Lecture
Feedback engineering ( reverse engineering , reverse engineering ; eng. Engineering ) is the study of some finished device or program, as well as documentation for it in order to understand the principle of its operation; for example, to detect undocumented features (including software bookmarks), make changes or reproduce a device, program or other object with similar functions, but without direct copying.
It is usually used if the creator of the original object did not provide information on the structure and method of creation (production) of the object. The copyright holders of such objects may declare that carrying out a reverse development or using its results violates their exclusive right under copyright law and patent legislation [1] [2].
Russia
USA
European Union
In the European Union, relations in the field of intellectual property protection are governed by certain directives. In the field of copyright, the processes of unification and harmonization are primarily associated with the legal protection of copyright and related rights, computer programs and databases.
In 2016, at the meeting of the Governmental Commission on Import Substitution, the Minister of Industry and Commerce of the Russian Federation D.V. Manturov announced plans to create a reverse engineering center on the basis of the Industry Development Fund [6].
Copying various mechanisms and machines without actual development. It allows minimal cost to reproduce a good design, but there are cases of copying and unsuccessful machines.
Examples:
The reverse development of electronic devices appeared at the dawn of radio engineering. In 1920-1930, various companies copied radio tubes and circuit solutions for their use from each other. It is with reverse engineering, and not with licensed production, that the radio tubes of the same purpose for almost all manufacturers turned out to be unified and interchangeable. For example, the European lamp EL95 is a clone of an earlier American lamp 6KA5. There are also opposite examples: American 6CA5 and KT88 - clones of the European EL34 lamp. The same applies to the Soviet radio tubes, many of which are clones of American lamps obtained under lend-lease (for example, 6F4, 6P9) or German ones from captured equipment (6Г2, ГУ50).
Research and reverse engineering of programs are usually carried out for the purpose of further modification, copying, or, for example, writing key generators, whose operation algorithm is obtained on the basis of an analysis of their verification algorithm. The study of programs is also used in order to obtain some confidential information about the program’s internal device — about a network communication protocol with a server, hardware, a security key, or about interaction with another program. Another area of application is obtaining information on the ways of exporting data from numerous proprietary file formats [8].
With the development of the Internet, popular operating systems and programs are increasingly being investigated for vulnerabilities or so-called vulnerabilities. "Holes". Later found holes can be used to obtain unauthorized access to a remote computer or computer network. On the other hand, reverse engineering is used in the study of malware by antivirus companies in order to add its signatures to their product databases.
One of the well-known examples of reverse engineering is the study of the BIOS of an IBM personal computer, which has become a serious step towards the development of production of IBM-compatible computers by third-party manufacturers. [9] [10] Creating a Samba server [11] [12] [13] [14] [15] (part of the GNU / Linux OS and working with servers based on Windows OS) also required the reverse development of the SMB protocol used by Microsoft. The creation of many ICQ clients also required the reverse development of the ICQ protocol. [ Source not specified 2908 days ]
Reverse software development is performed using the following techniques.
Currently, the words "reverse engineering" is most often understood to be so-called. clean room reverse engineering, that is, the process by which one group of developers analyzes the machine code of a program, makes up the algorithm of this program in pseudo-code or, if the program is a driver of a device, makes up the exhaustive specifications of the device of interest. After receiving the specifications, another development team writes its own driver based on the specifications or algorithms received. This approach allows you to avoid accusations of copyright infringement on the original program, as the laws, for example in the United States, fall under the concept of "fair use", that is, the fair use of the original program. The result of the reverse development is rarely identical to the original, which makes it possible to avoid responsibility under the law, especially if the first group of developers controls the absence of this identity and there is no violation of trademarks and patents.
Database
Can be used when creating a relational database model.
Backward development of a competitor's product in order to find out its structure, principle of operation and evaluate the possibilities of creating an analogue.
For example, a number of manufacturers of photographic equipment, such as Sigma, Tamron, Tokina and Carl Zeiss, produce lenses with Canon EF mount. They were created by reverse engineering, and their manufacturers do not have access to Canon specifications [ source not specified 67 days ].
