines in assembler. With full source text offers it to students for educational purposes. Released in 1987, functionally almost equivalent to Version 7 UNIX.
Based on the microkernel design. The idea of m / i is as few functions as possible in the kernel. Memory and file system management tasks are moved to user processes. The kernel handles the transfer of messages between processes, without being engaged in other tasks.
The kernel consists of 1600 lines on With and 800 assembly lines. The device drivers are also in the kernel, 2900 lines in C. The file system of 5100 lines in C and the memory manager in 2200 lines in C worked as two separate user processes.
The MINIX system has become an object of worship, 40,000 users, there is a comp.os.minix conference. Became a prototype of collective work. In 1997, the second version of the system was released. About her book is written +500 pages of source code in applications + CD. Available free of charge at www.cs.vu.nl/~ast/minix.html.
4. LINUX
Linus Torvalds writes another UNIX clone, which he himself called LINUX. The goal is to complement MINIX with more complex functions. The first version of the year 1991. Designed and compiled in the MINIX system, borrowed some of the ideas of MINIX - the source tree and file system structure.
The difference is a monolithic system, that is, the entire operating system was placed in the core. The source text is approximately 9,300 lines in C and 950 lines in assembly language. Functionally practically did not differ from MINIX.
It quickly grew into a full-fledged UNIX clone with virtual memory, a complex file system, etc. Works on a wide range of machines as well as UNIX. One of the main differences is the use of the gss compiler to compile it with standard ANSI C requires a lot of effort.
1994.- version 1.0. 165,000 lines of code — mapping files to address space BSD-compatible network software with sockets and TSP // IP.
Version 2.0 1996 –470,000 lines of code and 8,000 lines of assembly text. Support for 64-bit architecture, symmetric multitasking, new network protocols + driver collection.
The standard UNIX software has been transferred to the system, including the X Windows window system and most of the network software. In addition, two different GNOME and KDE GUIs were written specifically for LINUX.
Business model: freeware software. You can download from various sites, for example, www.kernel.org. License of a fund of free distributed programs: users are free to use, copy, modify and distribute further source texts and binary files. Prohibit the sale or distribution of binary code without similar texts.
So, strict compliance with the POSIX standard, the intersection of the user community has led to the fact that many features of LINUX - system calls, programs, libraries, internal data structures are very similar to their counterparts in UNIX. For example, more than 80% (150 s / v) are exact copies of the corresponding POSIX, BSD, SYSTEM V calls.
Thus, in a first approximation, most of the description of the UNIX system, given below, also applies to Linux. In those places where UNIX and Linux will differ significantly (for example, in the scheduling algorithm), both options will be specifically noted and explained. Where there will be no serious differences, we conditionally call it UNIX.
5. Overview of UNIX
Login to UNIX. It was created by programmers for programmers, in most cases actively cooperating with each other in creating a single project - a group. ACL (Access Control List) - Access Control List:
1) The rights of the owner of the user;
2) Rights of the group;
3) Default rights
As a rule, the host name is higher than the group rights, and the rights of the group are higher than the default rights, but this is not a requirement and is not verified in any way. A user can belong to several groups at the same time; a file always belongs to only one group.
Three rights read, write, execute. Execution for the directory - the right to open files in this directory. Rights bits in the access mask.
The right to delete does not exist, there is only the operation of deleting the name - unlink. A file can have several names, the deletion itself occurs when the last name is destroyed. To delete, create, or modify an IME file, it is sufficient to have write access to the directory in which it is contained.
In addition to the rights listed in the mask, the owner of the file is allowed to change the rights to the file: modify the rights mask and transfer the file to another group.
Another rights holder is the administrator. It has the ability to do anything with the presented objects in the system.
All global objects — external devices and named pipes — are files and access control to them is performed by the file mechanism.
UNIX file system . On UNIX, mounted file systems look like directories of a single tree. The tree begins with the root directory, dedicated FS, called root. The system administrator can mount a new file system to any directory located at any level of the tree. Such a directory is called a mount point, but this expression reflects only the current state of the directory.
This approach has an obvious at first glance, but a serious advantage over separate namespaces for different physical file systems. The reason is that the namespace is not related to the physical location of the files. That is, the system administrator can maintain a constant directory tree structure, moving individual branches along disks for more efficient use of disk space or simply for the convenience of administration.
All UNIX systems have approximately the same directory tree structure: system utilities in the / bin directory, system libraries in the / lib directory, configuration files in the / etc directory, etc. The username database is always in the / etc / passwd file.
