Lecture
Transmission Control Protocol / Internet Protocol (TCP / IP) is an industry standard protocol stack designed for wide area networks.
TCP / IP standards are published in a series of documents called Request for Comment (RFC). RFCs describe the internal workings of the Internet. Some RFCs describe network services or protocols and their implementation, while others generalize application conditions. TCP / IP standards are always published as RFCs, but not all RFCs define standards.
The stack was developed at the initiative of the Department of Defense (DoD) more than 20 years ago to link the experimental ARPAnet network with other satellite networks as a set of common protocols for a heterogeneous computing environment. The ARPA network supported developers and researchers in the military fields. In the ARPA network, the connection between two computers was carried out using the Internet Protocol (IP), which is still one of the main TCP / IP stack names and appears in the stack name.
A major contribution to the development of the TCP / IP stack was made by the University of Berkeley, implementing the stack protocols in its version of UNIX OS. The widespread adoption of the UNIX operating system has also led to the widespread adoption of the IP protocol and other stack protocols. The worldwide Internet also operates on this stack, whose Internet Engineering Task Force (IETF) division makes a major contribution to the improvement of stack standards published in the form of RFC specifications.
If currently the TCP / IP stack is distributed mainly on UNIX networks, its implementation in the latest network operating systems for personal computers (Windows NT 3.5, NetWare 4.1, Windows 95) is a good prerequisite for a rapid increase in the number of TCP stack installations / Ip.
So, the leading role of the TCP / IP stack is explained by the following properties:
Since the TCP / IP stack was developed before the ISO / OSI open systems interconnection model appeared, although it also has a multi-level structure, the alignment of TCP / IP stack levels with the OSI model is rather arbitrary.
The structure of the TCP / IP protocols is shown in Figure 2.1. TCP / IP protocols are divided into 4 levels.
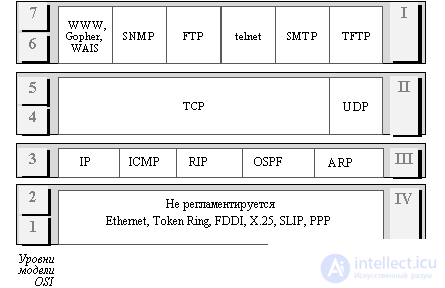
Fig. 2.1. TCP / IP stack
The lowest ( level IV ) corresponds to the physical and channel layers of the OSI model. This layer is not regulated in TCP / IP protocols, but it supports all popular standards of the physical and data link layer: Ethernet, Token Ring, FDDI, Fast Ethernet, 100VG-AnyLAN for local networks, point-to-point connection protocols for wide area networks (SLIP). and PPP, X.25 packet-switched territorial network protocols, frame relay. A special specification has also been developed, defining the use of ATM technology as a data link transport. Usually, when a new technology of local or global networks appears, it is quickly incorporated into the TCP / IP stack by developing an appropriate RFC that defines the method of encapsulating IP packets into its frames.
The next level ( level III ) is the level of interconnection, which deals with the transmission of packets using various transport technologies of local networks, territorial networks, special communication lines, etc.
The main protocol of the network layer (in terms of the OSI model) uses the IP protocol in the stack, which was originally designed as a packet transmission protocol in composite networks consisting of a large number of local networks connected by both local and global connections. Therefore, the IP protocol works well in networks with a complex topology, making rational use of the presence of subsystems in them and sparingly the throughput of low-speed communication lines. The IP protocol is a datagram protocol, that is, it does not guarantee delivery of packets to the destination node, but tries to do this.
The interworking layer also includes all protocols related to the creation and modification of routing tables, such as the RIP (Routing Internet Protocol) and Open Shortest Path First protocols for collecting routing information, as well as the Internet Control Message Protocol ( ICMP ) ). The latter protocol is designed to exchange error information between the routers of the network and the source node of the packet. With the help of special ICMP packets, it is reported that the package cannot be delivered, the lifetime or duration of the packet assembly from fragments is exceeded, anomalous parameter values, a change in the forwarding route and type of service, system status, etc. are reported.
The next level ( level II ) is called the main level . At this level, the Transmission Control Protocol ( TCP ) and User Datagram Protocol ( UDP ) datagrams function. TCP provides reliable messaging between remote application processes by creating virtual connections. The UDP protocol provides the transmission of application packets in a datagram manner, like IP, and performs only the functions of a link between the network protocol and numerous application processes.
The upper level ( level I ) is called applied. For many years of use in the networks of various countries and organizations, the TCP / IP stack has accumulated a large number of application-level protocols and services. These include such widely used protocols as FTP file copy protocol, terminal telnet emulation protocol, SMTP mail protocol used in Internet e-mail, hypertext services for accessing remote information, such as WWW and many others. Let us dwell in some detail on some of them.
File Transfer Protocol FTP (File Transfer Protocol) implements remote file access. In order to ensure reliable transmission, FTP uses a connection protocol, TCP, as its transport. In addition to file transfer, the FTP protocol offers other services. So, the user is given the opportunity to work interactively with a remote machine, for example, he can print the contents of its directories. Finally, FTP authenticates users. Before accessing the file, in accordance with the protocol, users must provide their name and password. To access the public FTP directories of Internet archives, password authentication is not required, and it is bypassed by using the predefined username Anonymous for such access.
In the TCP / IP stack, the FTP protocol offers the most comprehensive set of services for working with files, but it is also the most difficult to program. Applications that do not require all the features of FTP can use a different, more economical protocol — the simplest protocol is the Trivial File Transfer Protocol ( TFTP ). This protocol implements only the transfer of files, and as a transport, a connectionless protocol, simpler than TCP, is used - UDP.
The telnet protocol provides a stream of bytes between processes, as well as between a process and a terminal. Most often, this protocol is used to emulate a remote computer terminal. When using the telnet service, the user actually controls the remote computer in the same way as the local user, so this type of access requires good protection. Therefore, telnet servers always use at least password authentication, and sometimes more powerful security features, such as Kerberos.
Simple Network Management Protocol ( SNMP ) is used for network management. Originally, SNMP was designed to remotely monitor and control Internet routers, which are traditionally also commonly referred to as gateways. With the growing popularity, the SNMP protocol was also used to control any communication equipment — hubs, bridges, network adapters, etc. etc. The management problem in the SNMP protocol is divided into two tasks.
The first task is related to the transfer of information. The control information transfer protocols define the procedure for interaction between the SNMP agent running in the managed equipment and the SNMP monitor running on the administrator's computer, which is often also called the management console. Transmission protocols define the message formats exchanged between agents and the monitor.
The second task is related to controlled variables characterizing the state of the controlled device. Standards regulate what data should be stored and accumulated in devices, the names of these data and the syntax of these names. The SNMP standard defines a network management information database specification. This specification, known as the Management Information Base (MIB) database, defines the data elements that the managed device must store, and the valid operations on them.
Comments
To leave a comment
Computer networks
Terms: Computer networks