Jerry cans
The most well-known facts of reverse engineering during the Second World War were:
Software Reverse - restoring the principles / ideas / algorithms of the program for researching and / or creating similar software. Often used for:
Hacking software should not be confused with its reversing: for hacking, it is enough to disassemble the principle of the licensing check, and reversing is a complete analysis of the program by building blocks and unfolding your brain according to the level of kosher.
For a successful code encoding, you need to know the assembler, have a general idea of cryptography, know the Munspeak and the theory of probability - wasn’t your predecessor? Well, matan - for example, graph theory for branch analysis. But you can not know, the main thing - to be able to quickly find what to read, and quickly understand.

Reverse engineering device
Iron reversal - any control units of washing machines, Subaru Impreza, cash registers. Usually used for:
Any developer and manufacturer has its own failure analysis laboratory for real chip reversing. For example, a photo report about the Atmel laboratory.
In that country, it was decided to abandon the development of its own chips in general from hopelessness . Kopipizding IC topology was put on a grand scale.
A disassembler is a utility that converts a binary code into an assembler listing. In the simplest cases, this is quite enough, and it remains to smoke a little and find what you need. In the worst - this is porridge, and without scripts and / or debugger can not do.
Hiew ( Hacker's viewer ). A small utility, useless for normal people, is used only by overdue specialists, sometimes by advanced users (like a hex editor). For a long time there has been a bunch of GUI-shnyh tools for the same purposes, but according to the glorious tradition they continue to use tools ...
Sourcer from V Communications. The old powerful disassembler of DOS times and earlier versions of Windows. Allowed from .COM or .EXE files to get directly .ASM file, and for various assembler compilers, such as TASM or MASM. If a sufficient number of passes were given when disassembling, then with a high degree of probability it was possible to get the original executable byte-by-byte program when compiling the newly created .ASM file. Delivered with good comments in the listing, speed, support for different types of processor and, of course, old-school interface. Now it is not relevant, although some Anonymus continue to keep it in their tools, for example, to disassemble the MBR of a hard disk, Boot-sector, special utilities loaded from a diskette without any OS (for example, BIOS flashing utilities or utilities from HDD manufacturers), and other things. That is, for low-system needs. The latest version was v8.01 from 2001. Sourcer - remember, love, mourn!
Without these things, you will never know that the Nippon-Denso NP648976 processor is actually a pathetic Motorola 6803 clone with a 16K ROM on board. And when you find out, you will understand that the Japs never invented anything themselves, but only skillfully fucked up.
A debugger is a program for the controlled execution of a program or, in general, any arbitrary piece of code, up to a DLL injected into another process. An advanced debugger can use debugging hardware, and, of course, disassemble.
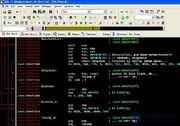
Matrix got you. Code analysis in IDA.
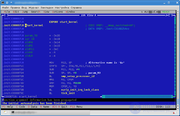
IDA in Linux or Linux in IDA?
IDA
Основной дизассемблер на сегодняшний день. Обладает множеством функций типа поддержки скриптов, графического режима или встроенных плагинов вплоть до эмулятора x86. Не тупой интерфейс — множество интуитивно понятных «горячих» клавиш и т. п. Проекту уже лет 15, и он единственный из дизассемблеров живёт активной жизнью и поныне: у других в новых версиях фичи почти не родятся. До сих пор таскает с собой DOS-GUI версию для олдфагов. Также известен нефиговой ценовой политикой.
Пишет его татарский расовый мудак по имени Ильфак Гуильфанов. Детали истории создания дизассемблера покрыты мраком, но известно, что Ильфаку, как и Биллу Гейтсу с DOS, добрые люди помогли написать первые версии. И задумывался он как инструмент для восстановления прошивок HDD. Дальше, непонятно как и почему, люди разошлись, и остался он один. Потом Ильфак всплывает с версией 3.x уже от лица фирмы Datarescue, которая купила проект. Начиная с версии 4.0, у него появляется GUI, написанный на BCB! С этого времени продукт начинает приобретать массовую известность в узких кругах по двум причинам:
Остановимся на втором пункте подробнее.