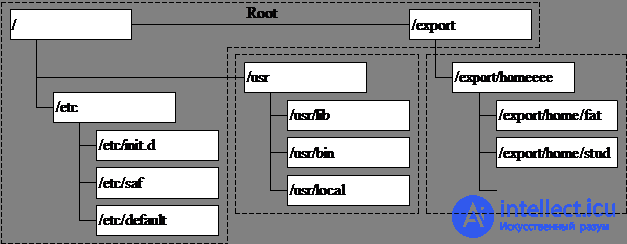
Fig. 1.1. UNIX namespace structure
The file name can consist of any ASCII character encoding characters, except for the characters '\ 000' - the system name limiter and '/' - the separator between the directory name and the file name, for example, eight carriage returns. There is no division into the name and the file extension, although the file names with the C program end with “c” and the object modules end with “.o”, the dot here is part of the name. You can create a file called “my-.2.5.pr”. In UNIX SVR3, the length of the file name is limited to 14 characters, and in BSD UNIX, Linux, SVR4 - only the length of the block on the disk, i.e. 512 bytes. The null character is considered the end of the file name in the directory.
The ability to use non-alphabetic characters in names is a simplification - from the procedures that work with names, the “validity” check has been removed
File - interpreted as a set of bytes. Unified file system (directories, devices, simple files, hard, flexible links, feeds).
UNIX Shell A specific command line interface. Launch shell - the appearance on the screen prompts. After entering the command line, the shell extracts the first word from it and looks for a file with that name, if it is found, it launches. At the time of the program, the shell is suspended. The end of the program is again an invitation and waiting for the next line to be entered. The shell is a regular user program — all it needs is the ability to input from the terminal and output to the terminal, the ability to run expensive programs.
Example: cp src dest - the first argument is the name of an existing file, the program copies this file and a copy calls dest
head -20 file - the first argument tells the program to print the first 20 lines of the file instead of the 10 received.
Arguments that control the operation of a command or specify additional values are called flags or keys and are indicated by a dash. Тире требуется, чтобы избежать двусмысленности. Так, например, команда head 20 file велит напечатать программе head первые 10 символов файла 20 , а затем первые 10 строк файла file.
Символы маски – джокеры-
ls *.c
ls [ ape] *- в квадратных скобках можно указать множество символов, из которых программа должна будет выбрать один. Например, команда выше велит программе ls вывести список всех файлов, имя которых начинается с символов «а» ,«p» или «е».
Программа оболочки не должна открывать терминал, чтобы прочитать с него или вывести на него строку. Вместо него программы получают автоматический доступ к файлу, называемому стандартным устройством ввода и к файлу, называемому стандартным устройством вывода , а также к файлу standart error . По умолчанию всем трем устройствам соответствует терминал – клавиатура для ввода и экран для вывода.
Например, команда sort вызывает программу sort, читает строки с терминала, сортирует их в алфавитном порядке и выводит результат на экран.
Стандартный ввод-вывод можно перенаправить. Используются символы “<” “>”.
Например, команда
sort < in> ou t –заставляет программу sort взять в качестве входного файл in и направить вывод в файл out. Поскольку стандартный вывод сообщений об ошибках не был перенаправлен, сообщения будут печататься на экране.
Программа, считывающая данные со стандартного устройства ввода, выполняющая определенную обработку этих данных и записывающая результат в поток стандартного вывода, называется фильтром.
Пример: рассмотрим следующую командную строку, состоящую из трех отдельных команд:
sort <in> temp; head –30<temp; rm temp
Сначала запускается команда sort – принимает данные из файла in и записывает результат в файл temp.
Когда команда завершает работу, оболочка запускает программу head, веля ей распечатать первые 30 строк из файла temp на стандартном устройстве ввода-вывода. Наконец, временный файл temp удаляется.
В системе UNIX часто используются строки, в которых первая программа командной строки формирует вывод используемых второй программой в качестве входа. Более простой способ: sort < in | head для этого используется вертикальная черта, называемая символом канала . Набор команд, соединенных символов канала, называется конвейером и может содержать произвольное количество команд.
Пример четырехкомпонентного конвейера:
grep ter*.t | sort | head –20 | tail –5>foo
Здесь в стандартное устройство вывода записываются все строки, содержащие строку ter во всех файлах, оканчивающихся на t, после чего они сортируются. Первые 20 строк выбирается программой head, которая передает их программе tail, записывающей последние пять строк ( то есть строки с 16 по 20 в отсортированном списке) в файл foo.
UNIX является универсальной много задачной системой. Синтаксис оболочки для запуска фонового процесса состоит в использовании символа амперсанда в конце строки.
Пример: wc – l < a > b &
Строка запустит программу подсчета количества слов wc, которая сосчитает число строк (флаг –l) во входном файле a, запишет результат в файл b, но будет делать это в фоновом режиме. Как только команда будет введена пользователем, оболочка напечатает символ приглашения к вводу и перейдет в режим ожидания следующей команды.
Конвейеры также могут выполняться в фоновом режиме, например:
sort<| head &
Можно одновременно запустить несколько фоновых конвейеров.
