Lecture
The network layer must first provide the means to solve the following tasks:
Traffic in the network is formed randomly, but it also reflects some patterns. As a rule, some users working on a common task (for example, employees of one department) often contact each other or a common server, and only sometimes they feel the need to access computer resources of another department. It is desirable that the network structure matches the structure of information flows. Depending on network traffic, computers on a network can be divided into groups (network segments). Computers unite in group if the most part of the messages generated by them, is addressed to computers of the same group.
Bridges and switches are used to divide the network into segments. They screen local traffic within a segment, not sending any frame outside of it, except for those addressed to computers located in other segments. Thus, the network falls into separate subnets. This allows you to more efficiently select the bandwidth of the existing communication lines, taking into account the intensity of traffic within each group, as well as the activity of data exchange between groups.
However, traffic localization by means of bridges and switches has significant limitations.
On the one hand, the logical network segments located between the bridges are not sufficiently isolated from each other, namely, they are not protected from so-called broadcast storms. If a station sends a broadcast message, then this message is transmitted to all stations of all logical network segments. Protection against broadcast storms in networks built on the basis of bridges is quantitative, not qualitative, the administrator simply limits the number of broadcast packets that a node is allowed to generate.
On the other hand, the use of a virtual segment mechanism implemented in local area network switches leads to a complete localization of traffic — such segments are completely isolated from each other, even with respect to broadcast frames. Therefore, in networks built only on bridges and switches, computers belonging to different virtual segments do not form a single network.
These drawbacks of bridges and switches are related to the fact that they work on data link layer protocols, which explicitly do not define the concept of a part of a network (or a subnet or segment) that could be used to structure a large network. Instead of improving the data link layer, the developers of network technologies decided to entrust the task of building a composite network to a new level - the network one.
Modern computing networks are often built using several different underlying technologies — Ethernet, Token Ring, or FDDI. Such heterogeneity arises either when combining already existing networks that use various data link layer protocols in their transport subsystems, or when moving to new technologies, such as Fast Ethernet or 100VG-AnyLAN.
It is for the formation of a unified transport system that combines several networks with different principles of information transfer between end nodes, and serves as the network level. When two or more networks organize a joint transport service, this mode of interaction is usually called internetworking . The term internet ( internetwork or internet) is also often used to denote a composite network in English literature .
The creation of a complex structured network integrating various basic technologies can also be carried out by means of the data link layer: for this, some types of bridges and switches can be used. However, not all types of bridges and switches have the ability to transmit data link layer protocols, besides these possibilities are limited. In particular, the maximum size of data fields in frames must coincide in the networks to be merged, since channel protocols, as a rule, do not support packet fragmentation functions.
Among the data link layer protocols, some provide data delivery in networks with an arbitrary topology, but only between a pair of neighboring nodes (for example, PPP) and some between any nodes (for example, Ethernet), but the network must have a specific and very simple topology type, for example, tree.
When several segments are networked using mots or switches, restrictions on its topology continue to apply: there should be no loops in the resulting network. Indeed, a bridge or its functional counterpart — a switch — can solve the task of delivering a packet to a destination only when there is a single path between the sender and the receiver. At the same time, the presence of redundant links, which form loops, is often necessary for better load balancing, as well as for improving the reliability of the network due to the existence of an alternative route in addition to the main one.
The network layer allows you to transfer data between any, arbitrarily connected network nodes.
The implementation of the network layer protocol implies the presence of a special device in the network - a router . Routers integrate individual networks into a single composite network (Figure 1.1). The internal structure of each network is not shown, as it does not matter when considering the network protocol. Multiple networks can be connected to each router (at least two).
In complex composite networks, there are almost always several alternative routes for packet transmission between two end nodes. The task of choosing routes from several possible is solved by routers as well as end nodes.
A route is a sequence of routers that a packet must pass from the sender to the destination.
The router selects a route based on its understanding of the current network configuration and the corresponding route selection criteria. Usually, the criterion is the time of the route, which in local networks is the same as the length of the route, measured in the number of routing nodes passed (in global networks, the time of packet transmission on each communication line is also taken into account).
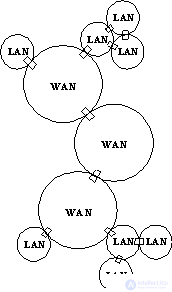
Fig. 1.1. Composite Network Architecture
In the OSI model, also called the Open Systems Interconnection (OSI) model and developed by the International Organization for Standardization (ISO), the network interaction tools are divided into seven levels, for which standard names and functions are defined.
The network layer occupies an intermediate position in the OSI model: application, session, and presentation protocols access its services. To perform its functions, the network layer calls the functions of the data link layer, which in turn refers to the means of the physical layer.
Consider briefly the basic functions of the levels of the OSI model.