Ильфак, будучи на данном рынке монополистом, давно забил на пользователей член. Потому что берут и так. Любой юзер IDA, которому приходилось иметь дело с поддержкой, получал кучу отрицательных эмоций: получив продукт с кучей багов, вы предоставлены себе в их исправлении. Ошибки исправлять никто не спешит — можно легко прождать полгода, даже если баг вопиющий. Продукт практически не тестировался перед релизами и не тестится до сих пор. Юзеры IDA вынуждены хранить несколько версий, потому что в одной хорошо работает одна фича, в другой — другая, в третьей — третья.
А среди «неофициальных» юзеров Ильфак нелюбим за то, что без спроса берёт идеи. За счёт того, что IDA поставляется с SDK, юзеры могут делать свои плагины к IDA, и таки делают немало. Плагины пишутся как для того, чтобы исправить баги оригинальной функциональности, так и ради добавления своих фич для решения конкретных задач. Уровень альтруизма среди «неофициальных» юзеров высок, и исходники плагинов выкладываются на всеобщее обозрение. Так вот, примерно через полгода после появления полезных исходников это становится фичей IDA. У Ильфака на этот счёт железное алиби: «То, что тут придумали — это не новая идея, это меня пользователи попросили ещё год назад».
Вначале народная ненависть выливалась в троллинг на форуме официального русского сайта. Но потом всё быстро утихло, ибо Ильфак анально отгородил форум официальных юзеров, а с неофициальными общаться перестал. Посему примерно раз в год то китайцы, то албанцы, то русские (был интересный случай, когда народ скидывался на руборде, чтобы купить одну копию и поделиться), то немцы тырят с тренингов, кардят, хачат сервера с IDA и коммуниздят очередную версию. Чем каждый раз нереально доставляют целевой аудитории IDA. А официальные юзеры потом смотрят в закрытые форумы поддержки и скидывают цитаты баттхёрта Ильфака в публику, повышая градус веселья.
Потом Ильфак свалил с Datarescue и стал делать IDA от лица своей конторы Hex-Rays. Ходят слухи, что он нанял наконец программеров с прямыми руками, которые наконец начали чистить его говнокод. Поэтому версия 5.5 была воспринята с одобрением, и некоторые неофициальные пользователи даже начали помышлять о приобретении. Но эйфория продлилась недолго, баги снова были найдены, и всё вернулось на круги своя.
Ознакомиться с историей спионеривания можно тут. В июле 2011 года у антивирусной компании была упёрта полная версия декомпилятора версии 6.1. TEH DRAMA!
SoftIce
Прошлый desktop-тред в бамплимите, начинаем новый…
Дебаггер, работающий на нулевом уровне, на котором можно всё. Появляется по нажатию CTRL+D, и всё остальное — программы, драйвера и даже некоторые прерывания перестают работать. Переставало идти даже «время», и задебажившийся индивид мог потом реально фалломорфировать, осознав сколько прошло времени в «реальном мире». Заодно обрубалась модемная связь, вызывая лютый багет от забытого брейкпоинта при ночном дозвоне по дайлапу. Можно трассировать что угодно: драйвер HDD, USB-антенны и т. п. А ещё там работает мышь и можно делать скрины.
SoftIce вышел на рынок как отладчик уровня ядра совершенно неожиданно для самих создателей этого ядра — MS. Позиционировался как тулза «для нахождения багов в софте», но последние весьма разнообразны: сюда можно отнести MS Office, требующий ключ активации. Немаловажное преимущество: он умеет считывать при загрузке инфу о библиотеке, в процессе отладки показывая имена, например, Kernel.FindClose+105h.
Нынче похож на свежий навоз: его уже n лет никто не обновляет. И не будет — в связи с выпилом конторы разработчиков: Numega невозбранно была проебана за 30 сребреников мудацкой Compuware. В итоге всё закончилось тотальным выпилом как нумеговских проектов, так и собственно офиса бывшей Нумеги. А остатки Девпартнера отдали какому-то ебучему реселлеру Microfocus, потому что Compuware после тотального экстерминатуса Нумеги забил на все эти ваши девпартнеры-девшмартеры болт.