Файлы, содержащие команды оболочки, называются сценариями оболочки. Сценарии оболочки могут присваивать значения переменным оболочки и затем считывать их. Могут запускаться с параметрами и использовать конструкции if, for, while, case. То есть это альтернативные программы, написанные на языке оболочки.
Программы обращаются к системным вызовам, помещая аргументы в регистры центрального процессора (или в стек), выполняя команду эмулирования прерывания для передачи управления ОС и перехода из пользовательского режима в режим ядра. На С невозможно написать команду эмулированного прерывания, этим занимаются библиотечные функции, по одной на системный вызов. Каждая такая процедура помещает аргументы в нужное место и выполняет команду эмулированного прерывания TRAP. Таким образом, чтобы обратиться к системному вызову read , программа на С должна вызвать библиотечную функцию read. В стандарте POSIX определен именно интерфейс библиотечных функций, а не интерфейс системных вызовов, там даже не упоминаются фактические системные вызовы.
Помимо ОС и библиотеки системных вызовов все версии содержат большое количество стандартных программ, некоторые описаны в стандарте POSIX 1003.2, многие могут различаться в разных версиях. К этим программам относится программный процессор (оболочка), компиляторы, редакторы, утилиты для работы с файлами.
Таким образом, три интерфейса в системе UNIX:
1) интерфейс системных вызовов;
2) интерфейс библиотечных функций;
3) интерфейс, образованный стандартным набором обслуживающих программ (который не имеет никакого отношения к системе и может быть легко заменен).
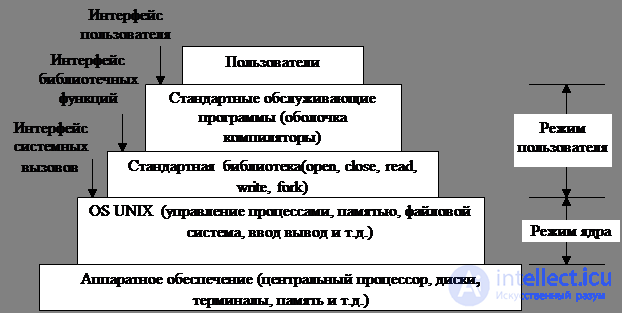
Fig. 1.2. Уровни операционной системы UNIX
Fig. 1.3. Некоторые компоненты персонального компьютера
Концептуально простой персональный компьютер, современные персоналки имеют более сложную структуру – несколько шин.
Утилиты UNIX. Пользовательский интерфейс состоит из большого числа обслуживающих программ, называемых также утилитами. Шесть категорий:
Стандарт POSIX содержит синтаксис и семантику не менее 100 таких программ (первые 3 категории). Идея стандартизации в том, чтобы писать сценарии оболочки, которые бы работали на всех системах UNIX.
Table 1.1. Примеры некоторых утилит, регламентируемых стандартом POSIX :
Program | Function |
Саt | Конкатенация нескольких файлов в стандартный выходной поток |
Сhmod | Изменение режима защиты файла |
Сp | Копирование файлов |
Сut | Вырезание колонок текста из файла |
Grep | Поиск определенной последовательности символов в файле |
Head | Extracting the first lines from a file |
Ls | Catalog listing |
Make | Compiling a file to create a binary file |
Mkdir | Creating a directory |
Od | Hex Dump File |
Paste | Insert columns of text into a file |
Pr | Formatting a file for printing |
Rm | Deleting files |
Rmdir | Deleting a directory |
Sort | Sorting file lines alphabetically |
Tail | Extracting Last Lines from File |
Tr | Convert characters from one set to another. |
6. References
1. Terence Chan Programming in C ++ for UNIX - K .: Ed. House "Williams", 200. - 694s.
2. Robachevsky A. UNIX operating system - SPb .: BHV-Petersburg, 2001. - 254с.
3. Maurizio Bach. Creating an UNIX Operating System
St. Petersburg: BHV-Petersburg, 2001. - 286s.
4. A. V. Gordeev A.Yu. Molchanov System Software - SPb .: Peter, 2001-734с.
5. Stevens U. UNIX: Interaction of processes.-SPb: Peter, 2002.-576s.: Ill.
6. Brown S. UNIX operating system .- M.: Mir, 1986. –463с.
7. Deytel G. Introduction to operating systems. In two volumes. - M.: Mir, 1987
8. Olifer N.A., Olifer V.G. Network operating systems. - SPb.: Peter, 2001
9. Dmitry Irtegov Introduction to operating systems. Textbook.- SPb: BHV-Petersburg, 2002.-624 with: Il.
10. E. Tanenbaum Modern operating systems. 2nd ed. - SPb: Peter, 2002. –1040 pp., Ill.
Comments
To leave a comment
Operating Systems and System Programming
Terms: Operating Systems and System Programming