The physical layer transmits bits over physical channels, such as coax, twisted pair, or fiber optic cable. At this level, the characteristics of the physical media and electrical signal parameters are determined.
The link layer provides data frame transmission between any nodes in networks with a typical topology or between two neighboring nodes in networks with an arbitrary topology. The data link layer protocols contain a certain structure of communications between computers and ways of their addressing. The addresses used at the data link layer in local networks are often called MAC addresses.
Network layer provides data delivery between any two nodes in a network with an arbitrary topology, while it does not assume any obligations for the reliability of data transmission.
Transport level provides data transfer between any network nodes with the required level of reliability. For this purpose, at the transport level there are facilities for establishing a connection, numbering, buffering, and ordering packets.
The session layer provides dialogue management tools that allow you to record which of the interacting parties is currently active, and also provides synchronization tools as part of the messaging procedure.
Presentation level Unlike the underlying layers, which deal with reliable and efficient transmission of bits from the sender to the receiver, the presentation layer deals with the external presentation of the data. At this level, various types of data transformation can be performed, such as compression and decompression, encryption and decryption of data.
The application layer is essentially a collection of a variety of network services provided to end users and applications. Examples of such services are, for example, e-mail, file transfer, connection of remote terminals to a computer over a network.
When constructing the transport subsystem, the functions of the physical, link and network layers, which are closely related to the equipment used in this network: network adapters, hubs, bridges, switches, routers, are of the greatest interest. The functions of the application and session layers as well as the presentation layer are implemented by the operating systems and system applications of the end nodes. The transport layer mediates between these two groups of protocols.
The data link layer protocols do not allow building networks with a developed structure, for example, networks that combine several enterprise networks into a single network, or highly reliable networks in which there are redundant connections between nodes. In order, on the one hand, to preserve the simplicity of the packet transfer procedures for typical topologies, and on the other hand, to allow the use of arbitrary topologies, an additional network layer is introduced.
Before we begin to consider the functions of the network layer, we clarify what is meant by the term "network". In the network layer protocols, the term "network" means a set of computers interconnected according to one of the standard generic topologies and using a common basic network technology for packet transmission. Within the network, the segments are not separated by routers, otherwise it would not be one network, but several networks. The router will connect several networks to the internetwork.
The basic idea of introducing a network layer is to leave the technologies used in the networks being merged intact, but to add additional information to the link layer frames — the network layer header , which could be used to find a destination on a network with any basic technology. The header of the network layer packet has a unified format that does not depend on the formats of the data link layer of those networks that may be included in the unified network.
The header of the network layer must contain the destination address and other information necessary for successful transfer of a packet from one type of network to another type of network. Such information may include, for example:
As the sender and recipient addresses in a composite network, not the MAC address is used, but a pair of numbers — the network number and the computer number on the network. In channel protocols, the "network number" field is usually absent - it is assumed that all nodes belong to the same network. Explicit network numbering allows network layer protocols to create an exact map of interconnections and choose rational routes for any of their topologies, using alternative routes, if they exist, that they do not know how to make bridges.
Thus, within the network, message delivery is regulated by the data link layer. But the delivery of packets between networks deals with the network layer.
There are two approaches to assigning a node number in a network packet header. The first is based on the use for each node of a new address that is different from that used on the data link layer. The advantage of this approach is its versatility and flexibility - whatever the address format at the data link layer, the node address format at the network level is chosen to be uniform. However, there are some inconveniences associated with the need to re-number the nodes, and most often manually.
The second approach is to use at the network level the same node address that was given to it at the channel level. This saves the administrator from additional work on the assignment of new addresses, eliminates the need to match the network and channel addresses of the same node, but can create the difficult task of interpreting the node address when connecting networks with different address formats.
In order to have information about the current network configuration, routers exchange routing information with each other using a special protocol. Protocols of this type are called routing information exchange protocols (or routing protocols). The routing information exchange protocols should be distinguished from, actually, the network layer protocols . While the former carry purely proprietary information, the latter are intended for transmitting user data, just as the data link layer protocols do.
In order to deliver a packet of the routing information exchange protocol to a remote router, the network layer protocol is used, since only it can transfer information between routers located in different networks. The packet of the routing information exchange protocol is placed in the data field of the network layer packet, therefore, from the point of view of packet nesting, routing protocols should be attributed to a higher level than the network one. But functionally, they solve a common problem with network-level packets — delivering frames to a destination through a heterogeneous composite network.
Using routing information exchange protocols, routers compile a varying degree of interconnection map details and decide on which next router to transmit a packet to form a rational path.
At the network level, one more type of protocols works that are responsible for mapping the address of the node used at the network level to the local network address. Such protocols are often called address resolution protocols - Address Resolution Protocol, ARP. Sometimes they are referred not to the network level, but to the channel level, although the subtleties of the classification do not change their essence.
Comments
To leave a comment
Computer networks
Terms: Computer networks