Radare2
A whole framework for reverse engineering. Initially, the hex editor includes a disassembler, a decompiler ... See for yourself. Cross-platform, with several interfaces to choose from, and its source code is open. Nya
Rest
WinDbg - as if bydlokodery, suffering from the word "Microsoft" burning in the anus, it was not insulting, this is the most popular kernel-mode debugger since the death of SoftIce. And in user-mode, Vinbag provides fierce wines, putting a bolt on these your Debugging API and allowing, for example, a peek into the native code for a process that already has a debugger for a managed code.
Syser is a Chinese kernel debugger with GUI. Came to replace SoftIce, turned down in 2011, losing the war to new 64-bit kernels.
OllyDbg - a third-level debugger, guishny, cute, functional above the roof, applicable for 95% of programs, and patched with pens and for all 98%. But due to the fact that r3 among professionals is considered not a tru-tulzy, suitable for scripts rather than for analyzing something really complicated, the author has put a dick on him, and now the debugger is developing new craftsmen, pathetically naming OllyDbg 2.0. [Domestic development http://www.ollydbg.de], although less well known than SoftIce, is completely kosher and free of charge. The releases look bad, but the guys are obviously gaining experience and are going in the right direction.
Modern programming languages such as Java, C # and other .NET'a do not require the use of disassemblers and debuggers for their own hacking. The entire source code can be easily obtained in a matter of seconds, and if the coder is a sucker and did not even apply obfuscation, then the received source codes from the author’s will differ, perhaps, by the absence of comments in the first. However, for ordinary binary binaries there are decompilers, though, half-dead and little usable. Who cares, look here and here.
.NET Reflector is a good tool for decompiling programs in C # and some other languages. The authors are constantly refining their offspring, and soon they promise to decompile other major languages. It was initially free, but after the appearance of a wide audience it became paid, however, Reflector was used to crack the paid version.
dotPeek is the brainchild of the infamous JetBrains, which by the time it was released from alpha became a useful tool that could compete with industry leaders. Decompiles an obfuscated lapshchik, before which even the famous and beloved .NET Reflector passes. Oh yeah, the program comes absolutely free.
ILSpy is a free analog reflector from SharpDevelop developers. It is quite usable, but stopped in development - all people throw at the new version of SharpDevelop.
JD, JavaDec, JavaByte, Cavaj, thousands of them ... are decompilers for Toad. The toolkit here is much richer than for C #, but the actual hit tools are not observed. However, it makes sense to purr (open libraries: so, the free idea9 community edition plus this and this may well help in the decompilation of a commercial bydlokod.
DeDe Full: Decompiler for Delphi programs of any version.
Often the code is obfuscated. Deobfuscators often help. For interpreted languages (with the exception of perl), they are usually not required or self-written.
For JavaScript - JSBeautifier.
For sharpe, one of the best is de4dot.
PETools - a tool of a certain NeoX (a yodmen is a person who poured iodine on dick). Suitable for use with PE-format. Competitor - LordPE (able to fix SizeOfImage in peb), the rest of this series - UG.
RSATool is a GUI program for pumping a skill using RSA. The author is an egoist from TMG (a scene, not a single nuke). For factorization is not suitable, it is better to use msieve.
To combat reversing, the authors use all sorts of tricks so that their creations are not available for analysis. The higher the greed and crap functionality, the more paranoid protection is usually, which in clinical cases may even begin to take revenge (delete files, etc.) if it feels that someone with a debugger is approaching her ass. Interestingly, the buggy protection can work where there is no cracking smell, and then a simple user can pizdets.
Advanced programs rarely contain paranoia, for example, WinRar.
HD Surprisingly, bydloprogs often have natural protection against analysis. Let's say a project on Visual Basic compiled into a P-code is much more difficult to read than a product of a full-fledged C programmer. Also the complexity is the Hindu programming style - bydlokoder clumsily trying to protect his creation by artificially blowing up the code, although without any elaboration it can be such HEX that even having the original source, you can understand how it works - reading such a listing can cause vomiting.
Zen coding - the use of the intricacies of design patterns and code generation in general is very “smart” by a programmer that leads to the creation of a no less disgusting code, which is fucked up in the samples.
Packers compress programs to take up less disk space and unpack in memory. Per se are not protected, but it is impossible to analyze a compressed program in its unpacked form. For well-known packers, it is best to find an unpacker that will return the program to a more or less initial state. Famous - UPX, ASPack, MEW, PECompact, NSPack.
Obfuscation - the transformation of the original / intermediate / final (underline the necessary) executable code into a mess that can not be read. From the original instruction, the obfuscator does five (or even a hundred, in the case of paranoia permutation), doing the same thing as one, plus another 200, which do nothing at all, and 28 that prevent emulation or debugging. It is used both in “good” programs to transfer the appearance of a crack, and in “bad” ones, such as polymorphic viruses, which are trying to delay the moment of their detection - each next copy will be different from the previous one. Olso is trying to use in a type of Malvar and other, in the hope that anti-virus vendors will suck dick. By the way, there is such a site http://www.ioccc.org, where competitions are held for the most confusing program for UNIX. Winners of the competition are true masterpieces of code writing and code matching. Strongly recommended for review.
Anti - debugging - techniques to combat debugging. For melkosoftovskogo is enough IsDebuggerPresent (). For example, it is sad to see the BeingDebugged field in peb, or to see the value of NtGlobalFlag. These are the 2 most govnometods, or prefer to fuck with rdtsc (multiprocessor systems suck my cock), nuclear layers and physical memory parsing. For each such reception there is an anti-reception, and so on. And usually it is fiercely, furiously buggy, bsodit, and in general, normal chelas do not debug every kind of huit on their computers, but make emulators choke on this stool: Virtual Box, VMWare, VirtualPC, etc.
Stolen pieces - a part of the program code is cut, and the execution of the original piece is taken out: in protector, on a remote server, dongle, and so on. When a hacker does a dump, he does not receive the entire program, but only a part of it. A kosher example of the implementation of this method are RSA SecurID tokens.
Virtual machines - a part of the program code is transmitted to the bytecodes of another (not necessarily real) processor, and a translator is added, which these bytecodes are hacked and executed. Some protectors, such as Temida, turn one gram of the original bydlokod into 1-3 tens of kilos of new shit.
Protectors - programs that will protect your creation, especially without forcing you to think - know sit and throw molds in debildere. Thinstaller, RCrypt, ASProtect, EXECryptor (hi Relayer), WL / Themida ... a lot of them. They may contain all of the above items in an unlimited amount and in the most incredible combinations, but usually contain bugs in PRNG / metamorphs and other hits of the huits. By the way, most of the most famous prots have already moved into another world — they could not stand the competition with the pirates!
Appeals to hackers inside the executable file in the form of ASCII strings - and this happens often! Starting from “evil uncles of the hakira, do not lamayte please the program, there is no money for beer” ® to any “yates stilL Here kinda Ooooh” and whole jokes about the snail in serious defenses. Acting on hacker-lobakerov stronger than all of the above methods, forcing the latter to choke on laughter, thereby delaying the date of the inevitable hacking.
Evening. Bus. Rides. Two sit on the first seat. They have coefficients. intelligence IQ = 180: - I read Hamlet in the original yesterday ... Such aesthetic pleasure ... On the other seat two more people sit. They have IQ = 140: - I looked at the Andalusian Dog yesterday and found a correlate with Picasso's early paintings ... There are two sitting on the other seat. They have IQ = 100: - My friend and I had watched "From Dusk Till Dawn" an hour ago. How does a chick say chick that ... On the other seat are two others. They have IQ = 80: - Hey, brother! Do you remember how drunk we drank in Mercea when some kind of legs were .. the guys stuck out in the window ... And on the back platform there are two with IQ = 40: - Well, I open the program with your debugger ...
Comments
To leave a comment
Cryptanalysis, Types of Vulnerability and Information Protection
Terms: Cryptanalysis, Types of Vulnerability and Information Protection